CCDE™ Written Exam (v2.1) v13.0
Question 1
What are two benefits of protecting the control plane of a network device? (Choose two.)
- A. prevents the delivery of packets from spoof sources
- B. preserves the confidentiality of traffic encrypted by IPsec
- C. maintains routing protocol adjacencies with local neighbors
- D. maintains remote management access to the router
Answer : CD
Question 2
Which tunneling mechanism provides confidentiality as well as tunneling capabilities?
- A. MPLS L3VPN
- B. IPsec ESP
- C. L2TPv3
- D. IPsec AH
Answer : B
Question 3
Your network operations team is deploying Access Control Lists (ACLs) across your
Internet gateways. They wish to place an ACL inbound on the Internet gateway interface facing the core network (the "trusted" interface). Which one of these addresses would the
ACL need for traffic sourced from the inside interface, to match the source address of the traffic?
- A. inside local
- B. outside local
- C. inside global
- D. outside global
Answer : A
Question 4
Refer to the exhibit.
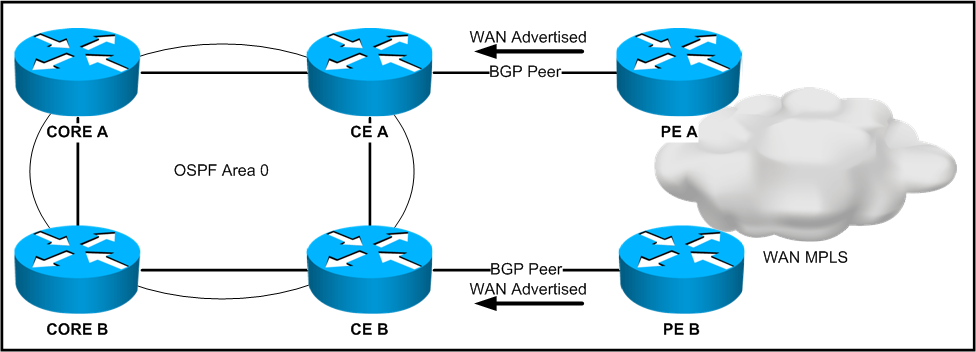
The design is being proposed for use within the network. The CE devices are OSPF graceful restart-capable, and the core devices are OSPF graceful restart-aware. The WAN advertisements received from BGP are redistributed into OSPF. A forwarding supervisor failure event takes place on CE A.
During this event, how will the routes learned from the WAN be seen on the core devices?
- A. via CE A and CE B
- B. via CE A
- C. via CE B
- D. no WAN routes will be accessible
Answer : C
Question 5
What statement is true about designing a policy in which more than one class share a queue?
- A. It must be avoided under all circumstances.
- B. It will result in a negative class.
- C. It requires consideration of the performance targets of classes sharing the queue.
- D. It should be deployed throughout the network to simplify the design.
Answer : C
Question 6
Your company plans to implement an Internet gateway router that is performing NAT. This same gateway will be terminating various IPsec tunnels to other remote sites. Which address type is appropriate for the ACL that will govern the sources of traffic entering the tunnel in the inside interface?
- A. inside local
- B. inside global
- C. outside local
- D. outside global
Answer : B
Question 7
A company is planning to connect its 30 sites with a VPLS WAN backbone. A router at each site should establish neighborships with all other routers using the OSPF routing protocol. Which three points must be considered regarding DR and BDR when different router platforms are used? (Choose three.)
- A. It is a best practice that the routers with the most powerful hardware should take the role of the DR and BDR.
- B. If the IP OSPF priority is the same for all routers, the highest loopback IP address and router ID will decide which routers will take the DR and BDR role during the selection process.
- C. To select the DR and BDR, the IP OSPF priority must be set to a higher value than the default value at the DR and BDR during the selection process.
- D. To select the DR and BDR, the IP OSPF priority must be set to a lower value than the default value at the DR and BDR during the selection process.
- E. The role for the DR and BDR will be selected when a new OSPF router comes up.
- F. To force two routers to become a DR and a BDR, the IP OSPF priority can be set to zero at all other OSPF routers.
Answer : ABF
Question 8
Network designers plan to interconnect two geographically separated data centers using an
Ethernet-over-MPLS pseudowire. Within that design, the link between the sites is stable, there are no apparent loops in the topology, and the root bridges for the respective VLANs are stable and unchanging. What additional aspect of the design should be adjusted to mitigate the chance of connectivity issues to the peer data center when the connection takes place?
- A. Enable 802.1d on one data center, and 802.1w on the other.
- B. Ensure that the spanning tree diameter for one or more VLANs is not too large.
- C. Enable UDLD on the link between the data centers.
- D. Enable root guard on the link between the data centers.
Answer : B
Question 9
You are designing a wireless LAN with the following components:
High-density indoor access point deployment
2.4-GHz and 5-GHz radios
802.11a, 802.11g, and 802.11n mode wireless LAN clients
Site survey results show negligible foreign WiFi and non-WiFi interference. What is the best method to decrease duty cycle (radio frequency utilization) and increase overall wireless
LAN client performance for this design?
- A. Disable all data rates below 12 Mb/s on all access points.
- B. Decrease radio transmit power on all access points that report a high duty cycle.
- C. Increase radio transmit power on all access points that report a high duty cycle.
- D. Disable all data rates above 12 Mb/s on all access points.
- E. Increase radio transmit power on all access points.
Answer : A
Question 10
Which IPv4 addressing and routing scheme can increase the availability of a network service during a DoS attack?
- A. unicast
- B. broadcast
- C. anycast
- D. multicast
Answer : C
Question 11
You are designing a network that will run EIGRP over a Metro Ethernet service that does not employ a link-loss technology. What will be the impact on convergence if there is a break in the end-to-end Layer 2 connectivity within the service provider network?
- A. The routers will immediately lose their adjacencies and converge.
- B. The routing protocol will not converge until the hold timers have expired.
- C. The switch ports connected to the router will go down and the routers will immediately converge.
- D. The VLAN on the switches will go inactive, the ports associated on the switch will go down, and the routers will immediately converge.
Answer : B
Question 12
You are designing a network to support data, voice and video. Which two main factors will you address to improve network convergence? (Choose two.)
- A. event propagation delay
- B. failure detection delay
- C. forwarding engine update delay
- D. routing table recalculation delay
Answer : BD
Question 13
A network designer has provisioned a router to use IPsec to encrypt the traffic over a GRE tunnel going to a web server at a remote location. From the router, the network designer can ping the web server, although the users in the office comment that they are unable to reach it. (Note: The DF bit is not set.) Which aspect should be changed in the design of the virtual connection?
- A. IP addresses of the GRE tunnel endpoints
- B. IPsec configuration
- C. MTU size on the GRE tunnel
- D. encapsulation of the GRE tunnel
Answer : C
Question 14
Which two resources are propagated by the headend router for constrained based path computation with MPLS Traffic Engineering? (Choose two.)
- A. average link utilization
- B. average input queue depth
- C. link bandwidth
- D. link affinity
- E. link delay
- F. link jitter
Answer : CD
Question 15
A new video multicast application is deployed in the network. The application team wants to use the 239.0.0.1 multicast group to stream the video to users. They want to know if this choice will impact the existing multicast design. What impact will their choice have on the existing multicast design?
- A. Because 239.0.0.1 is a private multicast range, a flood of PIM packets that have to be processed by the CPU and hostswill be sent by the routers in the network.
- B. Because 239.0.0.1 is a private multicast range, the rendezvous point has to send out constant group updates that will have to be processed by the CPU and hosts.
- C. The multicast application sends too many packets into the network and the network infrastructure drops packets.
- D. The 239.0.0.1 group address maps to a system MAC address, and all multicast traffic will have to be sent to the CPU and flooded out all ports.
Answer : D