Windows Server 2008 Active Directory, Configuring v41.0
Question 1
Your network consists of a single Active Directory domain. You have a domain controller and a member server that run Windows Server 2008 R2. Both servers are configured as
DNS servers. Client computers run either Windows XP Service Pack 3 or Windows 7.
You have a standard primary zone on the domain controller. The member server hosts a secondary copy of the zone.
You need to ensure that only authenticated users are allowed to update host (A) records in the DNS zone.
What should you do first?
- A. On the member server, add a conditional forwarder.
- B. On the member server, install Active Directory Domain Services.
- C. Add all computer accounts to the DNS UpdateProxy group.
- D. Convert the standard primary zone to an Active Directory-integrated zone.
Answer : D
Explanation:
http://technet.microsoft.com/en-us/library/cc726034.aspx
Understanding Active Directory Domain Services Integration
The DNS Server service is integrated into the design and implementation of Active
Directory Domain Services (AD DS). AD DS provides an enterprise-level tool for organizing, managing, and locating resources in a network.
How DNS integrates with AD DS -
When you install AD DS on a server, you promote the server to the role of a domain controller for a specified domain. As part of this process, you are prompted to specify a
DNS domain name for the AD DS domain which you are joining and for which you are promoting the server, and you are offered the option to install the DNS Server role. This option is provided because a DNS server is required to locate this server or other domain controllers for members of an AD DS domain.
Benefits of AD DS integration -
For networks that deploy DNS to support AD DS, directory-integrated primary zones are strongly recommended. They provide the following benefits:
DNS features multimaster data replication and enhanced security based on the capabilities of AD DS.
In a standard zone storage model, DNS updates are conducted based on a single-master update model. In this model, a single authoritative DNS server for a zone is designated as the primary source for the zone. This server maintains the master copy of the zone in a local file. With this model, the primary server for the zone represents a single fixed point of failure. If this server is not available, update requests from DNS clients are not processed for the zone.
With directory-integrated storage, dynamic updates to DNS are sent to any AD DS- integrated DNS server and are replicated to all other AD DS-integrated DNS servers by means of AD DS replication. In this model, any AD DS-integrated DNS servercan accept dynamic updates for the zone. Because the master copy of the zone is maintained in the
AD DS database, which is fully replicated to all domain controllers, the zone can be updated by the DNS servers operating at any domain controller for the domain. With the multimaster update model of AD DS, any of the primary servers for the directoryintegrated zone can process requests from DNS clients to update the zone as long as a domain controller is available and reachable on the network.
Also, when you use directory-integrated zones, you can use access control list (ACL) editing to secure a dnsZone object container in the directory tree. This feature provides detailed access to either the zone or a specified resource record in the zone. For example, an ACL for a zone resource record can be restricted so that dynamic updates are allowed only for a specified client computer or a secure group, such as a domain administrators group. This security feature is not available with standard primary zones.
Zones are replicated and synchronized to new domain controllers automatically whenever a new one is added to an AD DS domain.
By integrating stora
Question 2
Your network consists of a single Active Directory domain. All domain controllers run
Windows Server 2008 R2 and are configured as DNS servers. A domain controller named
DC1 has a standard primary zone for contoso.com. A domain controller named DC2 has a standard secondary zone for contoso.com.
You need to ensure that the replication of the contoso.com zone is encrypted.
You must not lose any zone data.
What should you do?
- A. Convert the primary zone into an Active Directory-integrated stub zone. Delete the secondary zone.
- B. Convert the primary zone into an Active Directory-integrated zone. Delete the secondary zone.
- C. Configure the zone transfer settings of the standard primary zone. Modify the Master Servers lists on the secondary zone.
- D. On both servers, modify the interface that the DNS server listens on.
Answer : B
Explanation:
Answer: Convert the primary zone into an Active Directory-integrated zone. Delete the secondary zone. http://technet.microsoft.com/en-us/library/cc771150.aspx
Change the Zone Type -
You can use this procedure to change make a zone a primary, secondary, or stub zone.
You can also use it to integrate a zone with Active Directory Domain Services (AD DS). http://technet.microsoft.com/en-us/library/cc726034.aspx
Understanding Active Directory Domain Services Integration
The DNS Server service is integrated into the design and implementation of Active
Directory Domain Services (AD DS). AD DS provides an enterprise-level tool for organizing, managing, and locating resources in a network.
Benefits of AD DS integration -
For networks that deploy DNS to support AD DS, directory-integrated primary zones are strongly recommended. They provide the following benefits:
DNS features multimaster data replication and enhanced security based on the capabilities of AD DS.
In a standard zone storage model, DNS updates are conducted based on a single-master update model.
In this model, a single authoritative DNS server for a zone is designated as the primary source for the zone. This server maintains the master copy of the zone in a local file. With this model, the primary server for the zone represents a single fixed point of failure. If this server is not available, update requests from DNS clients are not processed for the zone.
With directory-integrated storage, dynamic updates to DNS are sent to any AD DS- integrated DNS server and are replicated to all other AD DS-integrated DNS servers by means of AD DS replication. In this model, any AD DS-integrated DNS servercan accept dynamic updates for the zone. Because the master copy of the zone is maintained in the
AD DS database, which is fully replicated to all domain controllers, the zone can be updated by the DNS servers operating at any domain controller for the domain. With the multimaster update model of AD DS, any of the primary servers for the directoryintegrated zone can process requests from DNS clients to update the zone as long as a domain controller is available and reachable on the network.
Zones are replicated and synchronized to new domain controllers automatically whenever a new one is added to an AD DS domain.
By integrating storage of your DNS zone databases in AD DS, you can streamline database replication planning for your network.
Directory-integrated replication is faster and more efficient than standard DNS replication. http://technet.microsoft.com/en-us/library/ee649124%28v=ws.10%29.aspx
Deploy IPsec Policy to DNS Servers
You can deploy IPsec rules through one of the following mechanisms:
Domain Controllers organizational unit (OU): If the DNS servers in your domain are Active
Directoryintegrated, you can deploy IPsec policy settings using the Domain Controllers OU.
This option is recommended to make configuration and deployment easier.
DNS Server OU or security group: If you have DNS
Question 3
Your company has a single Active Directory domain. All domain controllers run Windows
Server 2003.
You install Windows Server 2008 R2 on a server.
You need to add the new server as a domain controller in your domain.
What should you do first?
- A. On a domain controller run adprep /rodcprep.
- B. On the new server, run dcpromo /adv.
- C. On the new server, run dcpromo /createdcaccount.
- D. On a domain controller, run adprep /forestprep.
Answer : D
Explanation:
http://social.technet.microsoft.com/Forums/en-US/winserverDS/thread/9931e32f-6302-
40f0-a7a1-2598a96cd0c1/
DC promotion and adprep/forestprep
Q: I've tried to dcpromo a new Windows 2008 server installation to be a Domain Controller, running in an existing domain. I am informed that, first, I must run adprep/forestprep ("To install a domain controller into this Active Directory forest, you must first perpare the forest using "adprep/forestprep". The Adprep utility is available on the Windows Server 2008 installation media in the Windows\sources\adprep folder"
A1:
You can run adprep from an existing Windows Server 2003 domain controller. Copy the contents of the \sources\adprep folder from the Windows Server 2008 installation DVD to the schema master role holder and run Adprep from there.
A2: to introduce the first W2K8 DC within an AD forest....
(1) no AD forest exists yet:
--> on the stand alone server execute: DCPROMO
--> and provide the information needed
(2) an W2K or W2K3 AD forest already exists:
--> ADPREP /Forestprep on the w2k/w2k3 schema master (both w2k/w2k3 forests)
--> ADPREP /rodcprep on the w2k3 domain master (only w2k3 forests)
--> ADPREP /domainprep on the w2k3 infrastructure master (only w2k3 domains)
--> ADPREP /domainprep /gpprep on the w2k infrastructure master (only w2k domains)
--> on the stand alone server execute: DCPROMO
--> and provide the information needed
Question 4
Your company has a domain controller that runs Windows Server 2008. The domain controller has the backup features installed.
You need to perform a non-authoritative restore of the doman controller using an existing backup file.
What should you do?
- A. Restart the domain controller in Directory Services Restore Mode and use wbadmin to restore critical volume
- B. Restart the domain controller in Directory Services Restore Mode and use the backup snap-in to restore critical volume
- C. Restart the domain controller in Safe Mode and use wbadmin to restore critical volume
- D. Restart the domain controller in Safe Mode and use the backup snap-in to restore critical volume
Answer : A
Explanation:
Almost identical to B42 -
http://technet.microsoft.com/en-us/library/cc816627%28v=ws.10%29.aspx
Performing Nonauthoritative Restore of Active Directory Domain Services
A nonauthoritative restore is the method for restoring Active Directory Domain Services
(AD DS) from a system state, critical-volumes, or full server backup. A nonauthoritative restore returns the domain controller to its state at the time of backup and then allows normal replication to overwrite that state with any changes that occurred after the backup was taken. After you restore AD DS from backup, the domain controller queries its replication partners. Replication partners use the standard replication protocols to update
AD DS and associated information, including the SYSVOL shared folder, on the restored domain controller.
You can use a nonauthoritative restore to restore the directory service on a domain controller without reintroducing or changing objects that have been modified since the backup. The most common use of a nonauthoritative restore is to reinstate a domain controller, often after catastrophic or debilitating hardware failures. In the case of data corruption, do not use nonauthoritative restore unless you have confirmed that the problem is with AD DS.
Nonauthoritative Restore Requirements You can perform a nonauthoritative restore from backup on a Windows Server 2008 system that is a standalone server, member server, or domain controller.
On domain controllers that are running Windows Server 2008, you can stop and restart AD
DS as a service. Therefore, in Windows Server 2008, performing offline defragmentation and other database management tasks does not require restarting the domain controller in
Directory Services Restore Mode (DSRM). However, you cannot perform a nonauthoritative restore after simply stopping the AD DS service in regular startup mode.
You must be able to start the domain controller in Directory Services Restore Mode
(DSRM). If the domain controller cannot be started in DSRM, you must first reinstall the operating system.
To perform a nonauthoritative restore, you need one of the following types of backup for your backup source:
System state backup: Use this type of backup to restore AD DS. If you have reinstalled the operating system, you must use a critical-volumes or full server backup. If you are restoring a system state backup, use the wbadmin start systemstaterecovery command.
Critical-volumes backup: A critical-volumes backup includes all data on all volumes that contain operating system and registry files, boot files, SYSVOL files, or Active Directory files. Use this type of backup if you want to restore more than the system state. To restore a critical-volumes backup, use the wbadmin start recovery command.
Full server backup: Use this type of backup only if you cannot start the server or you do not have a system state or critical-volumes backup. A full server backup is generally larger than a critical-volumes backup.
Resto
Question 5
Your company has an Active Directory forest that contains only Windows Server 2008 domain controllers.
You need to prepare the Active Directory domain to install Windows Server 2008 R2 domain controllers.
Which two tasks should you perform? (Each correct answer presents part of the solution.
Choose two.)
- A. Run the adprep /domainprep command.
- B. Raise the forest functional level to Windows Server 2008.
- C. Raise the domain functional level to Windows Server 2008.
- D. Run the adprep /forestprep command.
Answer : A,D
Explanation:
http://www.petri.co.il/prepare-for-server-2008-r2-domain-controller.htm
Prepare your Domain for the Windows Server 2008 R2 Domain Controller
Before installing the first Windows Server 2008 R2 domain controller (DC) into an existing
Windows 2000, Windows Server 2003 or Windows Server 2008 domain, you must prepare the AD forest and domain. You do so by running a tool called ADPREP.
ADPREP extends the Active Directory schema and updates permissions as necessary to prepare a forest and domain for a domain controller that runs the Windows Server 2008 R2 operating system.
Note: You may remember that ADPREP was used on previous operating systems such as
Windows Server 2003, Windows Server 2003 R2 and Windows Server 2008. This article focuses on Windows Server 2008 R2.
What does ADPREP do? ADPREP has parameters that perform a variety of operations that help prepare an existing Active Directory environment for a domain controller that runs
Windows Server 2008 R2. Not all versions of ADPREP perform the same operations, but generally the different types of operations that ADPREP can perform include the following:
Updating the Active Directory schema
Updating security descriptors -
Modifying access control lists (ACLs) on Active Directory objects and on files in the
SYSVOL shared folder -
Creating new objects, as needed -
Creating new containers, as needed
To prepare the forest and domain for the installation of the first Windows Server 2008 R2 domain controller please perform these tasks:
Lamer note: The following tasks are required ONLY before adding the first Windows Server
2008 R2 domain controller. If you plan on simply joining a Windows Server 2008 R2 Server to the domain and configuring as a regular member server, none of the following tasks are required.
Another lamer note: Please make sure you read the system requirements for Windows
Server 2008 R2. For example, you cannot join a Windows Server 2008 R2 server to a
Windows NT 4.0 domain, not can it participate as a domain controller in a mixed domain. If any domain controllers in the forest are running Windows 2000 Server, they must be running Service Pack 4 (SP4).
First, you should review and understand the schema updates and other changes that
ADPREP makes as part of the schema management process in Active Directory Domain
Services (AD DS). You should test the ADPREP schema updates in a lab environment to ensure that they will not conflict with any applications that run in your environment.
You must make a system state backup for your domain controllers, including the schema master and at least one other domain controller from each domain in the forest (you do have backups, don't you?). Also, make sure that you can log on to the schema master with an account that has sufficient credentials to run adprep /forestprep. You must be a member of the Schema Admins group, the Enterprise Admins group, and the Domain Admins group of the domain that hosts the schema master, which is, by default, the fo
Question 6
Your company has an Active Directory domain. The company has two domain controllers named DC1 and DC2. DC1 holds the Schema Master role.
DC1 fails. You log on to Active Directory by using the administrator account. You are not able to transfer the Schema Master operations role.
You need to ensure that DC2 holds the Schema Master role.
What should you do?
- A. Configure DC2 as a bridgehead server.
- B. On DC2, seize the Schema Master role.
- C. Log off and log on again to Active Directory by using an account that is a member of the Schema Administrators group. Start the Active Directory Schema snap-in.
- D. Register the Schmmgmt.dll. Start the Active Directory Schema snap-in.
Answer : B
Explanation:
Answer: On DC2, seize the Schema Master role.
http://technet.microsoft.com/en-us/library/cc816645%28v=ws.10%29.aspx
Transfer the Schema Master -
You can use this procedure to transfer the schema operations master role if the domain controller that currently hosts the role is inadequate, has failed, or is being decommissioned. The schema master is a forest-wide operations master (also known as flexible single master operations or FSMO) role.
Note: You perform this procedure by using a Microsoft Management Console (MMC) snap- in, although you can also transfer this role by using Ntdsutil.exe.
Membership in Schema Admins, or equivalent, is the minimum required to complete this procedure. http://technet.microsoft.com/en-us/library/cc794853%28v=ws.10%29.aspx
Seize the AD LDS Schema Master Role
The schema master is responsible for performing updates to the Active Directory
Lightweight Directory Services (AD LDS) schema. Each configuration set has only one schema master. All write operations to the AD
LDS schema can be performed only when connected to the AD LDS instance that holds the schema master role within its configuration set. Those schema updates are replicated from the schema master to all other instances in the configuration set.
Membership in the AD LDS Administrators group, or equivalent, is the minimum required to complete this procedure.
Caution: Do not seize the schema master role if you can transfer it instead. Seizing the schema master role is a drastic step that should be considered only if the current operations master will never be available again.
Question 7
You have a single Active Directory domain. All domain controllers run Windows Server
2008 and are configured as DNS servers.
The domain contains one Active Directory-integrated DNS zone.
You need to ensure that outdated DNS records are automatically removed from the DNS zone.
What should you do?
- A. From the properties of the zone, modify the TTL of the SOA record.
- B. From the properties of the zone, enable scavenging.
- C. From the command prompt, run ipconfig /flushdns.
- D. From the properties of the zone, disable dynamic updates.
Answer : B
Explanation:
http://technet.microsoft.com/en-us/library/cc753217.aspx
Set Aging and Scavenging Properties for the DNS Server
The DNS Server service supports aging and scavenging features. These features are provided as a mechanism for performing cleanup and removal of stale resource records, which can accumulate in zone data over time. You can use this procedure to set the default aging and scavenging properties for the zones on a server.
Further information:
http://technet.microsoft.com/en-us/library/cc771677.aspx
Understanding Aging and Scavenging
Question 8
Your company uses a Windows 2008 Enterprise certificate authority (CA) to issue certificates.
You need to implement key archival.
What should you do?
- A. Configure the certificate for automatic enrollment for the computers that store encrypted files.
- B. Install an Enterprise Subordinate CA and issue a user certificate to users of the encrypted files.
- C. Apply the Hisecdc security template to the domain controllers.
- D. Archive the private key on the server.
Answer : D
Explanation:
Answer: Archive the private key on the server.
http://technet.microsoft.com/en-us/library/cc753011.aspx
Enable Key Archival for a CA -
Before a key recovery agent can use a key recovery certificate, the key recovery agent must have enrolled for the key recovery certificate and be registered as the recovery agent for the certification authority (CA).
You must be a CA administrator to complete this procedure.
To enable key archival for a CA:
1. Open the Certification Authority snap-in.
2. In the console tree, click the name of the CA.
3. On the Action menu, click Properties.
4. Click the Recovery Agents tab, and then click Archive the key.
5. In Number of recovery agents to use, type the number of key recovery agents that will be used to encrypt the archived key.
The Number of recovery agents to use must be between one and the number of key recovery agent certificates that have been configured.
6. Click Add. Then, in Key Recovery Agent Selection, click the key recovery certificates that are displayed, and click OK.
7. The certificates should appear in the Key recovery agent certificates list, but their status is listed as Not loaded.
8. Click OK or Apply. When prompted to restart the CA, click Yes. When the CA has restarted, the status of the certificates should be listed as Valid.
Further information:
http://technet.microsoft.com/en-us/library/ee449489%28v=ws.10%29.aspx
Key Archival and Management in Windows Server 2008
http://technet.microsoft.com/en-us/library/cc730721.aspx
Managing Key Archival and Recovery
Question 9
Your network consists of a single Active Directory domain. The functional level of the forest is Windows Server 2008 R2.
You need to create multiple password policies for users in your domain.
What should you do?
- A. From the Group Policy Management snap-in, create multiple Group Policy objects.
- B. From the Schema snap-in, create multiple class schema objects.
- C. From the ADSI Edit snap-in, create multiple Password Setting objects.
- D. From the Security Configuration Wizard, create multiple security policies.
Answer : C
Explanation:
Answer: From the ADSI Edit snap-in, create multiple Password Setting objects. http://technet.microsoft.com/en-us/library/cc770842%28v=ws.10%29.aspx
AD DS Fine-Grained Password and Account Lockout Policy Step-by-Step Guide
In Windows Server 2008, you can use fine-grained password policies to specify multiple password policies and apply different password restrictions and account lockout policies to different sets of users within a single domain.
To store fine-grained password policies, Windows Server 2008 includes two new object classes in the Active
Directory Domain Services (AD DS) schema:
Password Settings Container -
Password Settings The Password Settings Container (PSC) object class is created by default under the System container in the domain. It stores the Password Settings objects
(PSOs) for that domain. You cannot rename, move, or delete this container.
Steps to configure fine-grained password and account lockout policies
When the group structure of your organization is defined and implemented, you can configure and apply finegrained password and account lockout policies to users and global security groups. Configuring fine-grained password and account lockout policies involves the following steps:
Step 1: Create a PSO -
Step 2: Apply PSOs to Users and Global Security Groups
Step 3: Manage a PSO -
Step 4: View a Resultant PSO for a User or a Global Security Group http://technet.microsoft.com/en-us/library/cc754461%28v=ws.10%29.aspx
Step 1: Create a PSO -
You can create Password Settings objects (PSOs):
Creating a PSO using the Active Directory module for Windows PowerShell
Creating a PSO using ADSI Edit -
Creating a PSO using ldifde -
Question 10
The default domain GPO in your company is configured by using the following account policy settings:
-> Minimum password length: 8 characters
-> Maximum password age: 30 days
-> Enforce password history: 12 passwords remembered
-> Account lockout threshold: 3 invalid logon attempts
-> Account lockout duration: 30 minutes
You install Microsoft SQL Server on a computer named Server1 that runs Windows Server
2008 R2. The SQL Server application uses a service account named SQLSrv. The SQLSrv account has domain user rights.
The SQL Server computer fails after running successfully for several weeks. The SQLSrv user account is not locked out.
You need to resolve the server failure and prevent recurrence of the failure. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
- A. Reset the password of the SQLSrv user account.
- B. Configure the local security policy on Server1 to grant the Logon as a service right on the SQLSrv user account.
- C. Configure the properties of the SQLSrv account to Password never expires.
- D. Configure the properties of the SQLSrv account to User cannot change password.
- E. Configure the local security policy on Server1 to explicitly grant the SQLSrv user account the Allow logon locally user right.
Answer : AC
Explanation:
Personal comment:
Maximum password age: 30 days -
The most probable cause for the malfunction is that the password has expired.
You need to reset the password and set it to never expire.
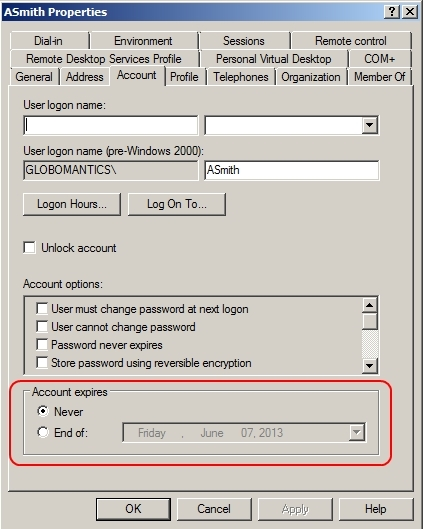
C:\Documents and Settings\usernwz1\Desktop\1.PNG
Question 11
Your company has an Active Directory domain that runs Windows Server 2008 R2. The
Sales OU contains an OU for Computers, an OU for Groups, and an OU for Users.
You perform nightly backups. An administrator deletes the Groups OU.
You need to restore the Groups OU without affecting users and computers in the Sales
OU.
What should you do?
- A. Perform an authoritative restore of the Sales OU.
- B. Perform a non-authoritative restore of the Sales OU.
- C. Perform an authoritative restore of the Groups OU.
- D. Perform a non-authoritative restore of the Groups OU.
Answer : C
Explanation:
Answer: Perform an authoritative restore of the Groups OU.
http://technet.microsoft.com/en-us/library/cc816878%28v=ws.10%29.aspx
Performing Authoritative Restore of Active Directory Objects
An authoritative restore process returns a designated, deleted Active Directory object or container of objects to its predeletion state at the time when it was backed up. For example, you might have to perform an authoritative restore if an administrator inadvertently deletes an organizational unit (OU) that contains a large number of users. In most cases, there are two parts to the authoritative restore process: a nonauthoritative restore from backup, followed by an authoritative restore of the deleted objects. If you perform a nonauthoritative restore from backup only, the deleted OU is not restored because the restored domain controller is updated after the restore process to the current status of its replication partners, which have deleted the OU. To recover the deleted OU, after you perform nonauthoritative restore from backup and before allowing replication to occur, you must perform an authoritative restore procedure. During the authoritative restore procedure, you mark the OU as authoritative and let the replication process restore it to all the other domain controllers in the domain. After an authoritative restore, you also restore group memberships, if necessary.
Question 12
Your company has a main office and a branch office. You deploy a read-only domain controller (RODC) that runs Microsoft Windows Server 2008 to the branch office.
You need to ensure that users at the branch office are able to log on to the domain by using the RODC.
What should you do?
- A. Add another RODC to the branch office.
- B. Configure a new bridgehead server in the main office.
- C. Decrease the replication interval for all connection objects by using the Active Directory Sites and Services console.
- D. Configure the Password Replication Policy on the RODC.
Answer : D
Explanation:
Answer: Configure the Password Replication Policy on the RODC. http://technet.microsoft.com/en-us/library/cc754956%28v=ws.10%29.aspx
RODC Frequently Asked Questions -
What new attributes support the RODC Password Replication Policy?
Password Replication Policy is the mechanism for determining whether a user or computer's credentials are allowed to replicate from a writable domain controller to an
RODC. The Password Replication Policy is always set on a writable domain controller running Windows Server 2008.
What operations fail if the WAN is offline, but the RODC is online in the branch office?
If the RODC cannot connect to a writable domain controller running Windows Server 2008 in the hub, the following branch office operations fail:
Password changes -
Attempts to join a computer to a domain
Computer rename -
Authentication attempts for accounts whose credentials are not cached on the RODC
Group Policy updates that an administrator might attempt by running the gpupdate /force command
What operations succeed if the WAN is offline, but the RODC is online in the branch office?
If the RODC cannot connect to a writable domain controller running Windows Server 2008 in the hub, the following branch office operations succeed:
Authentication and logon attempts, if the credentials for the resource and the requester are already cached, Local RODC server administration performed by a delegated RODC server administrator.
Question 13
You need to ensure that users who enter three successive invalid passwords within 5 minutes are locked out for 5 minutes.
Which three actions should you perform? (Each correct answer presents part of the solution.
Choose three.)
- A. Set the Minimum password age setting to one day.
- B. Set the Maximum password age setting to one day.
- C. Set the Account lockout duration setting to 5 minutes.
- D. Set the Reset account lockout counter after setting to 5 minutes.
- E. Set the Account lockout threshold setting to 3 invalid logon attempts.
- F. Set the Enforce password history setting to 3 passswords remembered.
Answer : C,D,E
Explanation:
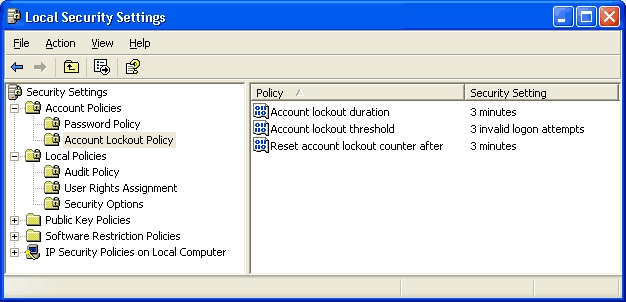
C:\Documents and Settings\usernwz1\Desktop\1.PNG
Question 14
Your company has an Active Directory forest that runs at the functional level of Windows
Server 2008.
You implement Active Directory Rights Management Services (AD RMS).
You install Microsoft SQL Server 2005. When you attempt to open the AD RMS administration Web site, you receive the following error message: "SQL Server does not exist or access denied."
You need to open the AD RMS administration Web site.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
- A. Restart IIS.
- B. Manually delete the Service Connection Point in AD DS and restart AD RMS.
- C. Install Message Queuing.
- D. Start the MSSQLSVC service.
Answer : A,D
Explanation:
http://technet.microsoft.com/en-us/library/cc747605%28v=ws.10%29.aspx#BKMK_1
RMS Administration Issues -
"SQL Server does not exist or access denied" message received when attempting to open the RMS
Administration Web site -
If you have installed RMS by using a new installation of SQL Server 2005 as your database server the SQL Server Service might not be started. In SQL Server 2005, the
MSSQLSERVER service is not configured to automatically start when the server is started.
If you have restarted your SQL Server since installing RMS and have not configured this service to automatically restart RMS will not be able to function and only the RMS Global
Administration page will be accessible.
After you have started the MSSQLSERVER service, you must restart IIS on each RMS server in the cluster to restore RMS functionality.
Question 15
A user in a branch office of your company attempts to join a computer to the domain, but the attempt fails.
You need to enable the user to join a single computer to the domain.
You must ensure that the user is denied any additional rights beyond those required to complete the task.
What should you do?
- A. Prestage the computer account in the Active Directory domain.
- B. Add the user to the Domain Administrators group for one day.
- C. Add the user to the Server Operators group in the Active Directory domain.
- D. Grant the user the right to log on locally by using a Group Policy Object (GPO).
Answer : A
Explanation:
http://technet.microsoft.com/en-us/library/cc770832%28v=ws.10%29.aspx#BKMK_1
Prestaging Client Computers -
Benefits of Prestaging Client Computers
Prestaging clients provides three main benefits:
An additional layer of security. You can configure Windows Deployment Services to answer only prestaged clients, therefore ensuring that clients that are not prestaged will not be able to boot from the network. Additional flexibility. Prestaging clients increases flexibility by enabling you to control the following. For instructions on performing these tasks, see the
Prestage Computers section of How to Manage Client Computers.
* The computer account name and location within AD DS.
* Which server the client should network boot from.
* Which network boot program the client should receive.
* Other advanced options for example, what boot image a client will receive or what
Windows Deployment Services client unattend file the client should use.
The ability for multiple Windows Deployment Services servers to service the same network segment. You can do this by restricting the server to answer only a particular set of clients.
Note that the prestaged client must be in the same forest as the Windows Deployment
Services server (trusted forests do not work).
Further information:
http://www.windows-noob.com/forums/index.php?/topic/506-how-can-i-prestage-a- computer-for-wds/howcan I PRESTAGE a computer for WDS?