Securing Cisco Networks with Threat Detection and Analysis v6.0
Question 1
Refer to the exhibit.
Based on the tcpdump output, which two statements are true? (Choose two.)
- A. The reply is sent via unicast.
- B. All devices in the same subnet on a switched network will see the reply because it was broadcast.
- C. The device is coming up for the first time and is requesting an IP address.
- D. The ARP request is being sent as a broadcast.
- E. The device is requesting an ARP.
- F. Host 192.168.10.7 is requesting the operational status of host 192.168.10.8.
Answer : A,D
Question 2
Refer to the exhibit.

Which two options does the following tcpdump command do? (Choose two.)
- A. Read from nvram (non-volatile) and parse the stream.
- B. Capture traffic based on host 10.10.10.10 and HTTP traffic.
- C. Capture traffic based on host 10.10.10.10 and everything but HTTP traffic.
- D. Capture ARP traffic only.
- E. Write the capture as a file.
- F. Read the capture from a file.
Answer : C,E
Question 3
What is the maximum size of an IP datagram?
- A. There is no maximum size.
- B. It is limited only by the memory on the host computers at either end of the connection and the intermediate routers.
- C. 1024 bytes
- D. 65535 bytes
- E. 32768 bytes
Answer : D
Question 4
The IHL is a 4-bit field containing what measurement?
- A. the number of 32-bit words in the IP header
- B. the size of the IP header, in bytes
- C. the size of the entire IP datagram, in bytes
- D. the number of bytes in the IP header
- E. the number of 32-bit words in the entire IP datagram
Answer : A
Question 5
What is the purpose of the TCP SYN flag?
- A. to sequence each byte of data in a TCP connection
- B. to synchronize the initial sequence number contained in the Sequence Number header field with the other end of the connection
- C. to acknowledge outstanding data relative to the byte count contained in the Sequence Number header field
- D. to sequence each byte of data in a TCP connection relative to the byte count contained in the Sequence Number header field
Answer : B
Question 6
Refer to the exhibit.
What does the tcpdump command do?
- A. Capture all packets sourced from TCP port 1514, resolve DNS names, print all TCP packets with the SYN flag not equaling 0, and print the Ethernet header and all version information.
- B. Capture all packets sourced from TCP port 1514, resolve DNS names, print all TCP packets except those containing the SYN flag, and print the Ethernet header and all version information.
- C. Capture up to 1514 bytes, do not resolve DNS names, print all TCP packets except for those containing the SYN flag, and print the Ethernet header and be very verbose.
- D. Capture up to 1514 bytes, do not resolve DNS names, print only TCP packets containing the SYN flag, and print the Ethernet header and be very verbose.
Answer : D
Question 7
Refer to the exhibit.
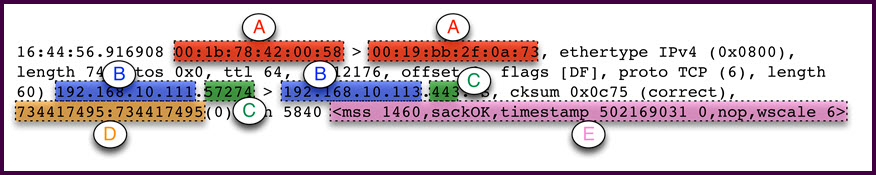
In the packet captured from tcpdump, which fields match up with the lettered parameters?
- A. A.Source and destination IP addresses,B.Source and destination Ethernet addresses,C.Source and destination TCP port numbers,D.TCP acknowledgement number,E.IP options
- B. A.Source and destination Ethernet addresses,B.Source and destination IP addresses,C.Source and destination TCP port numbers,D.TCP sequence number,E.TCP options
- C. A.Source and destination Ethernet addresses,B.Source and destination IP addresses,C.Source and destination TCP port numbers,D.TCP acknowledgement number,E.IP options
- D. A.Source and destination Ethernet addresses,B.Source and destination IP addresses,C.Source and destination TCP port numbers,D.TCP sequence number,E.IP options
Answer : B
Question 8
For TCP and UDP, what is the correct range of well-known port numbers?
- A. 0 - 1023
- B. 1 - 1024
- C. 1 - 65535
- D. 0 - 65535
- E. 024 - 65535
Answer : A
Question 9
Which three symptoms are best used to detect a TCP SYN flood attack? (Choose three.)
- A. high memory utilization on target server
- B. large number of sockets in SYN_RECV state on target server
- C. network monitoring devices report large number of unACKed SYNs sent to target server
- D. target server crashes repeatedly
- E. user experience with target server is slow or unresponsive
Answer : B,C,E
Question 10
Which two statements about the IPv4 TTL field are true? (Choose two.)
- A. If the TTL is 0, the datagram is automatically retransmitted.
- B. Each router that forwards an IP datagram reduces the TTL value by one.
- C. It is used to limit the lifetime of an IP datagram on the Internet.
- D. It is used to track IP datagrams on the Internet.
Answer : BC
Question 11
What are four steps to manage incident response handling? (Choose four.)
- A. preparation
- B. qualify
- C. identification
- D. who
- E. containment
- F. recovery
- G. eradication
- H. lessons learned
Answer : A,C,E,H
Question 12
What does the acronym "CSIRT" stand for?
- A. Computer Security Identification Response Team
- B. Cisco Security Incident Response Team
- C. Cisco Security Identification Response Team
- D. Computer Security Incident Response Team
Answer : D
Question 13
Which publication from the ISO covers security incident response?
- A. 1918
- B. 2865
- C. 27035
- D. 25012
Answer : C
Question 14
As a part of incident response, which action should be performed?
- A. watch to see if the incident reoccurs
- B. custody of information
- C. maintain data security and custody for future forensics use
- D. classify the problem
Answer : C
Question 15
Which action is recommended to prevent an incident from spreading?
- A. Shut down the switch port.
- B. Reboot the system.
- C. Reboot the switch.
- D. Reboot the router.
Answer : A