TS: Windows 7, Configuring v36.0
Question 1
Your company has an internal Web site that requires HTTPS. The Web site's certificate is self-signed. You have a computer that runs Windows 7 and Windows Internet Explorer 8.
You use HTTPS to browse to the Web site and receive the following warning message.
There is a problem with this website's security certificate.
You need to prevent the warning message from appearing when you access the Web site.
What should you do?
- A. From Internet Explorer, enable InPrivate Browsing.
- B. From Internet Explorer, add the Web site to the Trusted sites zone.
- C. From Certificate Manager, import the Web sites certificate into your Personal store.
- D. From Certificate Manager, import the Web sites certificate into your Trusted Root Certification Authorities store.
Answer : D
Explanation:
Certificate Manager -
A certificate manager can approve certificate enrollment and revocation requests, issue certificates, and manage certificates. This role can be configured by assigning a user or group the Issue and Manage Certificatespermission. When you assign this permission to a user or group, you can further refine their ability to manage certificates by group and by certificate template. For example, you might want to implement a restriction that they can only approve requests or revoke smart card logon certificates for users in a certain office or organizational unit that is the basis for a security group.Importing CertificatesYou may restore certificates and the corresponding private keys from a file.
6. Right-click the certificate store you want to import, and click Install PFX on the context menu.
7. The Certificate Import Wizard launches. Click Next.
8. In the File name text box, type the name of the certificate file that you want to import.
Alternatively, you can find the file by clicking Browse.
9. Click Next. If the file specified is a Personal Information ExchangePKCS #12 (*.pfx), you will be prompted for the password. Enter the password to import the file. Click Next.
10. On the next page, select where you'd like to store the certificate. Click Next.
11. The next wizard page contains summary information about the file that you are importing. Click Finish to import the file. The certificate(s) are now ready for use by the system.
Question 2
You are installing Windows 7 on from the desktop of a Windows XP Professional PC.
Which of the following can be performed from the Windows 7 DVD? Choose three.
- A. Run setup.exe from the DVD to start the Windows 7 installation.
- B. Use the autorun feature on the DVD to start the installation.
- C. Perform a full installation of Windows 7.
- D. Perform and upgrade of Windows 7 keeping all the Windows XP settings.
Answer : ABC
Question 3
In Windows 7 you can control when users such as kids can login to Windows 7.
Which of the following best describes where to configure this option?
- A. You cannot choose this feature unless you are connected to a domain.
- B. Go to the Start, Control Panel, User Accounts and Family Safety, Setup Parental Controls, and then choose Time Restrictions.
- C. Go to Start, Control Panel. User Profiles, and then Time Restriction Settings.
- D. Go to the Homegroup settings and choose Offline Time Settings.
Answer : B
Question 4
You have a computer that runs Windows Vista. The computer contains a custom application.
You need to export the user state and the settings of the custom application.
What should you do?
- A. Run Loadstate.exe and specify the /config parameter.
- B. Run Scanstate.exe and specify the /genconfig parameter.
- C. Modify the miguser.xml file. Run Loadstate.exe and specify the /ui parameter.
- D. Modify the migapp.xml file. Run Scanstate.exe and specify the /i parameter.
Answer : D
Explanation:
MigApp.xml This file contains rules about migrating application settings. These include
Accessibility settings, dial-up connections, favorites, folder options, fonts, group membership, Open Database Connectivity (ODBC) settings, Microsoft Office Outlook
Express mailbox files, mouse and keyboard settings, phone and modem options, Remote
Access Service (RAS) connection phone book files, regional options, remote access, screensaver settings, taskbar settings, and wallpaper settings.(Include) /i:[Path\]FileName
Specifies an .xml file that contains rules that define what user, application or system state to migrate. You can specify this option multiple times to include all of your .xml files
(MigApp.xml, MigUser.xml and any custom .xml files that you create). Path can be either a relative or full path. If you do not specify the Path variable, then FileName must be located in the current directory.NOT MigUser.xmlMigUser.xml This file contains rules about user profiles and user data. The default settings for this file migrate all data in My Documents,
My Video, My Music, My Pictures, desktop files, Start Menu, Quick Launch settings, favorites, Shared Documents, Shared Video, Shared Music, Shared desktop files, Shared
Pictures, Shared Start menu, and Shared Favorites. This file also contains rules that ensure that all the following file types are migrated from fixed volumes: .qdf, .qsd, .qel,
.qph, .doc, .dot, .rtf, .mcw, .wps, .scd, .wri, .wpd, .xl*, .csv, .iqy, . dqy, .oqy, .rqy, .wk*, .wq1,
.slk, .dif, .ppt*, .pps*, .pot*, .sh3, .ch3, .pre, .ppa, .txt, .pst, .one*, .mpp, .vsd, .vl*, .or6,
.accdb, .mdb, .pub, .xla, .xlb and .xls. The asterisk ( *) represents zero or more characters.
Question 5
Your network has a main office and a branch office.
The branch office has five client computers that run Windows 7. All client computers are configured to use BranchCache.
At the branch office, a computer named Computer1 is experiencing performance issues.
You need to temporarily prevent all computers from retrieving cached content from
Computer1.
What should you do on Computer1?
- A. At the command prompt, run Netsh branchcache flush.
- B. At the command prompt, run Netsh branchcache dump.
- C. Modify the Configure BranchCache for network files Group Policy setting.
- D. Modify the Set percentage of disk space used for client computer cache Group Policy setting.
Answer : A
Explanation:
Flush -
Deletes the contents of the local BranchCache cache.
Question 6
You plan to install Windows 7 by using a Windows 7 DVD.
You need to perform an automated installation of Windows 7.
What should you do?
- A. Create an answer file named oobe.xml. Copy the file to a network share.
- B. Create an answer file named winnt.sif. Place the file on a removable drive.
- C. Create an answer file named sysprep.inf. Copy the file to a network share.
- D. Create an answer file named autounattend.xml. Place the file on a removable drive.
Answer : D
Question 7
Which of the following operating systems support an offline migration using USMT?
Choose three.
- A. Windows 2000 Professional
- B. Windows XP Professional
- C. Windows Vista
- D. Windows 7
Answer : B,C,D
Question 8
Your network consists of a single IPv4 subnet. The subnet contains 20 computers that run
Windows 7.
You add a new computer named Computer1 to the subnet.
You discover that Computer1 has an IP address of 169.254.34.12.
You cannot connect to other computers on the network. Other computers on the network can connect to each other.
You need to ensure that you can connect to all computers on the network.
What should you do?
- A. Turn off Windows Firewall.
- B. Run Ipconfig.exe /renew.
- C. Configure a static TCP/IP address.
- D. Run Netsh.exe interface ipv4 install.
Answer : C
Explanation:
[Need better justification]
Configuring static IP addresses -
When you assign a static IP address, you need to tell the computer the IP address you want to use, the subnet mask for this IP address, and, if necessary, the default gateway to use for internetwork communications. An IP address is a numeric identifier for a computer.
Ip addressing schemes vary according to how your network is configured, but they're normally assigned based on a particular network segment.
Question 9
You have a computer that runs Windows 7. The computer connects to the corporate network by using a VPN connection.
You need to ensure that you can access the Internet when the VPN connection is active.
The solution must prevent Internet traffic from being routed through the VPN connection.
What should you do?
- A. Configure a static DNS server address.
- B. Configure a static IP address and default gateway.
- C. Configure the security settings of the VPN connection.
- D. Configure the advanced TCP/IP settings of the VPN connection.
Answer : D
Explanation:
To prevent the default route from being created
In the properties of the TCP/IP protocol of the dial-up connection object, in the Advanced
TCP/IP Settings dialog box, click the General tab, and then clear the Use default gateway on remote network check box.
Question 10
You have a computer that runs Windows 7. Your company has a corporate intranet Web site. You open Windows Internet Explorer as shown in the exhibit. (Click the Exhibit button.)
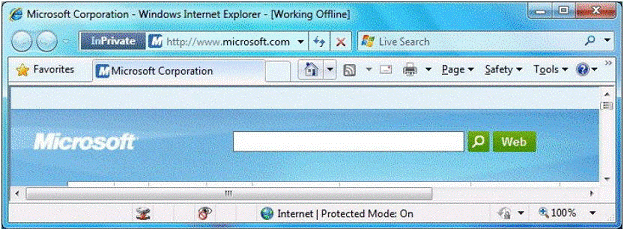
You need to ensure that you can access Web pages on both the Internet and the intranet.
What should you do?
- A. From the Files menu, click Work Offline.
- B. From the Safety menu, click InPrivate Filtering.
- C. From the Security tab, add the intranet Web site to the Trusted sites zone.
- D. From the Safety menu, click InPrivate Browsing.
Answer : A
Explanation:
Working Offline is activated -
On Internet Explorers File menu is a Work Offline item that toggles Internet Explorer between online and offline modes of operation.
(The question originally stated the Tools menu, maybe in a different version of IE this is the case, but for me and in the TechNet documentation it was under Files, so Im choosing to believe Tools was a mistake and it should be Files, this has been amended in the question).
InPrivate is turned on (does not prevent browsing the internet)
InPrivate Browsing helps prevent Internet Explorer from storing data about your browsing session. This includes cookies, temporary Internet files, history, and other data. Toolbars and extensions are disabled by default.
Question 11
You want to prohibit read, write, and execute access to all types of external storage devices.
What computer policy setting do you enable?
- A. All Removable Storage: Allow Direct Access In Remote Sessions
- B. All Removable Storage Classes: Deny All Access
- C. Removable Disks: Deny Read Access
- D. Removable Disks: Deny Write Access
Answer : B
Question 12
Which of the following tools can you use to determine if the applications installed on your computer running Windows Vista are known to have problems with Windows 7?
- A. Windows 7 Upgrade Advisor
- B. Sysprep
- C. USMT
- D. Windows PE
Answer : A
Explanation:
Windows 7 Upgrade Advisor -
Prior to attempting to perform the upgrade from Windows Vista to Windows 7, you should run the Windows 7 Upgrade Advisor. The Windows 7 Upgrade Advisor is an application that you can download from Microsofts Web site that will inform you if Windows 7 supports a computer running the current hardware and software configuration of Windows Vista.
Prior to running the Windows 7 Upgrade Advisor, you should ensure that all hardware that you want to use with Windows 7, such as printers, scanners, and cameras, are connected to the computer. The Upgrade Advisor generates a report that informs you of which applications and devices are known to have problems with Windows 7.
Question 13
You have a computer that runs Windows 7. The computer contains two volumes, C and D.
You create a new folder called D:\Reports.
You need to ensure that all files stored in the Reports folder are indexed by Windows
Search.
What should you do?
- A. Enable the archive attribute on the folder.
- B. Modify the Folder Options from Control Panel.
- C. Modify the properties of the Windows Search service.
- D. Create a new library and add the Reports folder to the library.
Answer : D
Explanation:
Libraries enable you to organize files by using metadata about the file, such as author, date, type, tags, and so on-instantly. Youre not limited to just browsing files by folder hierarchy. When you save files in a Library, Windows 7 indexes the files. You can use
Library features like the Arrange By control to instantly browse the files in the Library by metadata or use the Search Builder, which is built into the Search box in Windows
Explorer, to instantly search the files in the Library by metadata.
Question 14
You have a computer that runs Windows 7.
Your network contains a VPN server that runs Windows Server 2008.
You need to authenticate to the VPN server by using a smart card.
Which authentication setting should you choose?
- A. CHAP
- B. EAP
- C. MS-CHAP v2
- D. PAP
Answer : B
Explanation:
VPN Server Software Requirements
VPN server software requirements for smart card access are relatively straightforward. The remote access servers must run Windows 2000 Server or later, have Routing and Remote
Access enabled, and must support Extensible Authentication Protocol-Transport Layer
Security (EAP-TLS). EAP-TLS is a mutual authentication mechanism developed for use in conjunction with security devices, such as smart cards and hardware tokens. EAP-TLS supports Point-to-Point Protocol (PPP) and VPN connections, and enables exchange of shared secret keys for MPPE, in addition to Ipsec. The main benefits of EAP-TLS are its resistance to brute-force attacks and its support for mutual authentication. With mutual authentication, both client and server must prove their identities to each other. If either client or server does not send a certificate to validate its identity, the connection terminates.Microsoft Windows Server 2003 supports EAP-TLS for dial-up and VPN connections, which enables the use of smart cards for remote users. For more information about EAP-TLS, see the Extensible Authentication Protocol (EAP) topic at www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/auth_eap. mspx.
For more information about EAP certificate requirements, see the Microsoft Knowledge
Base article "Certificate Requirements when you use EAP-TLS or PEAP with EAP-TLS" at http://support.microsoft.com/default.aspx? scid=814394.
Question 15
You have a computer named Computer1 that runs Windows 7. The computer is a member of an Active Directory domain. The network contains a file server named Server1 that runs
Windows Server 2008.
You log on to the computer by using an account named User1.
You need to ensure that when you connect to Server1, you authenticate by using an account named Admin1.
What should you do on Computer1?
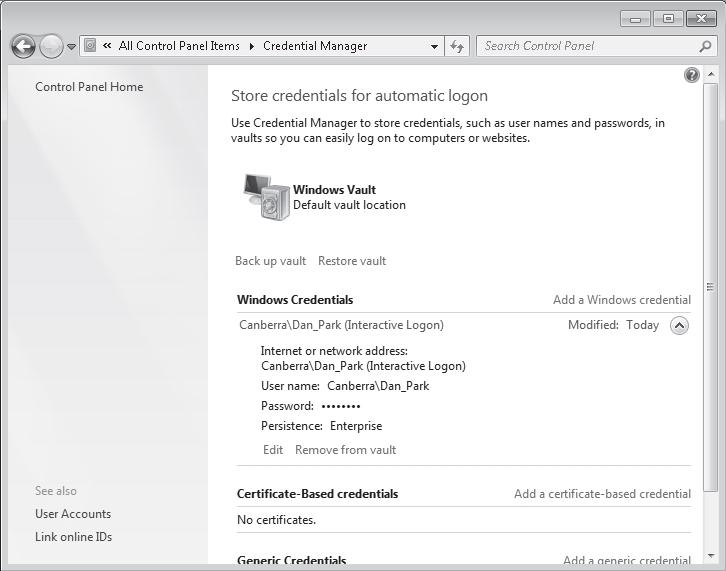
- A. From User Accounts, select Link online IDs.
- B. From Windows CardSpace, select Add a card.
- C. From Credential Manager, select Add a Windows credential.
- D. From Local Security Policy, modify the Access this computer from the network user right.
Answer : C
Explanation:
Credential Manager -
Credential Manager stores logon user name and passwords for network resources, including file servers, Web sites, and terminal services servers. Credential Manager stores user name and password data in the Windows Vault. You can back up the Windows Vault and restore it on other computers running Windows 7 as a method of transferring saved credentials from one computer to another. Although Credential Manager can be used to back up some forms of digital certificates, it cannot be used to back up and restore the self- signed Encrypting File System (EFS) certificates that Windows 7 generates automatically when you encrypt a file. For this reason, you must back up EFS certificates using other tools. You will learn about backing up EFS certificates later in this lesson.