CCIE Security Written Exam v1.0
Question 1
Which three statements about SXP are true? (Choose three.)
- A. To enable an access device to use IP device tracking to learn source device IP addresses, DHCP snooping must be configured.
- B. Each VRF supports only one CTS-SXP connection.
- C. It resides in the control plane, where connections can be initiated from a listener.
- D. Separate VRFs require different CTS-SXP peers, but they can use the same source IP addresses.
- E. The SGA ZBPF uses the SGT to apply forwarding decisions.
- F. Packets can be tagged with SGTs only with hardware support.
Answer : BCF
Explanation:
Question 2
View the Exhibit.
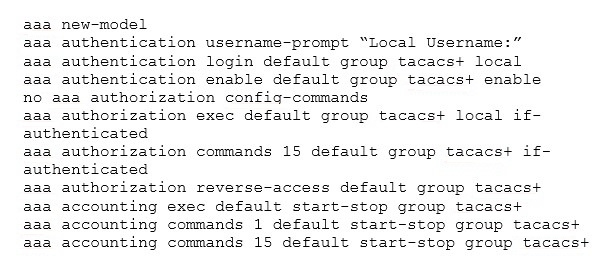
Refer to the exhibit. Which two effects of this configuration are true? (Choose two.)
- A. Configuration commands in the router are authorized without checking the TACACS+ server.
- B. When a user logs in to privilege EXEC mode, the router will track all user activity.
- C. Requests to establish a reverse AUX connection to the router will be authorized against the TACACS+ server.
- D. When a user attempts to authenticate on the device, the TACACS+ server will be prompt the user to enter the username stored in the router"™s database.
- E. If a user attempts to log in as a level 15 user, the local database will be used for authentication and TACACS+ server will be used for authorization.
- F. It configures the router"™s local database as the backup authentication method for all TTY, console, and aux logins.
Answer : AD
Explanation:
Question 3
Which two options are benefits of the Cisco ASA Identity Firewall? (Choose two.)
- A. It can identify threats quickly based on their URLs.
- B. It can operate completely independently of other services.
- C. It supports an AD server module to verify identity data.
- D. It decouples security from the network topology.
- E. It can apply security policies on an individual user or user-group basis.
Answer : DE
Explanation:
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa93/configuration/general/asa-general-cli/aaa-idfw.html
Question 4
View the Exhibit.
Switch-A (config)# cgmp leave-processing
Refer to the exhibit. Which two effects of this configuration are true? (Choose two.)
- A. It allows the switch to detect IGMPv2leave group messages.
- B. It optimizes the use of network bandwidth on the LAN segment.
- C. IGMPv2 leave group messages are stored in the switch CAM table for faster processing.
- D. Hosts send leave group messages to the Solicited-Node Address multicast address FF02::1:FF00:0000/104.
- E. It improves the processing time of CGMP leave messages.
- F. Hosts send leave group messages to the all-router multicast address when they want to stop receiving data for that group.
Answer : BE
Explanation:
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4000/8-2glx/configuration/guide/multi.html
Question 5
Which two statements about the TTL value in an IPv4 header are true? (Choose two.)
- A. It is a 4-bit value.
- B. Its maximum value is 128.
- C. It is a 16-bit value.
- D. It can be used for traceroute operations.
- E. When it reaches 0, the router sends an ICMP Type 11 message to the originator.
Answer : DE
Explanation:
Question 6
View the Exhibit.

Refer to the exhibit. Which effect of this configuration is true?
- A. Any VPN user with a session timeout of 24 hours can access the device.
- B. Users attempting to access the console port are authenticated against the TACACS+ server.
- C. If TACACS+authentication fails, the ASA uses cisco123 as its default password.
- D. The device tries to reach the server every 24 hours and falls back to the LOCAL database if it fails.
- E. The servers in the TACACS+ group are reactivated every 1440 seconds.
Answer : B
Explanation:
Question 7
Which of the following is AMP Endpoints office engine for windows?
- A. ClamAV
- B. ClamAMP
- C. TETRA
- D. TETRAAMP
Answer : C
Explanation:
Question 8
Which two characteristics of DTLS are true? (Choose two.)
- A. It includes a retransmission method because it uses an unreliable datagram transport.
- B. It cannot be used if NAT exists along the path.
- C. It completes key negotiation and bulk data transfer over a single channel.
- D. It includes a congestion control mechanism.
- E. It supports long data transfers and connectionless data transfers.
- F. It is used mostly by applications that use application layer object-security protocols.
Answer : AD
Explanation:
Question 9
A new computer is not getting its IPv6 address assigned by the router. While running WireShark to try to troubleshoot the problem, you find a lot of data that is not helpful to nail down the problem.
What two filters would you apply to WireShark to filter the data that you are looking for? (Choose two.)
- A. icmpv6.type = =136
- B. icmpv6.type = =135
- C. icmpv5type = =135
- D. icmpv6type = =136
- E. icmpv6type = =135
Answer : AB
Explanation:
Question 10
Which two options are benefits of network summarization? (Choose two.)
- A. It can summarize discontiguous IP addresses.
- B. It can easily be added to existing networks.
- C. It prevents unnecessary routing updates at the summarization boundary if one of the routes in the summary is unstable.
- D. It reduces the number of routes.
- E. It can increase the convergence of the network.
Answer : CD
Explanation:
Question 11
Which statement about VRF-aware GDOI group members is true?
- A. IPsec is used only to secure data traffic.
- B. Registration traffic and rekey traffic must operate on different VRFs.
- C. Multiple VRFs are used to separate control traffic and data traffic.
- D. The GM cannot route control traffic through the same VRF as data traffic.
Answer : A
Explanation:
Question 12
Which file extensions are supported on the Firesight Management Center 6.1 file policies that can be analyzed dynamically using the Threat Grid Sandbox integration?
- A. MSEXE, MSOLE2, NEW-OFFICE, PDF
- B. DOCX, WAV, XLS, TXT
- C. DOC, MSOLE2, XML, PDF
- D. TXT, MSOLE2, WAV, PDF
Answer : A
Explanation:
Question 13
View the Exhibit.
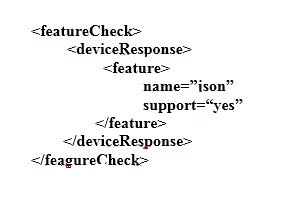
Refer to the exhibit. Which data format is used in this script?
- A. API
- B. JSON
- C. JavaScript
- D. YANG
- E. XML
Answer : E
Explanation:
Question 14
In which type of multicast does the Cisco ASA forward IGMP messages to the upstream router?
- A. multicast group concept
- B. PIM multicast routing
- C. stub multicastrouting
- D. clustering
Answer : C
Explanation:
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa90/configuration/guide/asa_90_cli_config/route_multicast.html#pgfId-1099362
Question 15
Which option is a data modeling language used to model configuration and state data of network elements?
- A. NETCONF
- B. RESTCONF
- C. YANG
- D. SNMPv4
Answer : C
Explanation:
Reference:
https://www.ietf.org/proceedings/92/slides/slides-92-netmod-10.pdf