EC-Council Certified Security Analyst (ECSA) v10.3
Question 1
Which of the following contents of a pen testing project plan addresses the strengths, weaknesses, opportunities, and threats involved in the project?
- A. Project Goal
- B. Success Factors
- C. Objectives
- D. Assumptions
Answer : D
Question 2
Identify the attack represented in the diagram below:
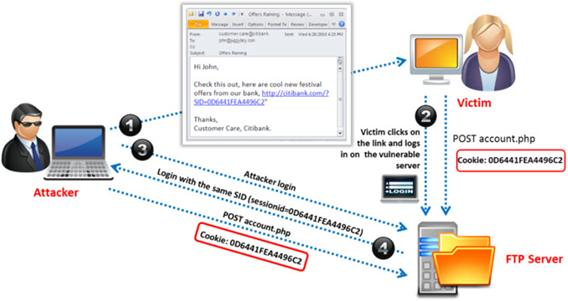
- A. Input Validation
- B. Session Hijacking
- C. SQL Injection
- D. Denial-of-Service
Answer : B
Reference:http://en.wikipedia.org/wiki/Session_hijacking
Question 3
If a web application sends HTTP cookies as its method for transmitting session tokens, it may be vulnerable which of the following attacks?
- A. Parameter tampering Attack
- B. Sql injection attack
- C. Session Hijacking
- D. Cross-site request attack
Answer : D
Reference:https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
Question 4
DNS information records provide important data about:
- A. Phone and Fax Numbers
- B. Location and Type of Servers
- C. Agents Providing Service to Company Staff
- D. New Customer
Answer : B
Question 5
Which of the following has an offset field that specifies the length of the header and data?
- A. IP Header
- B. UDP Header
- C. ICMP Header
- D. TCP Header
Answer : D
Question 6
Identify the type of firewall represented in the diagram below:
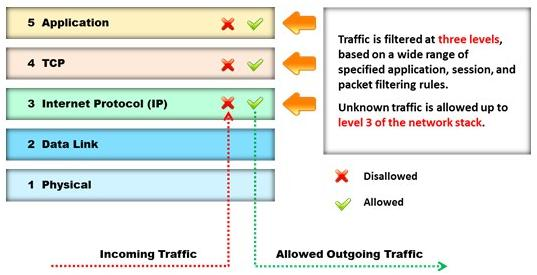
- A. Stateful multilayer inspection firewall
- B. Applicationlevel gateway
- C. Packet filter
- D. Circuit level gateway
Answer : A
Reference:http://www.technicolorbroadbandpartner.com/getfile.php?id=4159(page 13)
Question 7
The firstand foremost step for a penetration test is information gathering. The main objective of this test is to gather information about the target system which can be used in a malicious manner to gain access to the target systems.

Which of the following information gathering terminologies refers to gathering information through social engineering on-site visits, face-to-face interviews, and direct questionnaires?
- A. Active Information Gathering
- B. Pseudonymous Information Gathering
- C. Anonymous InformationGathering
- D. Open Source or Passive Information Gathering
Answer : A
Question 8
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
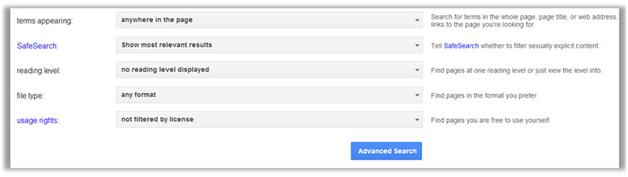
Which search keywords would you use in the Google search engine to find all the
PowerPoint presentations containing information about a target company, ROCHESTON?
- A. ROCHESTON fileformat:+ppt
- B. ROCHESTON ppt:filestring
- C. ROCHESTON filetype:ppt
- D. ROCHESTON +ppt:filesearch
Answer : C
Reference:http://blog.hubspot.com/blog/tabid/6307/bid/1264/12-Quick-Tips-To-Search-
Google-Like-An-Expert.aspx(specific document types)
Question 9
Wireless communication allows networks to extend to places that might otherwise go untouched by the wired networks. When most peoplesay Wireless these days, they are referring to one of the 802.11 standards. There are three main 802.11 standards: B, A, and
G. Which one of the following 802.11 types uses DSSS Modulation, splitting the 2.4ghz band into channels?
- A. 802.11b
- B. 802.11g
- C. 802.11-Legacy
- D. 802.11n
Answer : A
Question 10
What is the difference between penetration testingand vulnerability testing?
- A. Penetration testing goes one step further than vulnerability testing; while vulnerability tests check for known vulnerabilities, penetration testing adopts the concept of in-depth ethical hacking
- B. Penetration testingis based on purely online vulnerability analysis while vulnerability testing engages ethical hackers to find vulnerabilities
- C. Vulnerability testing is more expensive than penetration testing
- D. Penetration testing is conducted purely for meeting compliance standards while vulnerability testing is focused on online scans
Answer : A
Question 11
This is a group of people hired to give details of the vulnerabilities present in the system found after a penetration test. They are elite and extremely competent penetration testers and intrusion analysts. This team prepares a report on the vulnerabilities in the system,attack methods, and how to defend against them.

What is this team called?
- A. Blue team
- B. Tiger team
- C. Gorilla team
- D. Lion team
Answer : B
Question 12
Identify the type of testing that is carried out without giving any information to the employees or administrative head of the organization.
- A. Unannounced Testing
- B. Double Blind Testing
- C. Announced Testing
- D. Blind Testing
Answer : B
Question 13
Which of the following methods is used to perform server discovery?
- A. Banner Grabbing
- B. Whois Lookup
- C. SQL Injection
- D. SessionHijacking
Answer : B
Reference:http://luizfirmino.blogspot.com/2011/09/server-discovery.html
Question 14
Which among the following information is not furnished by the Rules of Engagement (ROE) document?
- A. Techniques for data collection from systems upon termination of the test
- B. Techniques for data exclusion from systems upon termination of the test
- C. Details on how data should be transmitted during and after the test
- D. Details on how organizational data is treated throughout and after the test
Answer : A
Question 15
Snort, an open source network-based intrusion detection sensor, is the most widely installed NIDS in the world. It can be configured to run in the four modes. Which one of the following modes reads the packets off the network and displays them in a continuous stream on the console (screen)?
- A. Packet Sniffer Mode
- B. Packet Logger Mode
- C. Network Intrusion Detection System Mode
- D. Inline Mode
Answer : A