CCIE Wireless Written Exam v1.0
Question 1
You have received a new Cisco 5760 Controller and have gone through the initial startup wizard. You are now trying to add APs to the controller, but these are not joining. Which three checks should you do next? (Choose three.)
- A. Check that the correct time is set on the controller.
- B. Check that the controller has enough AP licenses.
- C. Check that the controller has enough AP licenses.
- D. Check that option 53 has been set in the DHCP scope.
- E. Check that the radios are not in a shutdown state.
- F. Check the country code of the controller. The APs do not join the controller if the country code does not match.
Answer : BCE
Reference:
http://www.cisco.com/c/en/us/support/docs/wireless/2500-series-wireless-controllers/113034-2500-deploy-guide-00.html#anc10
Question 2
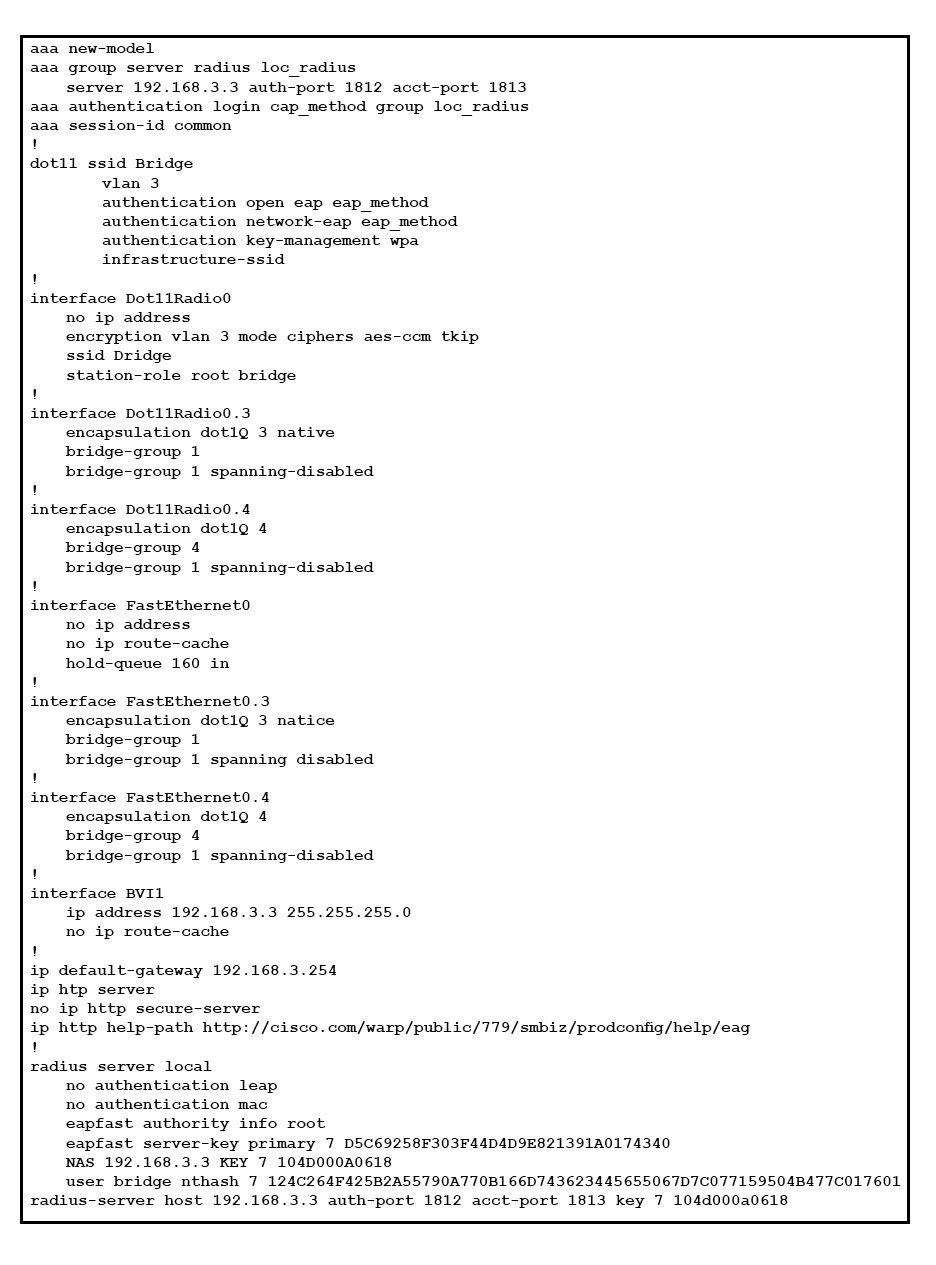
Refer to the exhibit. Which three statements about this extract of the configuration of an autonomous AP are true? (Choose three.)
- A. The administrator cannot access the AP via the web GUI using a secure connection.
- B. This configuration is of a non-root bridge access point.
- C. The RADIUS server IP address is misconfigured. It points to the AP itself, which creates a loop for the RADIUS packets.
- D. The SSID is not visible for clients probing the wireless medium.
- E. This configuration allows bridging of VLANs 3 and 4.
- F. The native VLAN must be VLAN 1 to match the native VLAN configured on the switch to which the AP is connecting.
Answer : ACE
Explanation:
Question 3
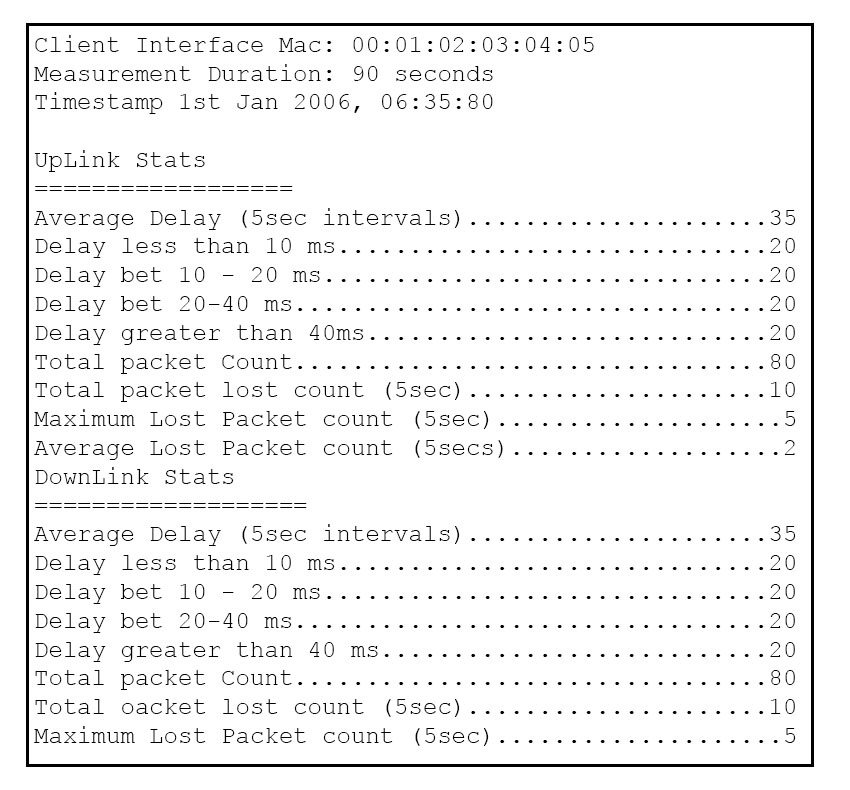
Refer to the exhibit. Which feature (and associated show output) is seen here?
- A. Controller>show client detail 00:01:02:03:04:05
- B. Controller> show client wmm 802.11 a 00:01:02:03:04:05 all
- C. Controller> show app stats 802.11 a 00:01:02:03:04:05
- D. Controller> show client tsm 802.11 a 00:01:02:03:04:05 all
Answer : D
Reference:
http://www.cisco.com/en/US/docs/wireless/controller/7.4/configuration/guides/system_management/ config_system_management_chapter_010000.html
Question 4
When connecting an autonomous access point in workgroup bridge mode to a WLAN configured on a Cisco WLC, which two options are true? (Choose two.)
- A. The WGB could serve wireless clients only in the other radio not connecting to the WLAN.
- B. The WGB creates a network extension for the wired clients.
- C. The traffic of the wired client behind the WGB can be tunneled only to the Cisco WLC on the VLAN configured for the dynamic interface of the WLAN.
- D. The traffic of the wired client tagged on a specific VLAN behind the WGB can be tunneled to the same VLAN behind the Cisco WLC.
- E. The WGB mode allows to connect only one wired client behind the WGB to the WLAN.
- F. The WGB cannot serve wireless clients.
Answer : AB
Explanation:
Question 5
On a Cisco autonomous AP, the maximum number of attempts to send a packet (packet retries) is set to 32 by default. Which statement about the result when the
AP has tried to send a packet for that number of attempts and no response is received from the client is true?
- A. The access point drops the packet.
- B. The access point resets the radio interface.
- C. The access point disassociates the client.
- D. The client MAC address is excluded for 60 seconds.
Answer : A
Explanation:
The maximum data retries setting determines the number of attempts the wireless device makes to send a packet before giving up and dropping the packet.
The default setting is 32.
Reference:
http://www.cisco.com/c/en/us/td/docs/wireless/access_point/15_2_4_JB/configuration/guide/scg15-2-4-Book/scg15-2-4-chap6-radio.html#pgfId-1039239
Question 6
You are the network administrator of a Cisco Autonomous AP deployment. You want to stop a client with MAC address 5057.a89e.b1f7 and IP address 10.0.0.2 from associating to your APs.
Which configuration do you use?
- A. access-list 700 deny 5057.a89e.b1f7 0000.0000.0000!dot11 association mac-list 700
- B. access-list 700 permit 5057.a89e.b1f7 0000.0000.0000!dot11 association mac-list 700
- C. ip access-list 25 deny host 10.0.0.2!interface Dot11Radio0ip access-group 25 in!interface Dot11Radio1ip access-group 25 in
- D. ip access-list 25 deny host 10.0.0.2!interface Dot11Radio0ip access-group 25 out!interface Dot11Radio1ip access-group 25 out
Answer : AC
Explanation:
Filters Using MAC-Based ACLs -
You can use MAC address-based filters in order to filter client devices based on the hard coded MAC address. When a client is denied access through a MAC- based filter, the client cannot associate with the AP. MAC address filters allow or disallow the forwarding of unicast and multicast packets either sent from or addressed to specific MAC addresses.
This is the command syntax to create a MAC address-based ACL on the AP:
Note: This command has been wrapped to two lines because of spatial considerations. access-listaccess-list-number{permit | deny}
48-bit-hardware-address 48-bit-hardware-address-mask
In Cisco IOS Software Release 12.3(7)JA, MAC address ACLs can use numbers in the range of 700 to 799 as the ACL number. They can also use numbers in the expanded range of 1100 to 1199.
This example illustrates how to configure a MAC-based filter through the CLI, in order to filter the client with a MAC address of0040.96a5.b5d4:
-> Log in to the AP through the CLI.
Use the console port or Telnet in order to access the ACL through the Ethernet interface or the wireless interface.
-> Enter global configuration mode on the AP CLI:
-> AP#configure terminal
-> Create a MAC address ACL 700.
This ACL does not allow the client 0040.96a5.b5d4 to associate with the AP. access-list 700 deny 0040.96a5.b5d4 0000.0000.0000
!--- This ACL denies all traffic to and from !--- the client with MAC address 0040.96a5.b5d4.
-> Issue this command in order to apply this MAC-based ACL to the radio interface: dot11 association mac-list 700
Filters Using Standard Access ListsYou can use standard ACLs to allow or disallow the entry of client devices into the WLAN network based on the IP address of the client. Standard ACLs compare the source address of the IP packets to the addresses that are configured in the ACL in order to control traffic. This type of
ACL can be referred to as a source IP address-based ACL.
The command syntax format of a standard ACL isaccess-listaccess-list-number{permit | deny} {hostip-address|source-ip source-wildcard| any}.
In Cisco IOS® Software Release 12.3(7)JA, the ACL number can be any number from 1 to 99. Standard ACLs can also use the extended range of 1300 to 1999.
These additional numbers are expanded IP ACLs.
When a standard ACL is configured to deny access to a client, the client still associates to the AP. However, there is no data communication between the AP and the client.
This example shows a standard ACL that is configured to filter the client IP address 10.0.0.2 from the wireless interface (radio0 interface). The IP address of the
AP is 10.0.0.1.
After this is done, the client with IP address 10.0.0.2 cannot send or receive data through the WLAN network even though the client is associated to the AP.
Complete these steps in order to create a standard ACL through the CLI:
Log in to the AP through the CLI.
Use the console port or use Telnet in order to access the ACL through the Ethernet interface or th
Question 7
Which feature intersection of a Cisco 5760 Wireless LAN Controller with HA AP SSO is not true?
- A. Upon guest anchor controller switchover, mobility tunnels stay active, APs remain connected, clients rejoin at MA or MC, and clients are anchored on the new active controller.
- B. wIPS information is synced to the standby unit. The standby unit does not have to relearn wIPS information upon switchover.
- C. Roamed clients that have their data path going through the mobility tunnel endpoint "become Local" in case of Layer 2 with sticky anchoring and Layer 3 roam. Layer 2 roamed clients are not affected except when roaming occurs between Cisco Unified Wireless Network and CA controllers.
- D. Switchover during AP preimage download causes the Aps to start image download all over again from the new active controller.
Answer : B
Explanation:
-> Switchover during AP Pre-Image download causes the APs to start image download all over again from the new Active controller.
-> Rogue APs and clients are not synced to Standby and are re-learnt upon switchover.
-> Infrastructure MFP key is not synced to the Standby controller and is re-learnt upon switchover.
-> New Active controller re-learns the shun list from IPS and other MCs, and redistributes it to the MAs.
-> wIPS information is not synced to the Standby unit and is re-learnt upon switchover.
-> Clean Air detected Interferer devices are re-learnt after switchover.
-> Net Flow records are cleared upon switchover and collection starts fresh on the new Active controller.
-> Mobility paths and tunnels to the MO and other peer MCs are not disrupted upon switchover. However the Client state is cleaned up on the MO under which the HA pair exists and is re-learnt from the new Active controller when the client re-associates.
-> Roamed clients that have their data path going through the Mobility Tunnel Endpoint (MTE) "become Local" in case of L2 with Sticky Anchoring and L3 Roam.
L2 Roamed Clients are not affected except when roaming occurs between CUWN and CA controllers.
-> RRM related configurations and the AP neighbor list in the Leader HA pair is synced to the Standby controller.
-> Upon Guest Anchor controller switchover, mobility tunnels stay active, APs remain connected, clients rejoin at MA or MC, and are anchored on the new Active controller.
Reference:
http://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/5700/software/release/ios_xe_33/5760_HA_DG_iosXE33.html#pgfId-45754
Question 8
DRAG DROP -
Drag and drop the Cisco AVVID IP DSCP values on the left to its matching traffic type on the right. Not all options are used.
Select and Place:
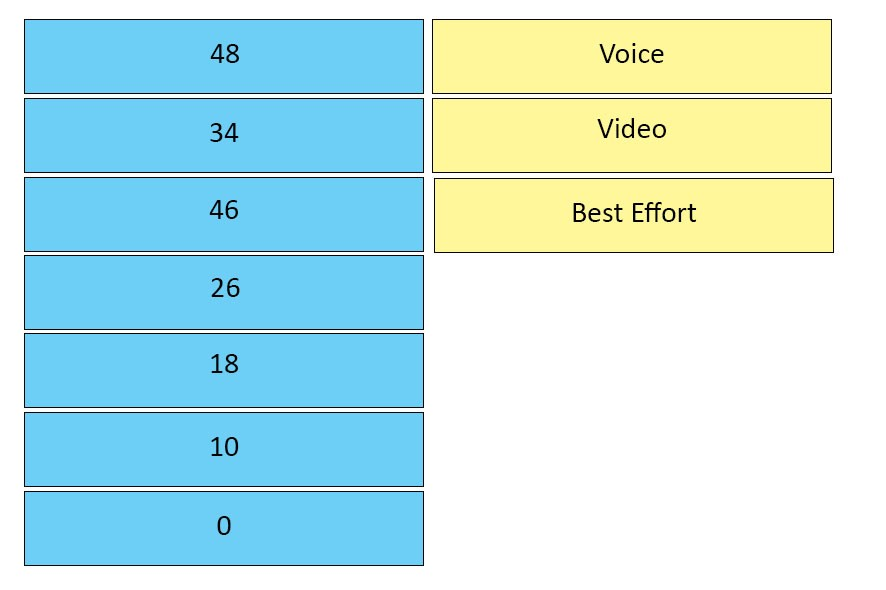
Answer : 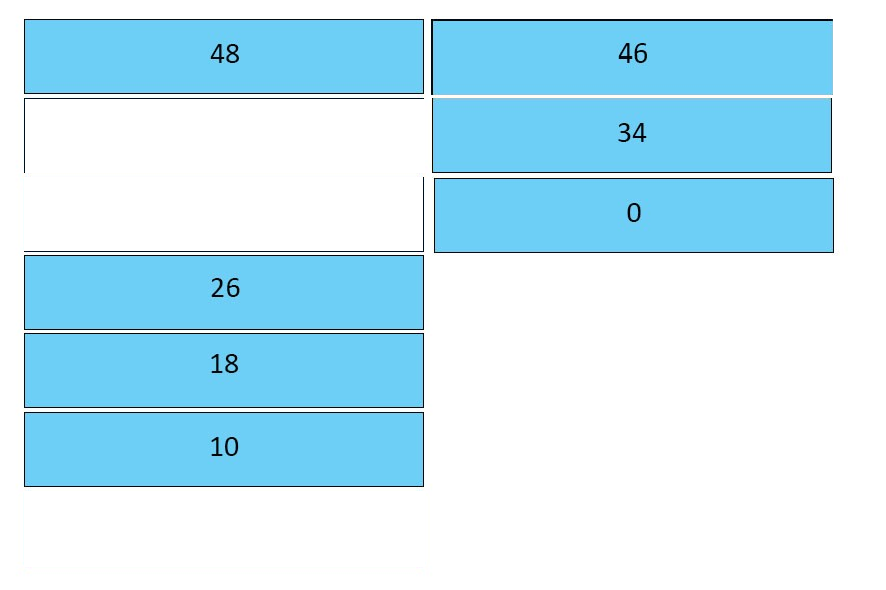
Question 9
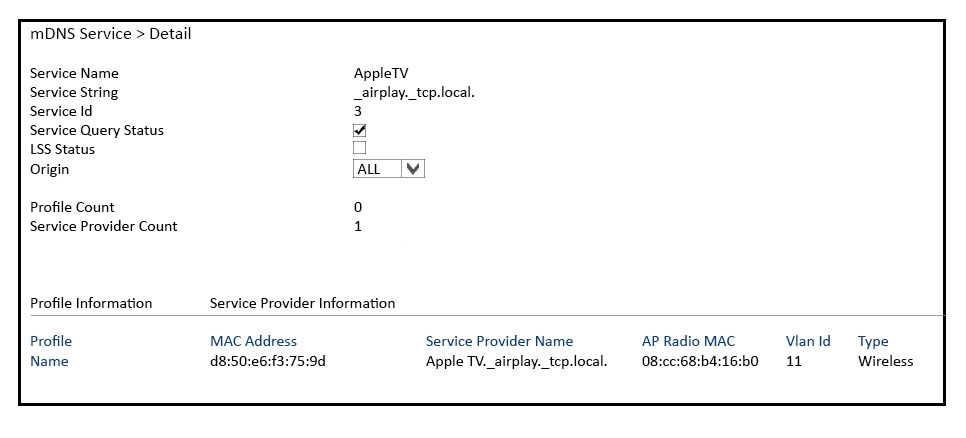
Refer to the exhibit. An Apple TV is associated to the wireless network. Wireless users attempt to connect to it, but they report that they cannot discover the Apple
TV on their devices. What is most likely the root cause?
- A. The mDNS Origin is not set to wireless.
- B. The "Service Provider Name" must not include "airplay" on it.
- C. The mDNS Service Provider is not associated to a profile.
- D. The "Service ID" must be changed to 1 in order to ensure the highest priority for the traffic.
Answer : A
Reference:
http://www.cisco.com/c/en/us/td/docs/wireless/technology/bonjour/7-5/Bonjour_Gateway_Phase-2_WLC_software_release_7-5.html#54133
Question 10
DRAG DROP -
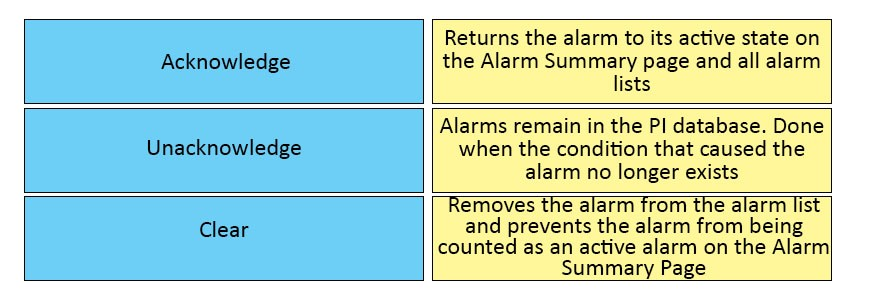
Prime infrastructure allows you to change an alarm status. Drag and drop the status on the left to the correct description on the right.
Select and Place:
Answer : 
Question 11
Which three statements about the high availability configuration on the Cisco 5760 WLCs are true? (Choose three.)
- A. Cisco WLC with more reboots is elected as active when the default stack priority is in use.
- B. Active Cisco WLCs in a pair can be identified using LED state without issuing any command on the Cisco WLC console.
- C. Cisco 5760 WLC uses a dedicated high availability port for high availability and configuration synchronization.
- D. All configuration including certificates are automatically synced between active and standby Cisco WLC.
- E. Cisco WLC with the highest priority in a stack are elected as the active Cisco WLC during the election process.
- F. EitherChannel bundles all ports on both active and standby Cisco WLC on a logical port.
Answer : BEF
Reference:
http://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/5700/software/release/ios_xe_33/5760_HA_DG_iosXE33.html#pgfId-43309
Question 12
You are a network administrator at ACME corporation where you have a pair of Cisco 5760 Wireless LAN Controllers deployed for HA AP SSO mode. A failover event occurs and the secondary Cisco 5760 controller moves into the active role. Which three statements about the failover event are true? (Choose three.)
- A. Rogue Aps and clients are not synced to the standby and are relearned upon switchover.
- B. NetFlow records are already exported upon switchover and collection starts resuming in the new active controller.
- C. Switchover during AP preimage download causes the Aps start image download all over again from the new active controller.
- D. With SSO, wIPS information is already synced with the standby unit and this information need not be relearned upon switchover.
- E. The new active controller does not need to relearn the shun list from IPS and other MCs, which eliminates the need to redistribute it to the MAs.
- F. Upon guest anchor controller switchover, mobility tunnels stay active, Aps remain connected, clients rejoin at MA or MC, and clients are anchored on the new active controller.
Answer : ACD
Explanation:
Question 13
Two wireless IP phones are never able to call each other when connected to the same autonomous AP. However, they can place calls to other wireless IP phones that are connected to other APs or to wired IP phones. The wireless phones are operating on VLAN100. Based on this output, which statement about the problem is true? ap(config-subif)#do show run interface do 0.100
Building configuration"¦
Current configuration: 320 bytes
!
interface Dot11Radio1.100
encapsulation dot1Q 100
no ip route-cache
bridge-group 100
bridge-group 100 subscriber-loop-control
bridge-group 100 port-protected
bridge-group 100 block-unknown-source
no bridge-group 100 source-learning
no bridge-group 100 unicast-flooding
bridge-group 100 spanning-disabled
end
- A. P2P blocking is enabled via the no bridge-group 100 unicast-flooding command.
- B. P2P blocking is enabled via the bridge-group 100 block-unknown-source command.
- C. P2P blocking is enabled via the bridge-group 100 subscriber-loop-control command.
- D. P2P blocking is enabled via the no bridge-group 100 source-learning command.
- E. P2P blocking is enabled via the bridge-group 100 port-protected command.
Answer : E
Explanation:
Public Secure Packet Forwarding (PSPF) prevents client devices associated to an access point from inadvertently sharing files or communicating with other client devices associated to the access point. It provides Internet access to client devices without providing other capabilities of a LAN. This feature is useful for public wireless networks like those installed in airports or on college campuses.

Note To prevent communication between clients associated to different access points, you must set up protected ports on the switch to which the wireless devices are connected. See the "Configuring Protected Ports" section for instructions on setting up protected ports.
To enable and disable PSPF using CLI commands on the wireless device, you use bridge groups. You can find a detailed explanation of bridge groups and instructions for implementing them in this document: "¢ Cisco IOS Bridging and IBM Networking Configuration Guide, Release 12.2. Click this link to browse to the Configuring Transparent Bridging chapter: http:// www.cisco.com/univercd/cc/td/doc/product/software/ios122/122cgcr/fibm_c/bcfpart1/bcftb.htm
You can also enable and disable PSPF using the web-browser interface. The PSPF setting is on the Radio Settings pages.
PSPF is disabled by default. Beginning in privileged EXEC mode, follow these steps to enable PSPF:
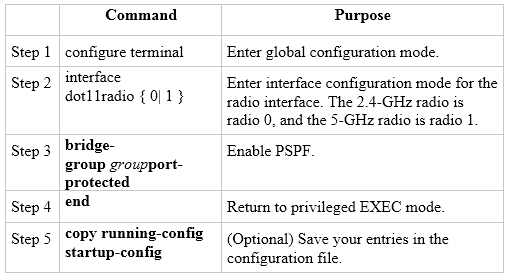
Question 14
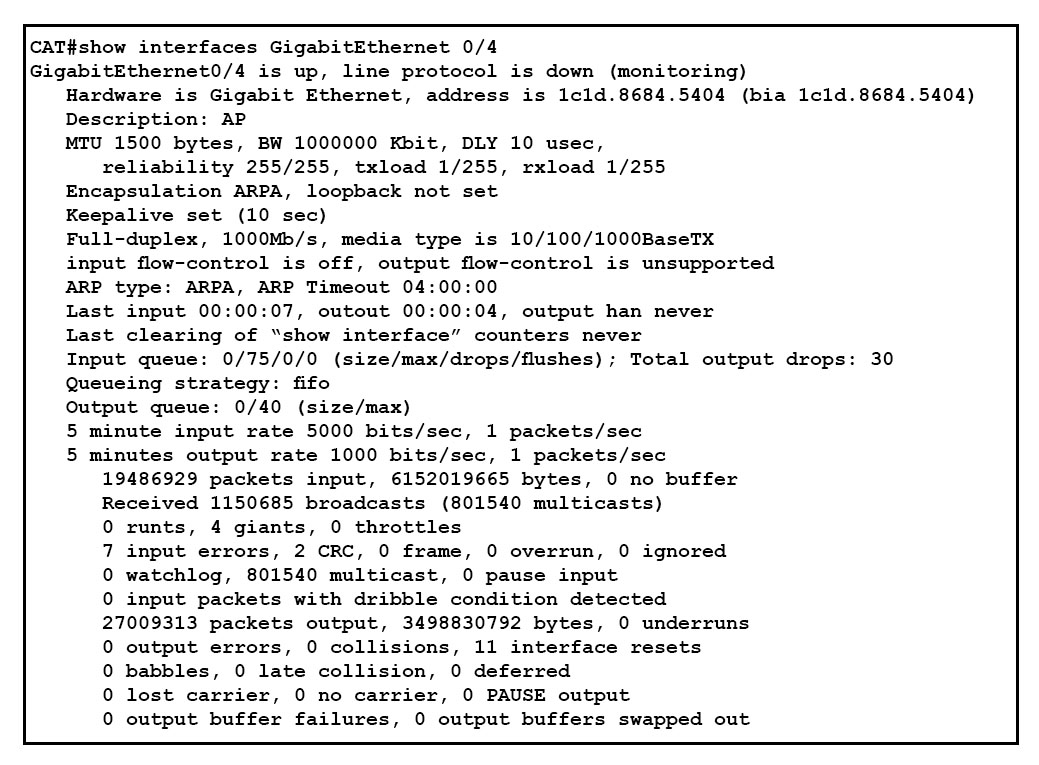
Refer to the exhibit. You cannot establish IP communication over interface GigabitEthernet 0/4 with an access point connected to it. Which reason is the cause of the issue?
- A. Interface GigabitEthernet 0/4 is mirroring traffic and cannot be used at this time.
- B. Line protocol is down on the interface because "output flow-control is unsupported".
- C. The problem is due to physical connectivity. The Ethernet cable must be revised.
- D. A SPAN session is configured on the Switch destination interface GigabitEthernet 0/4.
Answer : D
Explanation:
The port is a part of a monitor session (a SPAN session) as a destination port. Look for "monitor session" commands in your configuration that refer to the port, and if you do not need this monitoring session, you may remove it from your configuration. That will make the port work normally again.
Reference:
https://supportforums.cisco.com/discussion/11667971/gigabitethernet201-down-line-protocol-down-monitoring
Question 15
You are setting up a Cisco access point in repeater mode with a non-Cisco point as the parent and you use this interface configuration on your Cisco access point. interface Dot11Radio0 no ip address no ip route-cache no ip route-cache
!
ssid my WIFInetwork
!
station-role repeater
bridge-group 1 subscriber-loop-control
bridge-group 1 block-unknown-source
no bridge-group 1 source-learning
no bridge-group 1 unicast-flooding
bridge-group 1 spanning-disabled
You are getting the following error message. Which reason for this issue is true?
%DOT11-4-CANT_ASSOC: Interface Dot11Radio0, cannot associate. NO aironet Extension IE
- A. The parent AP MAC address has not been defined.
- B. Repeater made only works between Cisco access points.
- C. When repeater mode is used, unicast-flooding must be enabled to allow Aironet IE communications.
- D. "dot11 extension aironet" is missing under the interface Dot11Radio0 interface.
Answer : B
Explanation:
Repeaters and bridges have to be the same manufacturer because there are some protocols that other manufacturers won't accept. So Cisco Aironet to Cisco
Aironet will work. Cisco Aironet to Cisco Linksys (and other manufacturers) will NOT workReference:
Reference:
https://supportforums.cisco.com/discussion/11308521/cisco-ap-1141-repeater-hp-procurve-problems