Administering and Deploying System Center 2012 Configuration Manager v1.0
Question 1
Your network contains a System Center 2012 Configuration Manager environment.
You need to use the Configuration Manager console to identify service level agreement (SLA) issues among non-compliant clients.
What should you do?
- A. Configure a MicrosoftSQL Server Reporting Services (SSRS) report.
- B. Create an alert subscription.
- C. Configure an in-console alert.
- D. Create a ConfigMgr query.
Answer : C
Explanation:
Question 2
Your network contains a System Center 2012 R2 Configuration Manager Service Pack 1 (SP1) environment.
You need to create a report that lists all of the client computers that have an application named App1 installed.
Which query should you use to create the report?
- A. SELECT SYS.Netbios_Name0, ARP.DisplayName0FROM v_R_Sytem AS SYS INNER JOINv_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID =ARP.ResourceIDWHERE ARP.DisplayName0 NOT LIKE 'App1'
- B. SELECT SYS.Netbios_Name0 from v_R_System SYSWHERE SYS.ResourceID NOT IN(SELECT SYS.ResouceIDFROM v_R_System AS SYS INNER JOINv_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP.ResourceIDWHERE ARP.DisplayName0 = 'App1')
- C. SELECT SYS.Netbios_Name0, ARP.DisplayName0FROM v_R_Sytem AS SYS INNER JOINv_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP.ResourceIDWHERE ARP.DisplayName0 NOT IN('App1')
- D. SELECT SYS.Netbios_Name0 from v_R_System SYSWHERE SYS.ResourceID IN(SELECT SYS.ResouceIDFROM v_R_System AS SYS INNER JOINv_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP.ResourceIDWHERE ARP.DisplayName0 = 'App1')
Answer : D
Explanation:
SELECT computer name FROM table v_R_System (SQL Syntax)
WHERE resource ResourceID IN -
Add Remove Programs WHERE DisplayName0 = 'App1'
SQL INNER JOIN Keyword -
The INNER JOIN keyword returns rows when there is at least one match in both tables.
Question 3
Your network contains a System Center 2012 Configuration Manage environment.
The environment contains a primary site server named Server1 and a server named Server2 that runs Microsoft SQL Server 2008 R2.
Server2 contains the Configuration Managerdatabase.
Server2 fails.
You install SQL Server 2008 R2 on a new server.
You name the server Server3.
You need to restore the Configuration Manager database to Server3.
What should you do?
- A. Register the Service Principal Name (SPN) for the SQL Serverservice account of Server3. From Server1, run the Configuration Manager 2012 Setup Wizard.
- B. From Server3, run Microsoft SQL Server Management Studio, and then restore the backed up SQL Server database and log files.
- C. From Server3, run Microsoft SQL Server Management Studio, and then attach the backedup SQL Server database and log files.
- D. Register the Service Principal Name (SPN) for the SQL Server service account of Server3. From Server1, run the Site Repair Wizard.
Answer : A
http://technet.microsoft.com/en-us/library/gg712697.aspx
Backup and Recovery in Configuration Manager
Recover a Configuration Manager Site
A Configuration Manager site recovery is required whenever a Configuration Manager site fails or data loss occurs in the sitedatabase. Repairing and resynchronizing data arethe core tasks of a site recovery and are required to prevent interruption of operations. Site recovery is started by running the
Configuration Manager -
Setup Wizard from installation media or by configuring the unattended installation script and then using the Setup command /script option. Your recovery options vary depending on whether you have a backup of the Configuration Manager site database.
Site Database Recovery Options -
When you run Setup, you have the following recovery options for the site database:
* Recover the site database using a backup set: Use this option when you have a backup of the Configuration Manager site database that was created as part of the Backup Site Server maintenance task run onthe site before the site database failure. When you have a hierarchy, the changes that were made to the site database after the last site database backup are retrieved from the central administration site for a primary site, or from a reference primary site for a central administration site. When you recover the site database for a stand-alone primary site, you lose site changes after the last backup.
When you recover the site database for a site in a hierarchy, the recovery behavior is different for a central administration site and primary site, and when the last backup is inside or outside of the SQL Server change tracking retention period.
Question 4
Your network contains a System Center 2012 Configuration Manager environment.
The environment contains a single primary site.
The primary site has a distribution point and a management point.
You need to recommend a communication solution that meets the following requirements:
-> Communication between the client computes in the research department and the management point must use HTTPS.
-> Communication between all of the other client computers and the management point must be able to use HTTP.
-> Minimize the number of site system.
What should you do?
- A. Configure the existing management point to use HTTPS. Configure the research department computers always to use HTTPS.
- B. Create a new primary child site and configure the site to use native mode. Assign all of the research department computers to the new site.
- C. Install a new management point and configure the management point always to use HTTPS. Configure the research department computers always to use HTTPS.
- D. Install a new management point and configure Windows Firewall to block outbound TCP port 80. Configure the research department computes always to use HTTPS.
Answer : C
Explanation:
Create one additional management point that uses HTTPS, and configure research to use it.
Note: Optional Site System Roles
Optional site system roles are site system roles that are not required for the coreoperation of a Configuration Manager site. However, by default, the management point and distribution point, which are optional site system roles, are installed on the site server when you install a primary or secondary site. Although these two site systemroles are not required for the core operation of the site, you must have at least one management point to support clients at those locations. After you install a site, you can move the default location of the management point or distribution point to another server, install additional instances of each site system role, and install other optional site system roles to meet your business requirements. The optional site system roles are described in the following table:
A site system role that provides policyand service location information to clients and receives configuration data from clients.
You must install at least one management point at each primary site that manages clients, and at each secondary site where you want to provide a local point of contact for clients to obtain computer and user polices.
Question 5
Your network contains a System Center 2012 R2 Configuration Manager Service Pack 1 (SP1) environment.
Your company deploys 1,000 client computers.
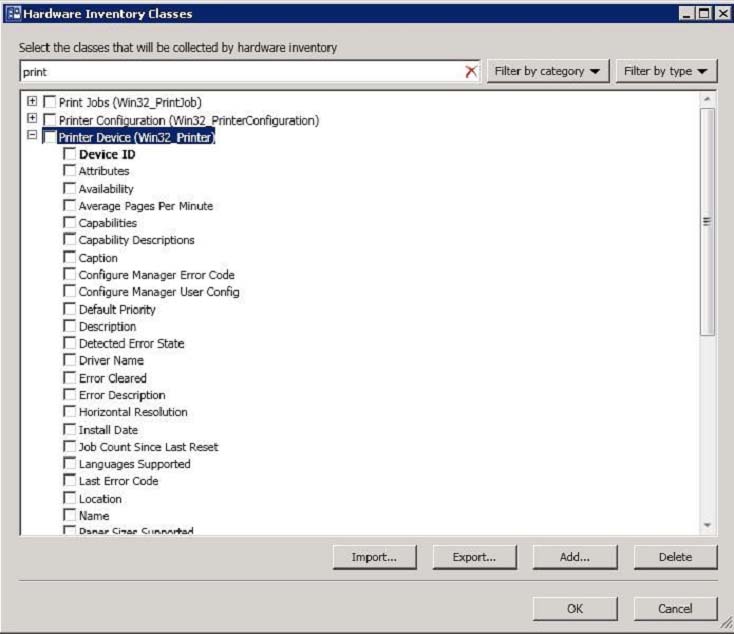
You discover that information about printers fails to appear in any inventory queries or reports.
Information about other hardware devices appears in the inventory queries and reports.
You need to ensure that Configuration Manager data includes information about the printers.
What should you do?
- A. Add a WMI class to the Hardware Inventory Classes list.
- B. Enable a default WMI class in the Hardware Inventory Classes list.
- C. Add a file name to the Software Inventory configuration.
- D. Add a file name to the Hardware inventory configuration.
- E. Add a file name to Software Metering.
- F. SelectCollect NOIDMIFfiles in Hardware Inventory.
- G. Add a WMI class to the Sms_def.mof file.
- H. Modify the Enable software inventory on clients setting.
- I. Modify the Enable hardware inventory on clientssetting.
Answer : B
Explanation:
How to Extend Hardware Inventory in Configuration Manager
System Center 2012 Configuration Manager hardware inventory reads information about devices by using Windows Management Instrumentation (WMI). WMI is the Microsoft implementation of web-based Enterprise Management (WBEM), which is an industry standard for accessing management information in an enterprise environment.
In previous versions of Configuration Manager, you could extend hardware inventory by modifying the file sms_def.mof onthe site server.
In System Center 2012 Configuration Manager, you no longer edit the sms_def.mof file as you did in Configuration Manager 2007. Instead, you can enable and disable WMI classes, and add new classes to collect by hardware inventory by using client settings. Configuration Manager provides the following methods to extend hardware inventory:
Enable or disable existing inventory classes - You can enable or disable the default inventory classes used by Configuration Manager or you can create custom client settings that allow you to collect different hardware inventory classes from specified collections of clients.
Add a new inventory class - You can add a new inventory class from the WMI namespace of another device.
Import and export hardware inventory classes - You can import and export Managed Object Format
(MOF) files that contain inventory classes from the Configuration Manager console.
Create NOIDMIF Files - Use NOIDMIF files to collect information about client devices that cannot be inventoried by Configuration Manager.
Create IDMIF Files - Use IDMIF files to collect information about assets in your organization that are not associated with a Configuration Manager client, for example, projectors, photocopiers and networkprinters.
Note:
References: How to Extend Hardware Inventory in Configuration Manager http://technet.microsoft.com/en-us/library/gg712290.aspx
Question 6
Your network contains a System Center 2012 Configuration Manager environment.
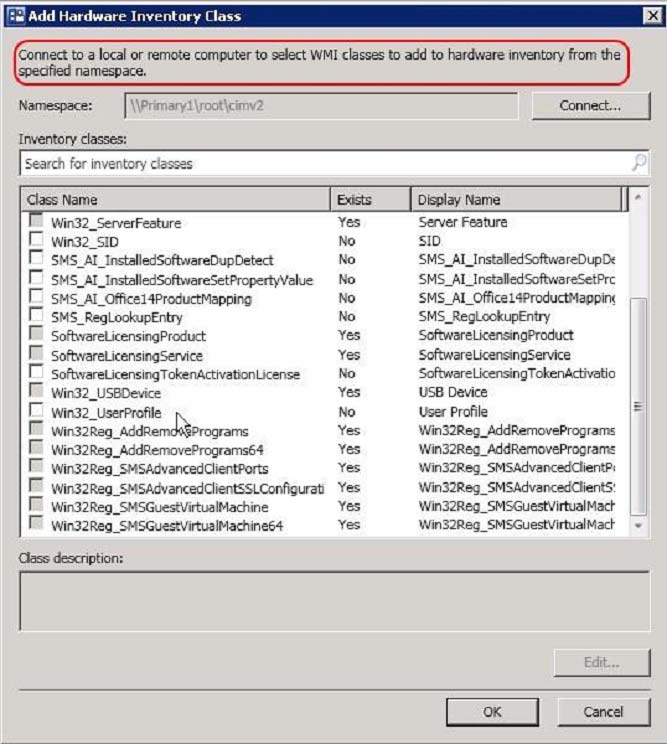
Your company develops a custom hardware device and installs the device on all of the client computers in the research department.
You discover that information about the device fails to appear in any inventory queries or reports.
Information about other hardware devices appears in the inventory queries and reports.
You need to ensure that Configuration Manager data include information about the custom hardware device.
What should you do?
- A. Enable a default WMI class in the Hardware Inventory Classes list.
- B. Modify the Enable hardware inventory on clients setting.
- C. Add a WMI class to the Hardware inventory Classes list.
- D. Add a file name to the Software Inventory configuration.
- E. Select Collect NOIDMIF files in Hardware Inventory.
- F. Add a file name to the Hardware inventory configuration.
- G. Add a file name to Software Metering.
- H. Add a WMI class to the Sms_def.mof file.
- I. Modify the Enable software inventory on clients setting.
Answer : C
Explanation:
How to Extend Hardware Inventory in Configuration Manager
System Center 2012 Configuration Manager hardware inventory reads information about devices by using Windows Management Instrumentation (WMI). WMI is the Microsoft implementation of web-based Enterprise Management (WBEM), which is an industry standard foraccessing management information in an enterprise environment.
In previous versions of Configuration Manager, you could extend hardware inventory by modifying the file sms_def.mof on the site server.
In System Center 2012 Configuration Manager, you no longer edit the sms_def.mof file as you did in Configuration Manager 2007. Instead, you can enable and disable WMI classes, and add new classes to collect by hardware inventory by using client settings. Configuration Manager provides the following methods to extend hardware inventory:
Enable or disable existing inventory classes - You can enable or disable the default inventory classes used by Configuration Manager or you can create custom client settings that allow you to collect different hardware inventory classes from specified collections of clients.
Add a new inventory class - You can add a new inventory class from the WMI namespace of another device.
References: Reference: How to Extend Hardware Inventory in Configuration Manager http://technet.microsoft.com/en-us/library/gg712290.aspx
Question 7
Your network contains a System Center 2012 Configuration Manager environment.
Your company deploys a custom Application to 2,000 client computers by using Configuration Manager.
The Application is not listed in Add Remove Programs.
You discover that information about the Application fails to appear in the inventory queries and inventory reports.
You verify that information about other Applications appear in the inventory reports.
You need to ensure that Configuration Manager data includes installation information about the custom Application.
What should you do?
- A. Add a file name to Software Metering.
- B. Add a WMI class to the Hardware Inventory Classes file.
- C. Add a file name to the Hardware Inventory configuration.
- D. Enable a default WMI Cass in the Hardware Inventory Classes list.
- E. SelectCollect NOIDMIF filesin Hardware Inventory.
- F. Add a file name to the Software Inventory configuration.
- G. Modify the Enablehardware inventory on Cents setting.
- H. Add a WMI class to the Sms_def.mof file.
Answer : F
Explanation:
Introduction to Software Inventory in Configuration Manager
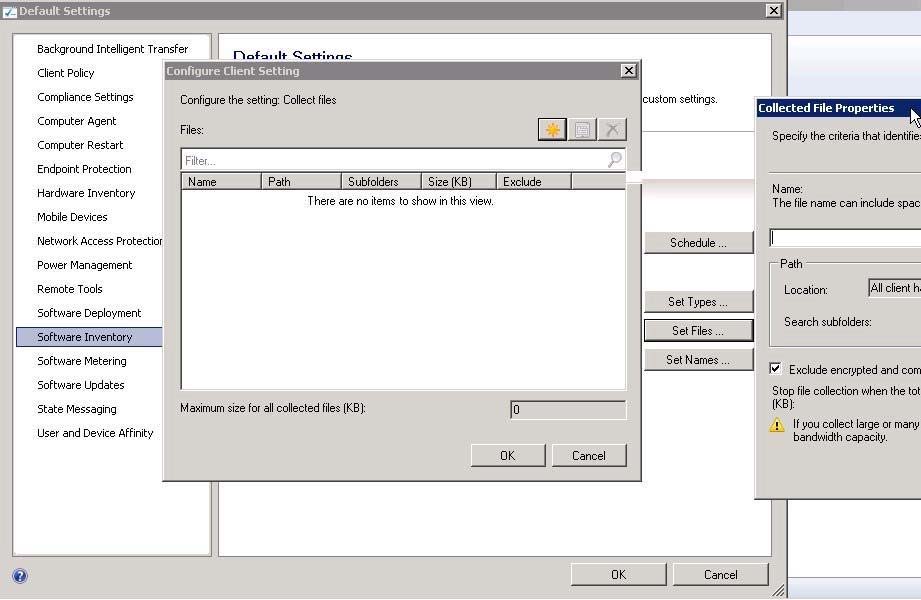
Use software inventory inSystem Center 2012 Configuration Manager to collect information about files that are contained on client devices in your organization.
Additionally, software inventory can collect files from client devices and store these on the site server. Software inventory is collected when the Enable software inventory on clients setting is enabled in client settings.
Note:
References: Introduction to Software Inventory in Configuration Manager http://technet.microsoft.com/en-us/library/gg682049.aspx
Question 8
Your network contains a System Center 2012 Configuration Manager environment.
Your company deploys a third-party Application to 10,000 client computers.
You need to ensure that you can run a report that lists all of the client computers that ran the Application last month.
What should you do?
- A. Modify the Enable hardware inventory on clients setting.
- B. Enable a default WMI class in the Hardware Inventory Classes list.
- C. Modify the Enable software inventory on clients setting.
- D. Add a file nameto the Hardware Inventory configuration.
- E. Add a WMI class to theHardware Inventory Classes list.
- F. Add a file name to the Software Inventory configuration.
- G. Add a file name to Software Metering.
- H. Add a WMI class to the Sms_def.mof file.
- I. Select Collect NOIDMIF files in Hardware Inventory.
Answer : G
Explanation:
Introduction to Software Metering in Configuration Manager
Use software metering in System Center 2012 Configuration Manager to monitor and collect software usage data from Configuration Manager clients.
To collect this usage data, configure software metering rules or use the Configuration Manager inventory to generate these rules automatically. Client computers evaluate these rules and collect metering data to send to the site.
Question 9
Your network contains a System Center 2012 R2 Configuration Manager Service Pack 1 (SP1) environment.
You need to create a report that lists all of the client computers that do not have an Application named App1 installed.
Which query should you use to create the report?
- A. SELECTSYS.Netbios_Name0, ARP.DisplayName0FROM v_R_System AS SYS INNER JOINv_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP. ResourceID WHERE ARP.DisplayName0 NOT IN ('App1')
- B. SELECT SYS.Netbios_Name0 from v_R_System SYSWHERE SYS.ResourceID IN(SELECT SYS.ResourceIDFROM v_R_System ASSYS INNER JOINv_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID - ARP.ResourceID. WHERE ARP.DisplayName0 = 'App1')
- C. SELECT SYS.Netbios_Name0 from v_R_System SYSWHERE SYS.ResourceID NOT IN(SELECT SYS.ResourceIDFROM v_R_SystemAS SYS INNER JOINv_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID = ARP.ResourceID WHERE ARP.DisplayName0 = 'App1')
- D. SELECT SYS.Netbios_Name0, ARP.DisplayName0FROM v_R_System AS SYS INNER JOINV_GS_ADD_REMOVE_PROGRAMS AS ARP ON SYS.ResourceID - ARP.ResourceID WHERE ARP.DisplayName0NOT LIKE 'App1'
Answer : C
Explanation:
SELECT computer name FROM table v_R_System (SQL Syntax)
WHERE resource ResourceID is NOT IN
Add Remove Programs WHERE DisplayName0 = 'App1'
SQL INNER JOIN Keyword -
The INNER JOINkeyword returns rows when there is atleast one match in both tables.
Question 10
Your network contains a System Center 2012 Configuration Manager environment.
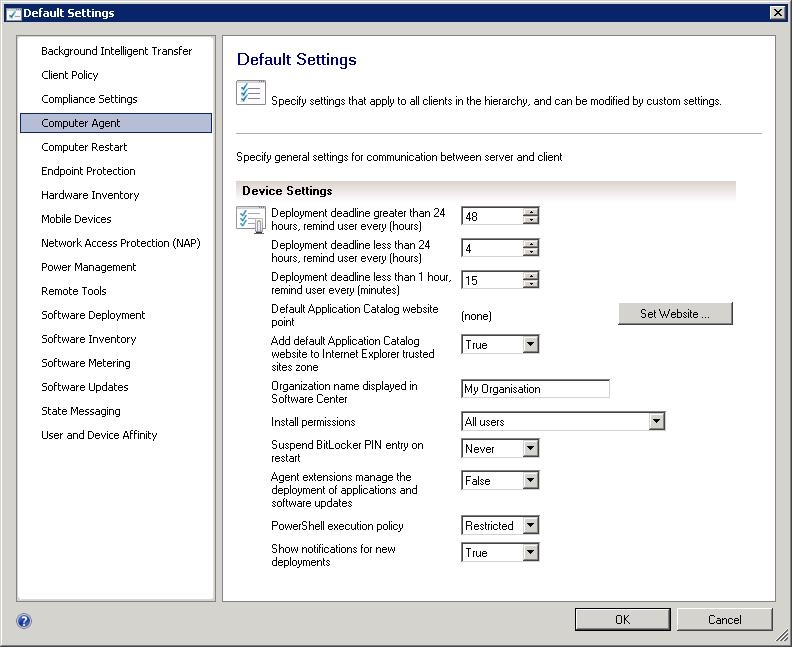
You need to change the organization name displayed by Configuration Manager.
Which settings should you modify from the Configuration Manager console?
- A. Client Policy
- B. Computer Agent
- C. User and Device Affinity
- D. Compliance Settings
Answer : B
Explanation:
Administration -> Client Settings -> Default Client Settings -> Computer Agent
Question 11
Your network contains a System Center 2012 Configuration Manager environment.
In Default Client Agent Settings, you enable Hardware Inventory and Software Inventory.
You discover that a group of client computers fails to report software inventory data.
The client computers report hardware inventory data.
You confirm that Configuration Manager can deploy Applications to the group of client computers.
You need to identify what is causing the reporting issue.
Which log files should you review? (Choose all that Apply.)
- A. Filesystemfile.log
- B. Dataldr.log
- C. Mp_sinv.log
- D. Inventoryagent.log
- E. Hman.log
Answer : ABD
Explanation:
A: FileSystemFile.log is a client log file that records the activity of the Windows Management Instrumentation (WMI) provider for software inventory and file collection.
B: Dataldr.log is a site server log file that records information about the processing of Management Information Format (MIF) files and hardware inventory in the
Configuration Manager database.
D: Inventoryagent.log is a client log file that records activities of hardware inventory, software inventory, and heartbeat discovery actions on the client.
Question 12
Your network contains a System Center 2012 R2 Configuration Manager Service Pack 1 (SP1) environment.
The network contains 10 database servers that run Microsoft SQL Server 2014. You have a configuration baseline that is used to monitor the database servers.
You add new configuration items to the configuration baseline.
Two days later, you discover that only eight of the database servers report any information about the new configuration items.
You need to identify whether the new configuration items downloaded to the database servers.
Which log file should you review?
- A. Hman.log
- B. Sitestat.log
- C. Dcmagent.log
- D. Wsyncmgr.log
- E. Ccm.log
- F. Contenttransfermanager.log
- G. Sdmagent.log
- H. Rcmctrl.log
- I. Ciagent.log
- J. Smsexec.log K. Locationservices.log
Answer : I
Explanation:
Ciagent.log is a client log file that records details about the process ofremediation and compliance for compliance settings, software updates, and application management.
Question 13
You create a deployment to install Microsoft Office 2013 The deployment targets 5,000 client computers on the network.
Two weeks after you create the deployment, you discover that Office 2013 fails to install on a client computer named Computer 1.
You need to identify whether Computer1 started downloading the Application of Office 2013.
Which log file should you review?
- A. Locationservices.log
- B. Ccm.log
- C. Sdmagent.log
- D. Sitestat.log
- E. Rcmctrl.log
- F. Dcmagent.log
- G. Contenttransfermanager.log
- H. Smsexec.log
- I. Wsyncmgr.log
- J. Ciagent.log K. Hman.tog
Answer : G
Explanation:
ContentTransferManager.log is a client log file that schedules the Background Intelligent Transfer Service (BITS) or the Server Message Block (SMB) to download or to access packages.
Question 14
Your network contains a System Center 2012 Configuration Management environment.
The environment contains a Central Administration site and two primary child sites named Child1 and Child2.
You create a new Application on the Central Administration site.
You view the new Application on Child1, but the new Application fails to appear on Child2.
You need to identify whether the Application transferred to Child2.
Which log file should you review?
- A. Locationservices.log
- B. Smsexec.log
- C. Ccm.log
- D. Sdmagent.log
- E. Dcmagent.log
- F. Rcmctrl.log
- G. Wsyncmgr.log
- H. Ciagent.log
- I. Hman.log
- J. Contenttransfermanager.log K. Sitestat.log
Answer : F
Explanation:
Rcmctrl.log is a site server log file that records the activities of database replication between sites in the hierarchy.
Question 15
Your network contains a System Center 2012 Configuration Manager environment.
You create two custom client agent settings named ClientSettings1 and ClientSettings2. You apply ClientSettings1 to all of the client computers in the sales department. You apply ClientSettings2 to all of the client computers in the marketing department.
The client computers in the marketing department contain several custom registry settings.
You need to collect the custom registry settings from the marketing department computers.
What should you do?
- A. Edit the default client agent settings and include the custom registry information
- B. Edit ClientSettings2 and exclude the custom registry information.
- C. Create a new set of custom client agent settings for the marketing department and include the custom registry information.
- D. Edit ClientSettings2 andinclude the custom registry information.
Answer : C
Explanation:
It is common sense, that you just add another client setting and deploy it to the collection.
Why? All settings can be separately deleted and especially named. Easier to handle.