Advanced Solutions of Microsoft Exchange Server 2013 v22.0
Question 1
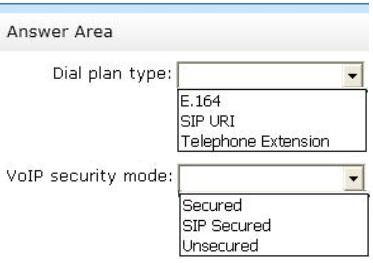
You need to configure the Exchange Server UM dial plan for the planned integration of UM and Lync Server.
How should you configure the UM dial plan? (To answer, select the appropriate dial plan type and VoIP security mode in the answer area.)
Answer : 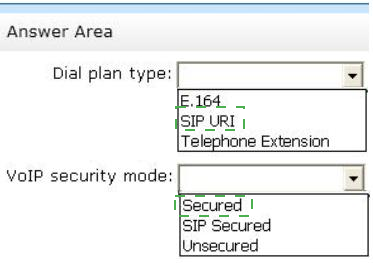
Explanation:
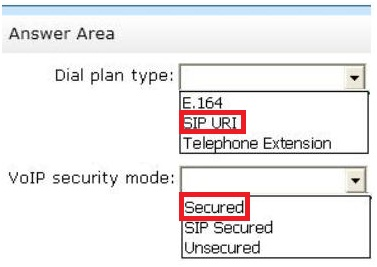
* Scenario: Integrate Unified Messaging (UM) services with the Lync Server 2013 infrastructure.
* If you want to integrate Exchange Unified Messaging (UM) with Lync Server 2013, you must perform the following tasks:
/ On the Exchange UM server, create a SIP dial plan based on your organizations specific deployment requirements.
/ To encrypt Enterprise Voice traffic, configure the security settings on the Exchange UM
SIP dial plan as SIP Secured or Secured.
Etc.
Note:
* There are three formats or URI types that can be configured on UM dial plans:
/ Telephone Extension (TeleExtn)
/ SIP URI
Session Initiation Protocol (SIP) is a standard protocol for initiating interactive user sessions that involve multimedia elements such as video, voice, chat, and gaming. SIP is a request-to-response based protocol that answers requests from clients and responses from servers.
/ E.164
* When you configure the dial plan to use SIP secured mode, only the SIP signaling traffic will be encrypted, and the RTP media channels will still use TCP, which isnt encrypted.
However, when you configure the dial plan to use Secured mode, both the SIP signaling traffic and the RTP media channels are encrypted. An encrypted signaling media channel that uses Secure Realtime Transport Protocol (SRTP) also uses mutual TLS to encrypt the
VoIP data.
Question 2
You are attempting to resolve the email delivery issue for Fabrikam.
You need to identify which certificate is being used by the servers in the Exchange Server organization of Fabrikam.
In which directory on EX1 should you review the log files? (To answer, select the appropriate directory in the answer area.)
Answer : 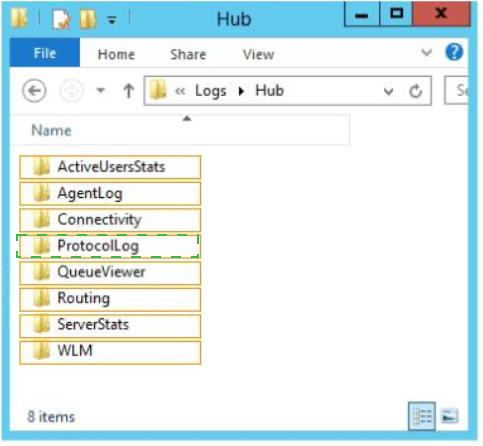
Explanation:
* Scenario: After a change to a certificate, users report that email messages sent to
Fabrikam are not delivered.
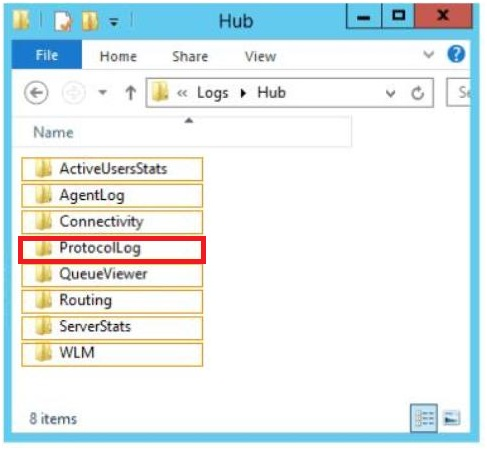
* ProtocolLog
Protocol logging records the SMTP conversations that occur between messaging servers as part of message delivery. These SMTP conversations occur on Send connectors and
Receive connectors that exist in the Front End Transport service on Client Access servers, the Transport service on Mailbox servers, and the Mailbox Transport service on Mailbox servers. You can use protocol logging to diagnose mail flow problems.
Question 3
You need to recommend a solution that meets the compliance requirements for email messages that contain information about the Fabrikam acquisition.
Which three actions should you recommend? (Each correct answer presents part of the solution. Choose three.)
- A. Create an Outlook protection rule.
- B. Create a new custom message classification.
- C. Modify the registry on all client computers.
- D. Modify the Content Filtering settings.
- E. Export the Message Classification configuration to an .xml file.
Answer : B,C,E
Explanation:
B: Use the New-MessageClassification cmdlet to create a message classification instance in your organization.
E: After you create a new message classification, you can specify the message classification as a transport rule predicate. Before Microsoft Outlook and Outlook Web App users can apply the message classification to messages, you must update the end-user systems with the message classification XML file created by the Export-
OutlookClassification.ps1 script file. The Export-OutlookClassification.ps1 script file is located in the %ExchangeInstallPath%Scripts directory.
C: Microsoft Office Outlook requires a local file (Classifications.xml) that contains definitions of the message classifications that Microsoft Exchange Server supports before
Outlook users can apply message classifications to their messages. You must also create a registry key that enables message classification and references the Classifications.xml file on the Outlook user's computer.
* From scenario:
Compliance Requirements include:
Users must use a custom message classification when they send email messages that contain information about the planned acquisition of Fabrikam.
Question 4
You need to identify which technologies must be used to meet the security requirements.
Which technologies should you identify? (To answer, drag the appropriate technologies to the correct requirements. Each technology may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
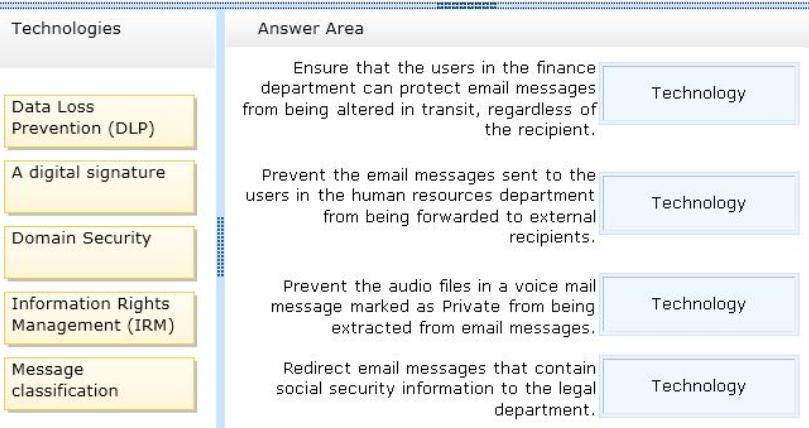
Answer : 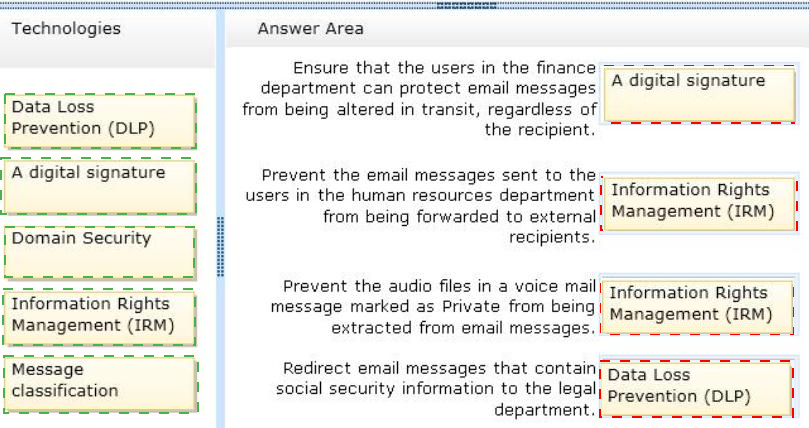
Question 5
You need to implement a solution that meets the collaboration requirements.
What should you do?
- A. Run the Set-CASMailbox cmdlet.
- B. Create an organization relationship.
- C. Create a new sharing policy.
- D. Modify the organization configuration.
Answer : B
Explanation:
* Scenario: Custom recipient MailTips created in the Exchange Server organization of Trey
Research must be visible to the users at Fabrikam. The solution must ensure that administrators can define a subset of users who can share their MailTips.
* MailTips Over Organization Relationships
You may want to restrict certain types of MailTips. You can either allow all MailTips to be returned or allow only a limited set that would prevent NDRs. You can configure this setting parameter on the Set-OrganizationRelationship cmdlet.
Reference: MailTips over organization relationships
Question 6
You restore the files of DB3 to EX3.
You need to mount DB3 on EX3. The solution must ensure that email messages sent to the users of DB3 while the database was offline are delivered once DB3 is mounted.
Which three actions should you perform in sequence? (To answer, move the appropriate three actions from the list of actions to the answer area and arrange them in the correct order.)
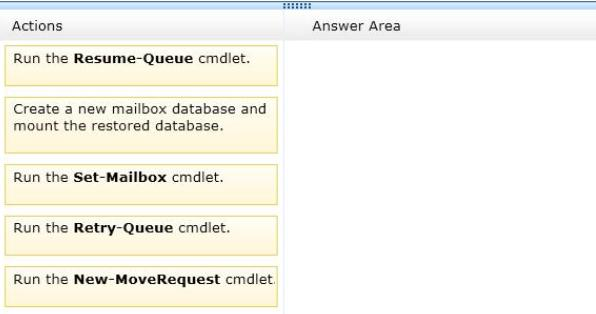
Answer : 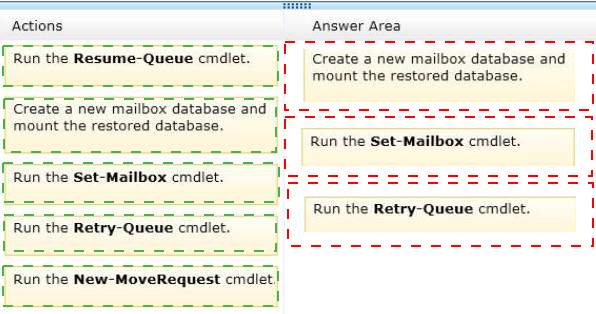
Explanation:
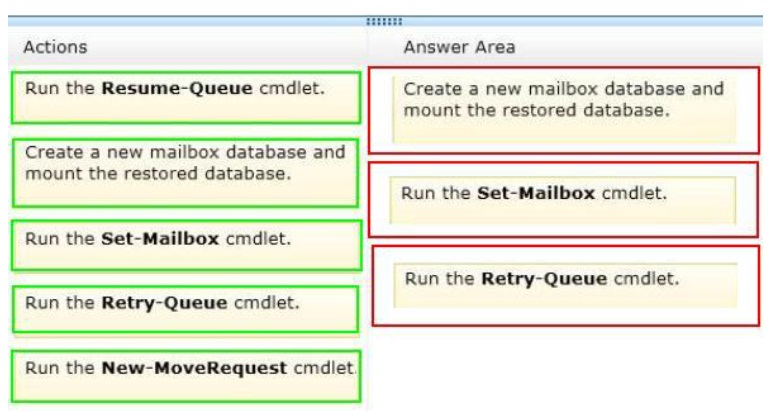
Question 7
You need to implement a solution that meets the compliance requirements for the members of the legal department.
Which two cmdlets should you use? (Each correct answer presents part of the solution.
Choose two.)
- A. New-RoleAssignmentPolicy
- B. Add-ManagementRoleEntry
- C. New-ManagementRoleAssignment
- D. New-ManagementRole
- E. New-ManagementScope
Answer : CD
Explanation:
* From scenario:
/ Only the users in the legal department must be able to use eDiscovery to view the contents of email messages sent by the finance department users.
/ Users in the legal department use a shared mailbox named Legal. Legal is enabled for In-
Place Hold. Legal is the only mailbox on DB2.
We need to assign the role to the legal department users using the New-
ManagementRoleAssignment cmdlet.
To restrict the eDiscovery access to the finance users emails, we need to create a scope using the New-ManagementScope cmdlet.
Topic 5, Proseware, Inc -
Overview -
General Overview -
Proseware, Inc., is an international manufacturing company that has 1,000 users.
Proseware has a sales department, a marketing department, a research department, and a human resources department.
Proseware purchases another company named Contoso, Ltd. Contoso has 500 users.
Physical Locations -
Proseware has two main offices located in New York and London.
The offices connect to each other by using a WAN link. Each office connects directly to the
Internet. Contoso has a single office in Dallas.
Existing Environment -
Active Directory Environment -
The Proseware network contains an Active Directory forest named proseware.com. The forest contains a single domain. All domain controllers run Windows Server 2012.
Each office contains three domain controllers. Each office is configured as an Active
Directory site.
The Contoso network contains an Active Directory forest named contoso.com. The forest contains a single domain. All domain controllers run Windows Server 2012.
Exchange Server Organization -
Proseware has an Exchange Server 2013 organization that contains four servers. The servers are configured as shown in the following table.
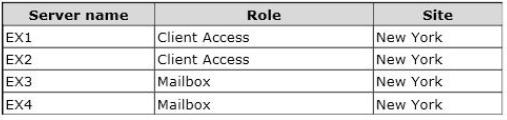
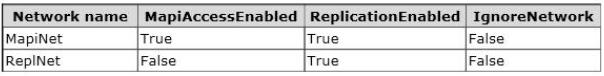
EX3 and EX4 are the members of a database availability group (DAG) named DAG1.
DAG1 has two DAG networks. The networks are configured as shown in the following table.
Users connect to mail.proseware.com for Microsoft Outlook and Outlook Web App services. Mail.proseware.com resolves to an IP address on a hardware load balancer.
All Outlook Anywhere users are enabled for Cached Exchange Mode.
Proseware pilots a hybrid deployment of Exchange Server 2013 and Microsoft Office 365.
The mailbox of each pilot user is moved to Office 365. For the pilot mailboxes, all inbound email messages from the Internet are delivered to the Exchange Server organization, and then forwarded to Office 365.
Contoso has an Exchange Server 2010 organization.
Problem Statements -
Proseware identifies the following issues:
-> MapiNet is saturated with network traffic caused by the database replication between the members of DAG1 over MapiNet.
-> The pilot users report that entries added to their Safe Senders list and their
Blocked Senders list fail to work.
-> A recent power outage in the New York office prevents all users from accessing their mailbox.
-> A user named User1 rep
Question 8
You are evaluating the deployment of two additional Client Access servers and a hardware load balancer in the London office.
You need to recommend changes to the Client Access namespace design to meet the site resiliency requirements.
Which three actions should you recommend? (Each correct answer presents part of the solution. Choose three.)
- A. In the London office, set mail.proseware.com as the external host name for Outlook Anywhere. In the New York office, set mail.proseware.com as the external host name for Outlook Anywhere.
- B. In the London office, set lonmail.proseware.com as the internal host name for Outlook Anywhere. In the New York office, set nycmail.proseware.com as the internal host name for Outlook Anywhere.
- C. Use DNS round robin for the external host name for Outlook Anywhere.
- D. Use DNS round robin for the internal host name for Outlook Anywhere.
- E. In the London office, set nycmail.proseware.com as the external host name for Outlook Anywhere. In the New York office, set lonmail.proseware.com as the external host name for Outlook Anywhere.
- F. In the London office, set mail.proseware.com as the internal host name for Outlook Anywhere. In the New York office, set mail.proseware.com as the internal host name for Outlook Anywhere.
Answer : ABC
Explanation:
A: Use mail.proseware.com as the external host name for Outlook Anywhere at both locations.
B: Use internal names (lonmail.proseware.com and nycmail.proseware.com) as the internal host name for Outlook Anywhere in London and New York respectively.
C: To meet the resiliency requirement use the external host name (mail.proseware.com) for
DNS round robin for Outlook anywhere.
* From scenario:
/ Users connect to mail.proseware.com for Microsoft Outlook and Outlook Web App services. Mail.proseware.com resolves to an IP address on a hardware load balancer.
/ All Outlook Anywhere users are enabled for Cached Exchange Mode.
/ Proseware has two main offices located in New York and London.
/
Site Resiliency Requirements -
- All mailboxes must be available if a single site becomes unavailable. The solution must not require administrator intervention.
- User traffic on the WAN links must be minimized.
* Split DNS for Exchange Server 2013
Split DNS allows your internal clients to receive a different answer to their DNS lookups than an external client would receive. In effect you have your Exchange namespace hosted on your internal DNS server, with records configured to point to internal IP addresses.
Question 9
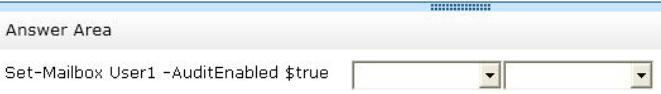
You need to recommend a solution to audit the issue of User1.
Which command should you recommend? (To answer, select the appropriate options in the answer area.)
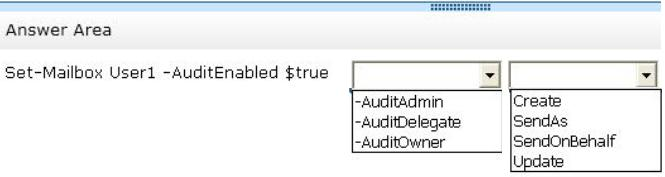
Answer : 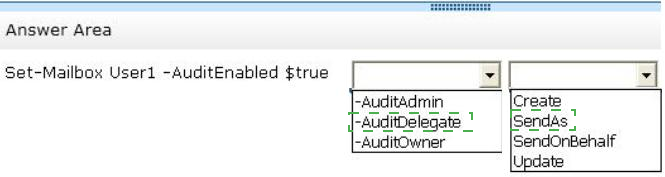
Explanation:
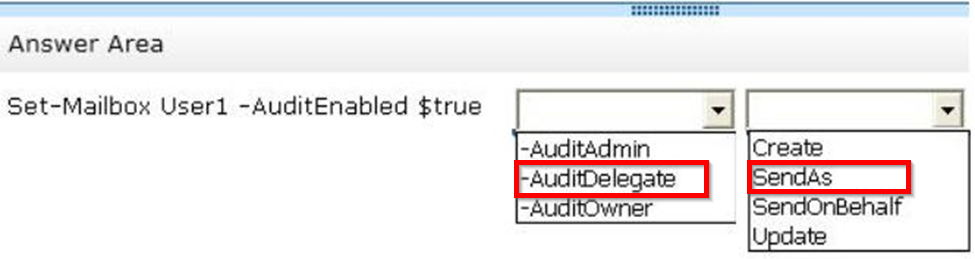
* Scenario: A user named User1 reports that email messages are being sent from her mailbox without her consent.
* Set-Mailbox AuditDelegate
The AuditDelegate parameter specifies the operations to log for delegate users.
Question 10
You need to recommend a solution to meet the technical requirements for redundancy during email delivery.
Which cmdlet should you include in the recommendation?
- A. Set-FrontendTransportService
- B. Set-TransportConfig
- C. Set-MailboxTransportService
- D. Set-TransportService
Answer : B
Explanation:
/ Internal email messages must be rejected if the messages cannot be protected by using
Shadow Redundancy -
We need to use the Set-TransportConfig cmdlet with the RejectMessageOnShadowFailure parameter.
Question 11
You need to resolve the network traffic issue for MapiNet.
You suspend database replication.
Which three cmdlets should you run next in sequence? (To answer, move the appropriate three cmdlets from the list of actions to the answer area and arrange them in the correct order.)
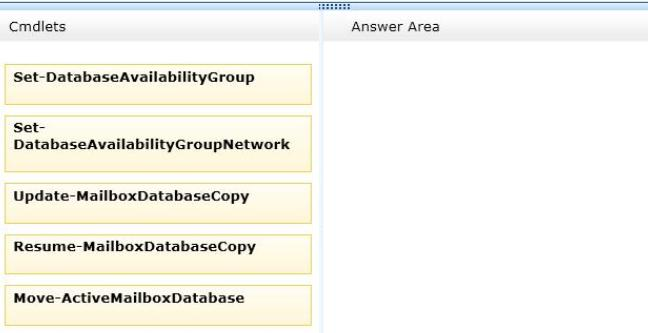
Answer : 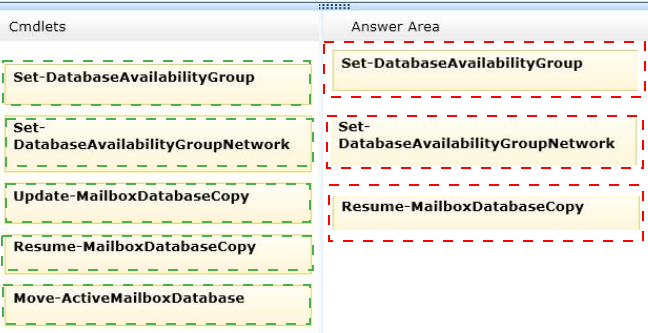
Question 12
You need to implement UM for the sales department users.
Which four commands should you run in sequence? (To answer, move the appropriate four commands from the list of commands to the answer area and arrange them in the correct order.)
Answer : 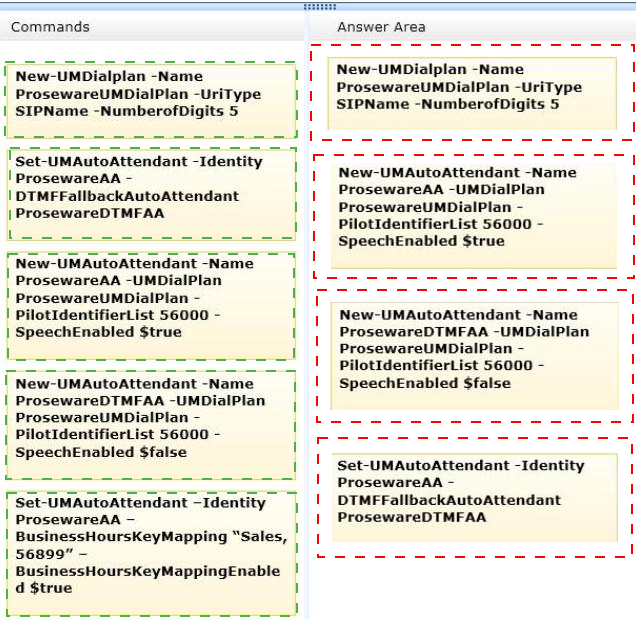
Question 13
You need to recommend a solution to support the planned changes for the integration of the Exchange Server organizations of Contoso and Proseware.
What should you configure in each organization? (To answer, drag the appropriate objects to the correct forests. Each object may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)
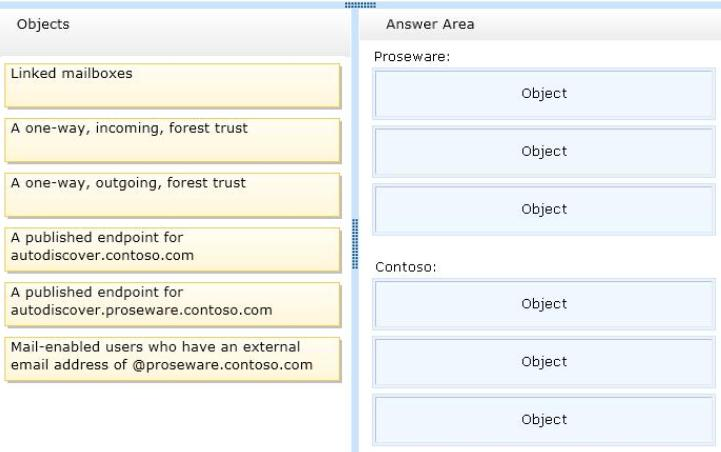
Answer : 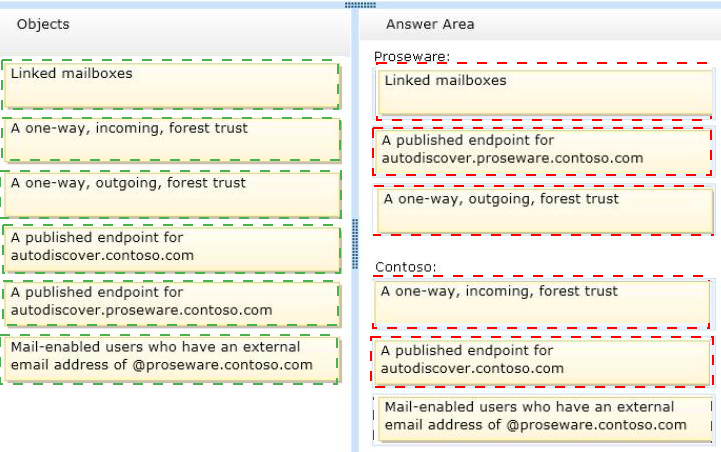
Question 14
You need to recommend a solution to audit the issue of User1.
Which command should you recommend? (To answer, select the appropriate options in the answer area.)
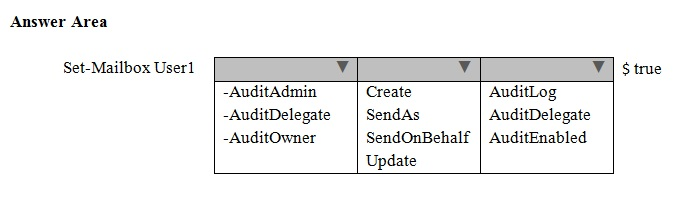
Answer : 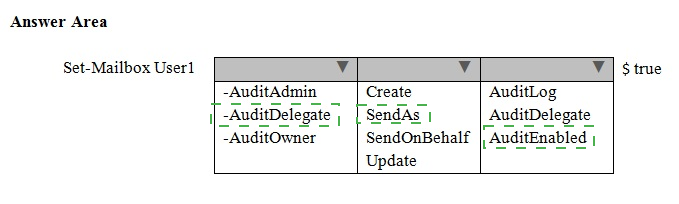
Explanation:
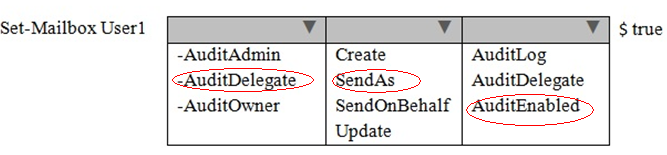
Scenario: A user named User1 reports that email messages are being sent from her mailbox without her consent.
For mailboxes in your organization that you wish to enable audit logging on you can do so using the Set-Mailbox cmdlet.
* The AuditDelegate parameter specifies the operations to log for delegate users. Valid values include:
None Update Move MoveToDeletedItems SoftDelete HardDelete FolderBind SendAs
SendOnBehalf -
* Send As
This permission allows delegates to use the mailbox to send messages. After this permission is assigned to a delegate, any message that the delegate sends from the mailbox will appear to have been sent by the mailbox owner.
Incorrect:
* Send on Behalf
This permission also allows a delegate to use the mailbox to send messages. After this permission is assigned to a delegate, the From address in any message sent by the delegate indicates that the message was sent by the delegate on behalf of the mailbox owner.
* The AuditEnabled parameter specifies whether to enable or disable mailbox audit logging.
If auditing is enabled, actions specified in the AuditAdmin, AuditDelegate, and AuditOwner parameters are logged. Valid values include:
$true
Mailbox audit logging is enabled.
$false
Mailbox audit logging is disabled.
The default value is $false.
Question 15
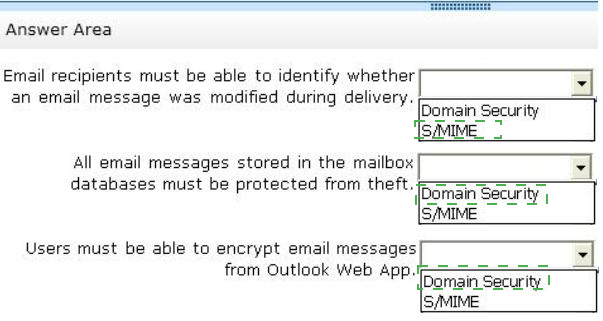
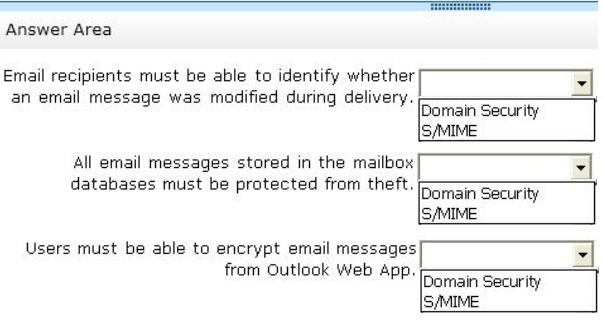
You need to recommend which technology can be used to meet each email security requirement.
What should you recommend? (To answer, select the appropriate technology for each requirement in the answer area.)
Answer :