EC-Council Certified Security Analyst (ECSA) v8.0
Question 1
Jonathan is a network administrator who is currently testing the internal security of his network. He is attempting to hijack a session, using Ettercap, of a user connected to his
Web server. Why will Jonathan not succeed?
- A. Only an HTTPS session can be hijacked
- B. Only DNS traffic can be hijacked
- C. Only FTP traffic can be hijacked
- D. HTTP protocol does not maintain session
Answer : D
Question 2
What is a good security method to prevent unauthorized users from "tailgating"?
- A. Electronic key systems
- B. Man trap
- C. Pick-resistant locks
- D. Electronic combination locks
Answer : B
Question 3
If an attacker's computer sends an IPID of 31400 to a zombie computer on an open port in
IDLE scanning, what will be the response?
- A. 31401
- B. The zombie will not send a response
- C. 31402
- D. 31399
Answer : A
Question 4
What is the following command trying to accomplish?
- A. Verify that TCP port 445 is open for the 192.168.0.0 network
- B. Verify that UDP port 445 is open for the 192.168.0.0 network
- C. Verify that UDP port 445 is closed for the 192.168.0.0 network
- D. Verify that NETBIOS is running for the 192.168.0.0 network
Answer : B
Question 5
What will the following URL produce in an unpatched IIS Web Server?
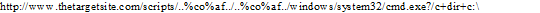
- A. Execute a buffer flow in the C: drive of the web server
- B. Insert a Trojan horse into the C: drive of the web server
- C. Directory listing of the C:\windows\system32 folder on the web server
- D. Directory listing of C: drive on the web server
Answer : D
Question 6
When setting up a wireless network with multiple access points, why is it important to set each access point on a different channel?
- A. Avoid cross talk
- B. Avoid over-saturation of wireless signals
- C. So that the access points will work on different frequencies
- D. Multiple access points can be set up on the same channel without any issues
Answer : A
Question 7
A packet is sent to a router that does not have the packet destination address in its route table, how will the packet get to its properA packet is sent to a router that does not have the packet? destination address in its route table, how will the packet get to its proper destination?
- A. Root Internet servers
- B. Border Gateway Protocol
- C. Gateway of last resort
- D. Reverse DNS
Answer : C
Question 8
Larry is an IT consultant who works for corporations and government agencies. Larry plans on shutting down the city's network using BGP devices and ombies? What type of
Penetration Testing is Larry planning to carry out?
- A. Internal Penetration Testing
- B. Firewall Penetration Testing
- C. DoS Penetration Testing
- D. Router Penetration Testing
Answer : C
Question 9
You are a security analyst performing reconnaissance on a company you will be carrying out a penetration test for. You conduct a search for IT jobs on Dice.com and find the following information for an open position:
7+ years experience in Windows Server environment
5+ years experience in Exchange 2000/2003 environment
Experience with Cisco Pix Firewall, Linksys 1376 router, Oracle 11i and MYOB v3.4
Accounting software are required MCSA desired,
MCSE, CEH preferred -
No Unix/Linux Experience needed -
What is this information posted on the job website considered?
- A. Information vulnerability
- B. Social engineering exploit
- C. Trade secret
- D. Competitive exploit
Answer : A
Question 10
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
- A. Filtered
- B. Stealth
- C. Closed
- D. Open
Answer : D
Question 11
John and Hillary works at the same department in the company. John wants to find out
Hillary's network password so he can take a look at her documents on the file server. He enables Lophtcrack program to sniffing mode. John sends Hillary an email with a link to
Error! Reference source not found. What information will he be able to gather from this?
- A. The SID of Hillary's network account
- B. The network shares that Hillary has permissions
- C. The SAM file from Hillary's computer
- D. Hillary's network username and password hash
Answer : D
Question 12
Terri works for a security consulting firm that is currently performing a penetration test on
First National Bank in Tokyo. Terri's duties include bypassing firewalls and switches to gain access to the network. Terri sends an IP packet to one of the company's switches with
ACK bit and the source address of her machine set. What is Terri trying to accomplish by sending this IP packet?
- A. Poison the switch's MAC address table by flooding it with ACK bits
- B. Enable tunneling feature on the switch
- C. Trick the switch into thinking it already has a session with Terri's computer
- D. Crash the switch with a DoS attack since switches cannot send ACK bits
Answer : C
Question 13
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
- A. 2.4 Ghz Cordless phones
- B. Satellite television
- C. CB radio
- D. Computers on his wired network
Answer : A
Question 14
You have compromised a lower-level administrator account on an Active Directory network of a small company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of the Domain Controllers on port 389 using ldp.exe.
What are you trying to accomplish here?
- A. Enumerate domain user accounts and built-in groups
- B. Establish a remote connection to the Domain Controller
- C. Poison the DNS records with false records
- D. Enumerate MX and A records from DNS
Answer : A
Question 15
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the axfr and ixfr commands using DIG. What is Simon trying to accomplish here?
- A. Perform a zone transfer
- B. Perform DNS poisoning
- C. Send DOS commands to crash the DNS servers
- D. Enumerate all the users in the domain
Answer : A