Performing CyberOps Using Core Security Technologies (CBRCOR) v1.0
Question 1
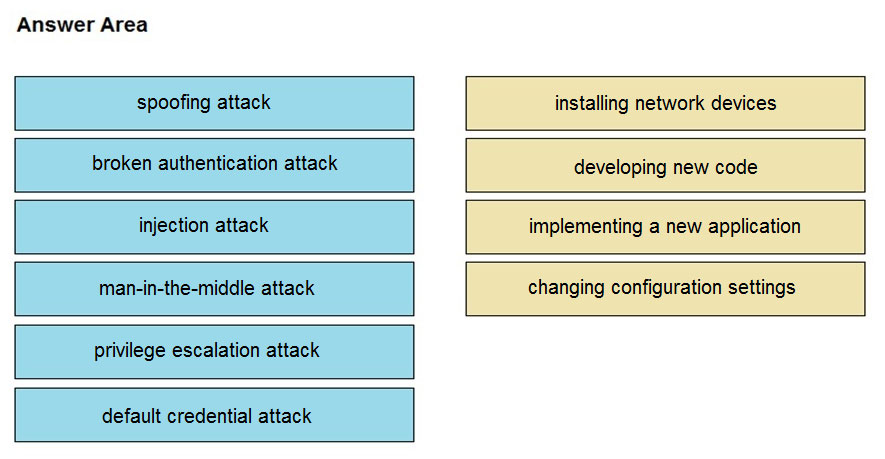
DRAG DROP -
Drag and drop the threat from the left onto the scenario that introduces the threat on the right. Not all options are used.
Select and Place:
Answer : 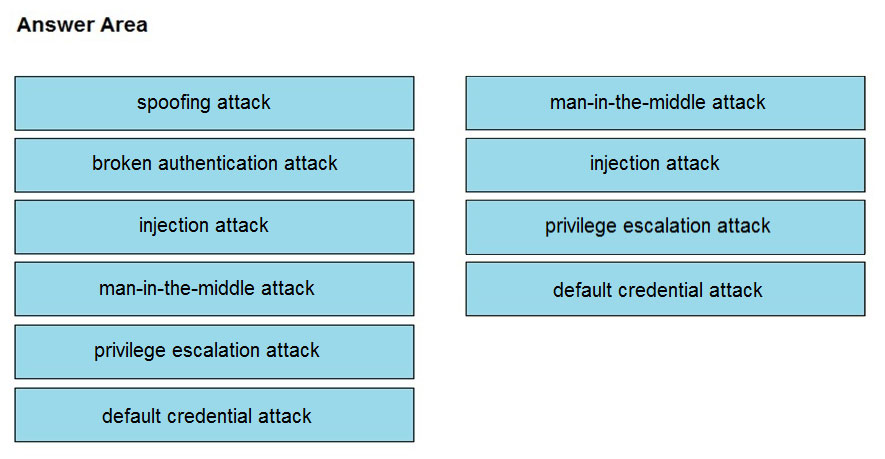
Question 2
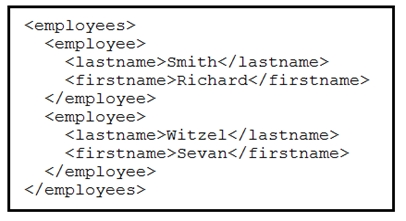
Refer to the exhibit. Which data format is being used?
- A. JSON
- B. HTML
- C. XML
- D. CSV
Answer : B
Question 3
The incident response team was notified of detected malware. The team identified the infected hosts, removed the malware, restored the functionality and data of infected systems, and planned a company meeting to improve the incident handling capability. Which step was missed according to the NIST incident handling guide?
- A. Contain the malware
- B. Install IPS software
- C. Determine the escalation path
- D. Perform vulnerability assessment
Answer : D
Question 4
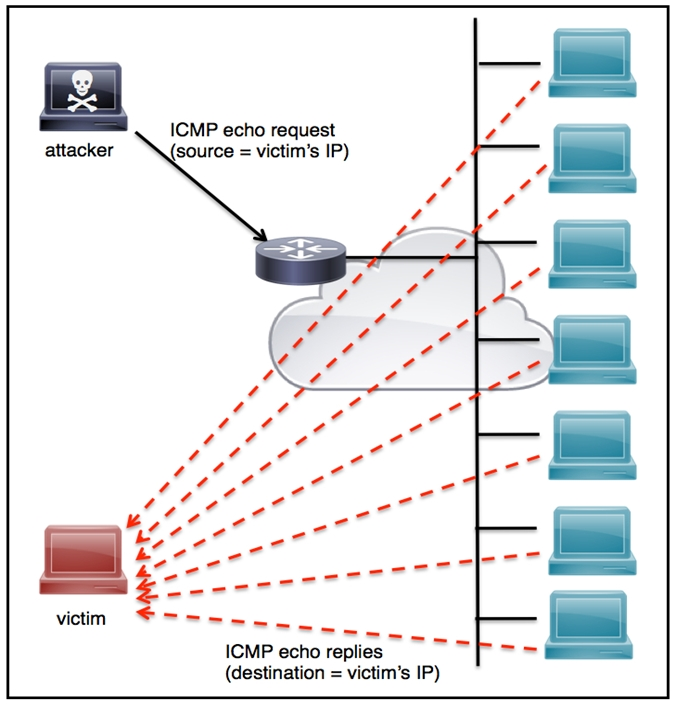
Refer to the exhibit. An engineer must tune the Cisco IOS device to mitigate an attack that is broadcasting a large number of ICMP packets. The attack is sending the victimג€™s spoofed source IP to a network using an IP broadcast address that causes devices in the network to respond back to the source IP address. Which action does the engineer recommend?
- A. Use command ip verify reverse-path interface
- B. Use global configuration command service tcp-keepalives-out
- C. Use subinterface command no ip directed-broadcast
- D. Use logging trap 6
Answer : A
Reference:
https://www.ccexpert.us/pix-firewall/ip-verify-reversepath-command.html
Question 5
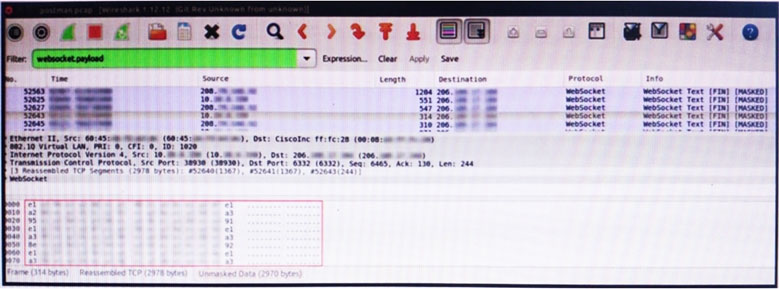
Refer to the exhibit. An engineer is analyzing this Vlan0392-int12-239.pcap file in Wireshark after detecting a suspicious network activity. The origin header for the direct IP connections in the packets was initiated by a google chrome extension on a WebSocket protocol. The engineer checked message payloads to determine what information was being sent off-site but the payloads are obfuscated and unreadable. What does this STIX indicate?
- A. The extension is not performing as intended because of restrictions since ports 80 and 443 should be accessible
- B. The traffic is legitimate as the google chrome extension is reaching out to check for updates and fetches this information
- C. There is a possible data leak because payloads should be encoded as UTF-8 text
- D. There is a malware that is communicating via encrypted channels to the command and control server
Answer : C
Question 6
What do 2xx HTTP response codes indicate for REST APIs?
- A. additional action must be taken by the client to complete the request
- B. the server takes responsibility for error status codes
- C. communication of transfer protocol-level information
- D. successful acceptance of the clientג€™s request
Answer : D
Reference:
https://restfulapi.net/http-status-codes/#:~:text=HTTP%20defines%20these%20standard%20status,results%20of%20a%20client%27s%
20request.&text=2xx%3A%20Success%20ג€"%20Indicates%20that%20the,order%20to%20complete%20their%20request
.
Question 7
An engineer received an alert of a zero-day vulnerability affecting desktop phones through which an attacker sends a crafted packet to a device, resets the credentials, makes the device unavailable, and allows a default administrator account login. Which step should an engineer take after receiving this alert?
- A. Initiate a triage meeting to acknowledge the vulnerability and its potential impact
- B. Determine company usage of the affected products
- C. Search for a patch to install from the vendor
- D. Implement restrictions within the VoIP VLANS
Answer : C
Question 8
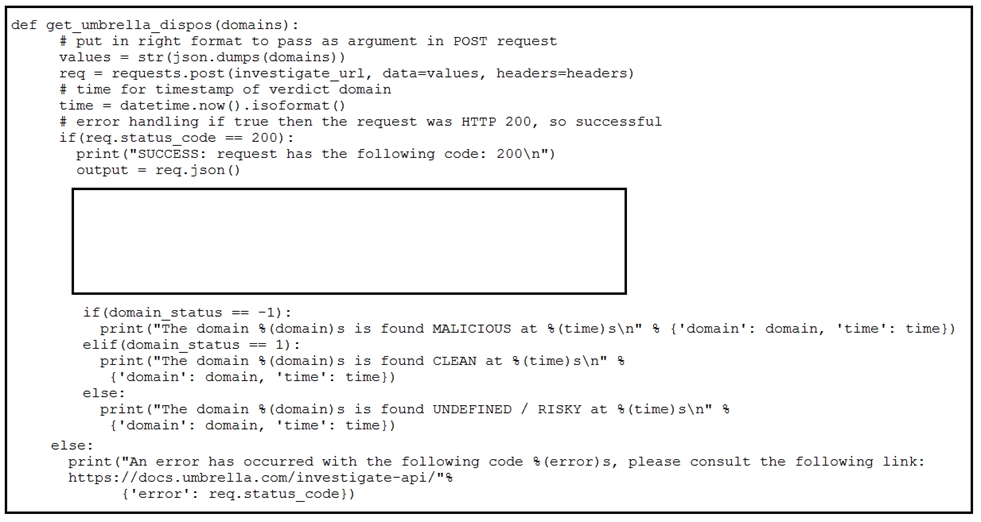
Refer to the exhibit. Which code snippet will parse the response to identify the status of the domain as malicious, clean or undefined?
A.
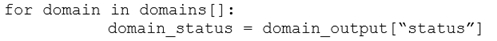
B.

C.

D.

Answer : C
Question 9
An engineer receives an incident ticket with hundreds of intrusion alerts that require investigation. An analysis of the incident log shows that the alerts are from trusted IP addresses and internal devices. The final incident report stated that these alerts were false positives and that no intrusions were detected. What action should be taken to harden the network?
- A. Move the IPS to after the firewall facing the internal network
- B. Move the IPS to before the firewall facing the outside network
- C. Configure the proxy service on the IPS
- D. Configure reverse port forwarding on the IPS
Answer : C
Question 10
A SOC team is informed that a UK-based user will be traveling between three countries over the next 60 days. Having the names of the 3 destination countries and the user's working hours, what must the analyst do next to detect an abnormal behavior?
- A. Create a rule triggered by 3 failed VPN connection attempts in an 8-hour period
- B. Create a rule triggered by 1 successful VPN connection from any nondestination country
- C. Create a rule triggered by multiple successful VPN connections from the destination countries
- D. Analyze the logs from all countries related to this user during the traveling period
Answer : D
Question 11
An engineer receives a report that indicates a possible incident of a malicious insider sending company information to outside parties. What is the first action the engineer must take to determine whether an incident has occurred?
- A. Analyze environmental threats and causes
- B. Inform the product security incident response team to investigate further
- C. Analyze the precursors and indicators
- D. Inform the computer security incident response team to investigate further
Answer : C
Question 12
An employee abused PowerShell commands and script interpreters, which lead to an indicator of compromise (IOC) trigger. The IOC event shows that a known malicious file has been executed, and there is an increased likelihood of a breach. Which indicator generated this IOC event?
- A. ExecutedMalware.ioc
- B. Crossrider.ioc
- C. ConnectToSuspiciousDomain.ioc
- D. W32.AccesschkUtility.ioc
Answer : D
Question 13
Refer to the exhibit. Which command was executed in PowerShell to generate this log?
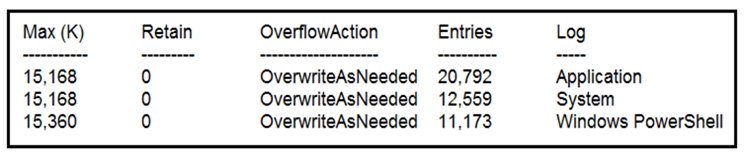
- A. Get-EventLog -LogName*
- B. Get-EventLog -List
- C. Get-WinEvent -ListLog* -ComputerName localhost
- D. Get-WinEvent -ListLog*
Answer : A
Reference:
https://lists.xymon.com/archive/2019-March/046125.html
Question 14
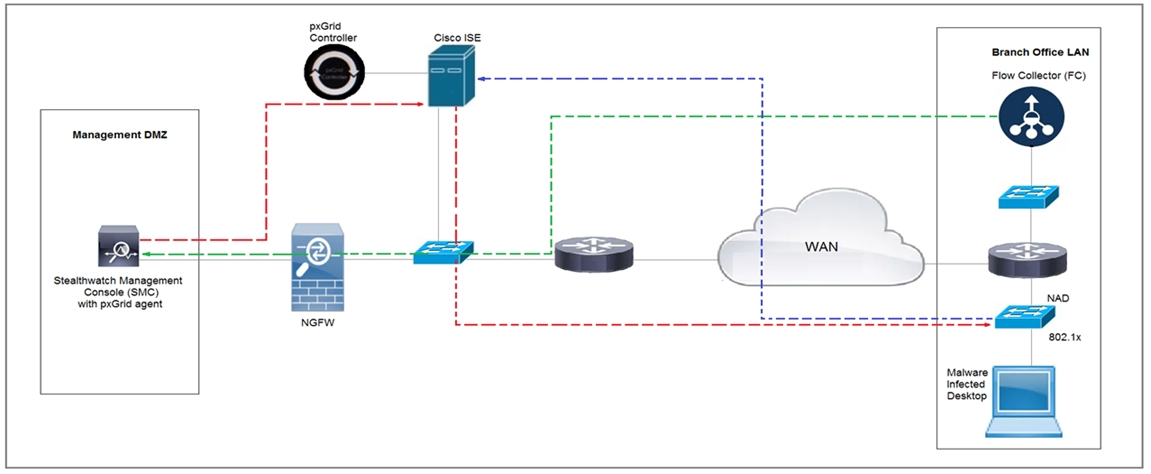
Refer to the exhibit. Cisco Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a Quarantine VLAN using Adaptive Network Control policy. Which telemetry feeds were correlated with
SMC to identify the malware?
- A. NetFlow and event data
- B. event data and syslog data
- C. SNMP and syslog data
- D. NetFlow and SNMP
Answer : B
Question 15
A security architect is working in a processing center and must implement a DLP solution to detect and prevent any type of copy and paste attempts of sensitive data within unapproved applications and removable devices. Which technical architecture must be used?
- A. DLP for data in motion
- B. DLP for removable data
- C. DLP for data in use
- D. DLP for data at rest
Answer : C
Reference:
https://www.endpointprotector.com/blog/what-is-data-loss-prevention-dlp/