Administration of Symantec Data Loss Prevention 15 v1.0
Question 1
What is the correct order for data in motion when a customer has integrated their CloudSOC and DLP solutions?
- A. User > CloudSOC Gatelet > DLP Cloud Detection Service > Application
- B. User > Enforce > Application
- C. User > Enforce > CloudSOC > Application
- D. User > CloudSOC Gatelet > Enforce > Application
Answer : C
Question 2
Refer to the exhibit.
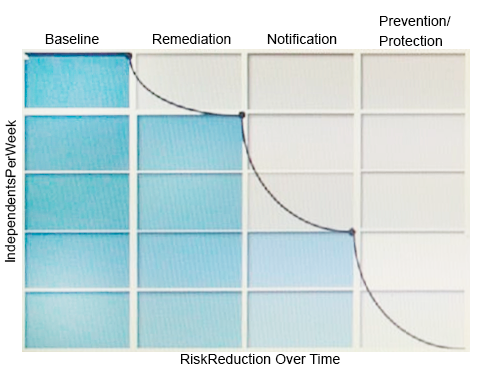
What activity should occur during the baseline phase, according to the risk reduction model?
- A. Define and build the incident response team
- B. Monitor incidents and tune the policy to reduce false positives
- C. Establish business metrics and begin sending reports to business unit stakeholders
- D. Test policies to ensure that blocking actions minimize business process disruptions
Answer : C
Question 3
Which two DLP products support the new Optical Character Recognition (OCR) engine in Symantec DLP 15.0? (Choose two.)
- A. Endpoint Prevent
- B. Cloud Service for Email
- C. Network Prevent for Email
- D. Network Discover
- E. Cloud Detection Service
Answer : BC
Question 4
Which two actions are available for a ג€Network Prevent: Remove HTTP/HTTPS contentג€ response rule when the content is unable to be removed? (Choose two.)
- A. Allow the content to be posted
- B. Remove the content through FlexResponse
- C. Block the content before posting
- D. Encrypt the content before posting
- E. Redirect the content to an alternative destination
Answer : AC
Reference:
https://help.symantec.com/cs/dlp15.0/DLP/v27603831_v120691346/Configuring-the-Network-Prevent-for-Web:-Remove-HTTP-S-Content-action?locale=EN_US
Question 5
Which two factors are common sources of data leakage where the main actor is well-meaning insider? (Choose two.)
- A. An absence of a trained incident response team
- B. A disgruntled employee for a job with a competitor
- C. Merger and Acquisition activities
- D. Lack of training and awareness
- E. Broken business processes
Answer : BD
Question 6
What is required on the Enforce server to communicate with the Symantec DLP database?
- A. Port 8082 should be opened
- B. CryptoMasterKey.properties file
- C. Symbolic links to .dbf files
- D. SQL*Plus Client
Answer : D
Reference:
https://www.symantec.com/connect/articles/three-tier-installation-dlp-product
Question 7
Which option is an accurate use case for Information Centric Encryption (ICE)?
- A. The ICE utility encrypts files matching DLP policy being copied from network share through use of encryption keys.
- B. The ICE utility encrypts files matching DLP policy being copied to removable storage through use of encryption keys.
- C. The ICE utility encrypts files matching DLP policy being copied to removable storage on an endpoint use of certificates.
- D. The ICE utility encrypts files matching DLP policy being copied from network share through use of certificates
Answer : B
Reference:
https://help.symantec.com/cs/ICE1.0/ICE/v126756321_v120576779/Using-ICE-with-Symantec-Data-Loss-Preventionabout_dlp?locale=EN_US
Question 8
A DLP administrator is attempting to add a new Network Discover detection server from the Enforce management console. However, the only available options are Network Monitor and Endpoint servers.
What should the administrator do to make the Network Discover option available?
- A. Restart the Symantec DLP Controller service
- B. Apply a new software license file from the Enforce console
- C. Install a new Network Discover detection server
- D. Restart the Vontu Monitor Service
Answer : C
Question 9
A DLP administrator is testing Network Prevent for Web functionality. When the administrator posts a small test file to a cloud storage website, no new incidents are reported.
What should the administrator do to allow incidents to be generated against this file?
- A. Change the ג€Ignore requests Smaller Thanג€ value to 1
- B. Add the filename to the Inspect Content Type field
- C. Change the ג€PacketCapture.DISCARD_HTTP_GETג€ value to ג€falseג€
- D. Uncheck trial mode under the ICAP tab
Answer : A
Reference:
https://help.symantec.com/cs/dlp15.0/DLP/id-SF0B0161467_v120691346/Configuring-Network-Prevent-for-Web-Server?locale=EN_US
Question 10
A compliance officer needs to understand how the company is complying with its data security policies over time.
Which report should be compliance officer generate to obtain the compliance information?
- A. Policy report, filtered on date and summarized by policy
- B. Policy Trend report, summarized by policy, then quarter
- C. Policy report, filtered on quarter and summarized by policy
- D. Policy Trend report, summarized by policy, then severity
Answer : A
Question 11
A DLP administrator has performed a test deployment of the DLP 15.0 Endpoint agent and now wants to uninstall the agent. However, the administrator no longer remembers the uninstall password.
What should the administrator do to work around the password problem?
- A. Apply a new global agent uninstall password in the Enforce management console.
- B. Manually delete all the Endpoint agent files from the test computer and install a new agent package.
- C. Replace the PGPsdk.dll file on the agentג€™s assigned Endpoint server with a copy from a different Endpoint server
- D. Use the UninstallPwdGenerator to create an UninstallPasswordKey.
Answer : A
Reference:
https://help.symantec.com/cs/dlp15.0/DLP/v122359104_v120691346/About-agent-password-management?locale=EN_US
Question 12
A DLP administrator determines that the \SymantecDLP\Protect\Incidents folder on the Enforce server contains. BAD files dated today, while other. IDC files are flowing in and out of the \Incidents directory. Only .IDC files larger than 1MB are turning to .BAD files.
What could be causing only incident data smaller than 1MB to persist while incidents larger than 1MB change to .BAD files?
- A. A corrupted policy was deployed.
- B. The Enforce serverג€™s hard drive is out of space.
- C. A detection server has excessive filereader restarts.
- D. Tablespace is almost full.
Answer : D
Question 13
Which statement accurately describes where Optical Character Recognition (OCR) components must be installed?
- A. The OCR engine must be installed on detection server other than the Enforce server.
- B. The OCR server software must be installed on one or more dedicated (non-detection) Linux servers.
- C. The OCR engine must be directly on the Enforce server.
- D. The OCR server software must be installed on one or more dedicated (non-detection) Windows servers.
Answer : D
Reference:
https://help.symantec.com/cs/dlp15.0/DLP/v122760159_v120691346/About-content-detection-with-OCR-Sensitive-Image-Recognition?locale=EN_US
Question 14
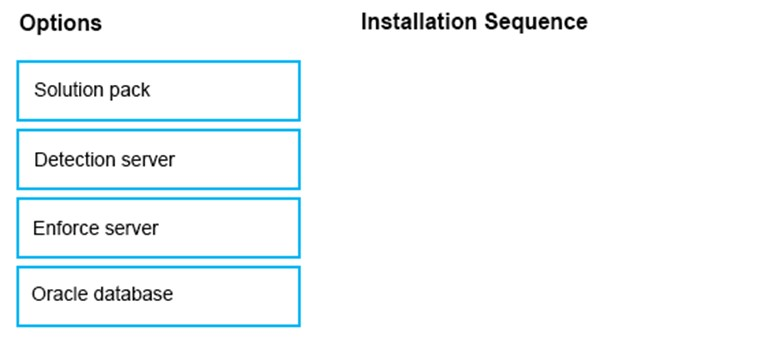
DRAG DROP -
What is the correct installation sequence for the components shown here, according to the Symantec Installation Guide?
Place the options in the correct installation sequence.
Select and Place:
Answer : 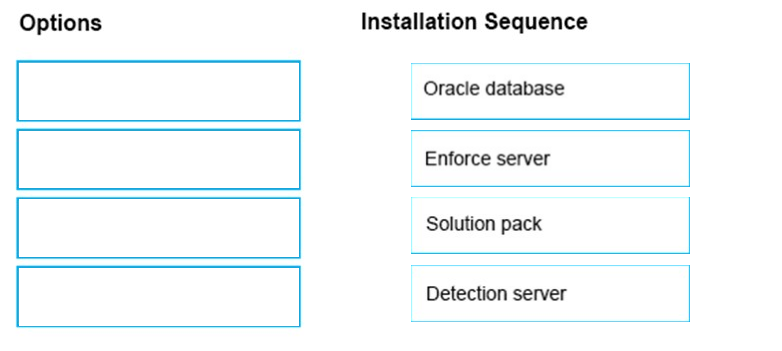
Question 15
Which action is available for use in both Smart Response and Automated Response rules?
- A. Log to a Syslog Server
- B. Limit incident data retention
- C. Modify SMTP message
- D. Block email message
Answer : A