CCNA Security Implementing Cisco Network Security v1.0
Question 1
Refer to the exhibit.
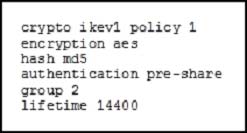
What is the effect of the given command sequence?
- A. It configures IKE Phase 1.
- B. It configures a site-to-site VPN tunnel.
- C. It configures a crypto policy with a key size of 14400.
- D. It configures IPSec Phase 2.
Answer : A
Explanation:
ikev2 policy command from global configuration mode. The prompt displays IKE policy configuration mode. For example: hostname(config)# crypto ikev1 policy 1 hostname(config-ikev1-policy)#
After creating the policy, you can specify the settings for the policy.
Reference:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa84/configuration/guide/asa_84_cli_config/vpn_ike.html
Question 2
Refer to the exhibit.
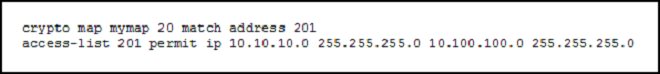
What is the effect of the given command sequence?
- A. It defines IPSec policy for traffic sourced from 10.10.10.0/24 with a destination of 10.100.100.0/24.
- B. It defines IPSec policy for traffic sourced from 10.100.100.0/24 with a destination of 10.10.10.0/24.
- C. It defines IKE policy for traffic sourced from 10.10.10.0/24 with a destination of 10.100.100.0/24.
- D. It defines IKE policy for traffic sourced from 10.100.100.0/24 with a destination of 10.10.10.0/24.
Answer : A
Explanation:
Crypto map entry "mymap 30" references the dynamic crypto map set "mydynamicmap," which can be used to process inbound security association negotiation requests that do not match "mymap" entries 10 or 20. In this case, if the peer specifies a transform set that matches one of the transform sets specified in
"mydynamicmap," for a flow "permitted" by the access list 103, IPSec will accept the request and set up security associations with the remote peer without previously knowing about the remote peer. If accepted, the resulting security associations (and temporary crypto map entry) are established according to the settings specified by the remote peer.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/command/reference/srfipsec.html
Question 3
Refer to the exhibit.
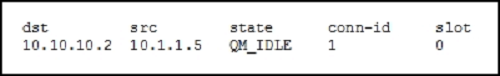
While troubleshooting site-to-site VPN, you issued the show crypto isakmp sa command. What does the given output show?
- A. IPSec Phase 1 is established between 10.10.10.2 and 10.1.1.5.
- B. IPSec Phase 2 is established between 10.10.10.2 and 10.1.1.5.
- C. IPSec Phase 1 is down due to a QM_IDLE state.
- D. IPSec Phase 2 is down due to a QM_IDLE state.
Answer : A
Phase 1 of IPsec is used to establish a secure channel between the two peers that will be used for further data transmission. The ASAs will exchange secret keys, they authenticate each other and will negotiate about the IKE security policies. This is what happens in phase 1:
-> Authenticate and protect the identities of the IPsec peers.
-> Negotiate a matching IKE policy between IPsec peers to protect the IKE exchange.
-> Perform an authenticated Diffie-Hellman exchange to have matching shared secret keys.
-> Setup a secure tunnel for IKE phase 2.
Reference:
https://networklessons.com/security/cisco-asa-site-site-ikev1-ipsec-vpn/
Question 4
Refer to the exhibit.
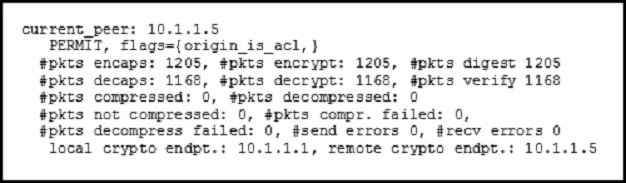
While troubleshooting site-to-site VPN, you issued the show crypto ipsec sa command. What does the given output show?
- A. IPSec Phase 2 is established between 10.1.1.1 and 10.1.1.5.
- B. ISAKMP security associations are established between 10.1.1.5 and 10.1.1.1.
- C. IKE version 2 security associations are established between 10.1.1.1 and 10.1.1.5.
- D. IPSec Phase 2 is down due to a mismatch between encrypted and decrypted packets.
Answer : A
Explanation:
Once the secure tunnel from phase 1 has been established, we will start phase 2. In this phase the two firewalls will negotiate about the IPsec security parameters that will be used to protect the traffic within the tunnel. In short, this is what happens in phase 2:
-> Negotiate IPsec security parameters through the secure tunnel from phase 1.
-> Establish IPsec security associations.
-> Periodically renegotiates IPsec security associations for security.
Reference:
https://networklessons.com/security/cisco-asa-site-site-ikev1-ipsec-vpn/
Question 5
Refer to the exhibit.
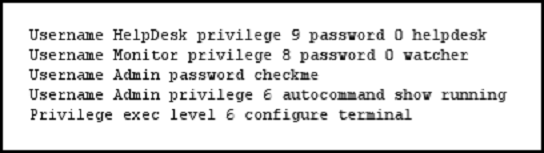
The Admin user is unable to enter configuration mode on a device with the given configuration. What change can you make to the configuration to correct the problem?
- A. Remove the autocommand keyword and arguments from the Username Admin privilege line.
- B. Change the Privilege exec level value to 15.
- C. Remove the two Username Admin lines.
- D. Remove the Privilege exec line.
Answer : A
Explanation:
The autocommand causes the specified command to be issued automatically after the user logs in. When the command is complete, the session is terminated.
Because the command can be any length and contain embedded spaces, commands using the autocommand keyword must be the last option on the line.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/command/reference/fsecur_r/srfpass.html#wp1030793
Question 6
After reloading a router, you issue the dir command to verify the installation and observe that the image file appears to be missing. For what reason could the image file fail to appear in the dir output?
- A. The secure boot-image command is configured.
- B. The secure boot-comfit command is configured.
- C. The confreg 0x24 command is configured.
- D. The reload command was issued from ROMMON.
Answer : A
Explanation:
Secured files will not appear on the output of a dir command issued from an executive shell because the IFS prevents secure files in a directory from being listed.
ROM monitor (ROMMON) mode does not have any such restriction and can be used to list and boot secured files.
Reference:
http://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_usr_cfg/configuration/15-mt/sec-usr-cfg-15-mt-book/sec-resil-config.html
Question 7
What is the effect of the send-lifetime local 23:59:00 31 December 31 2013 infinite command?
- A. It configures the device to begin transmitting the authentication key to other devices at 00:00:00 local time on January 1, 2014 and continue using the key indefinitely.
- B. It configures the device to begin transmitting the authentication key to other devices at 23:59:00 local time on December 31, 2013 and continue using the key indefinitely.
- C. It configures the device to begin accepting the authentication key from other devices immediately and stop accepting the key at 23:59:00 local time on December 31, 2013.
- D. It configures the device to generate a new authentication key and transmit it to other devices at 23:59:00 local time on December 31, 2013.
- E. It configures the device to begin accepting the authentication key from other devices at 23:59:00 local time on December 31, 2013 and continue accepting the key indefinitely.
- F. It configures the device to begin accepting the authentication key from other devices at 00:00:00 local time on January 1, 2014 and continue accepting the key indefinitely.
Answer : B
Explanation:
Send-lifetime infinite command configures the device to begin transmitting the authentication key to other devices at 23:59:00 local time on December 31, 2013 and continue using the key indefinitely
Question 8
What type of packet creates and performs network operations on a network device?
- A. control plane packets
- B. data plane packets
- C. management plane packets
- D. services plane packets
Answer : A
Explanation:
Under normal network operating conditions, the vast majority of packets handled by network devices are data plane packets. These packets are handled in the fast path. Network devices are optimized to handle these fast path packets efficiently. Typically, considerably fewer control and management plane packets are required to create and operate IP networks. Thus, the punt path and route processor are significantly less capable of handling the kinds of packets rates experienced in the fast path since they are never directly involved in the forwarding of data plane packets
Reference:
http://www.cisco.com/c/en/us/about/security-center/copp-best-practices.html
Question 9
An attacker installs a rogue switch that sends superior BPDUs on your network. What is a possible result of this activity?
- A. The switch could offer fake DHCP addresses.
- B. The switch could become the root bridge.
- C. The switch could be allowed to join the VTP domain.
- D. The switch could become a transparent bridge.
Answer : B
Explanation:
The BPDU guard feature is designed to allow network designers to keep the active network topology predictable. BPDU guard is used to protect the switched network from the problems that may be caused by the receipt of BPDUs on ports that should not be receiving them. The receipt of unexpected BPDUs may be accidental or may be part of an unauthorized attempt to add a switch to the network. BPDU guard is best deployed toward user-facing ports to prevent rogue switch network extensions by an attacker.
Question 10
In what type of attack does an attacker virtually change a device's burned-in address in an attempt to circumvent access lists and mask the device's true identity?
- A. gratuitous ARP
- B. ARP poisoning
- C. IP spoofing
- D. MAC spoofing
Answer : D
Explanation:
If your original MAC address is revealed, a hacker can use it to impersonate you! On many networks (wired or wireless) access is restricted based on MAC address to avoid access to unauthorized devices on the network. So, when you go offline, someone can use your machine's MAC address and access the network as 'you'.
Reference:
http://blog.technitium.com/2011/06/why-you-need-to-change-mac-address.html
Question 11
What command can you use to verify the binding table status?
- A. show ip dhcp snooping database
- B. show ip dhcp snooping binding
- C. show ip dhcp snooping statistics
- D. show ip dhcp pool
- E. show ip dhcp source binding
- F. show ip dhcp snooping
Answer : A
Explanation:
To retain the bindings across reloads, you must use the DHCP snooping database agent. Without this agent, the bindings established by DHCP snooping are lost upon reload, and connectivity is lost as well.
The database agent stores the bindings in a file at a configured location. Upon reload, the switch reads the file to build the database for the bindings. The switch keeps the file current by writing to the file as the database changes.
Reference:
http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/snoodhcp.html#wp1090624
Question 12
If a switch receives a superior BPDU and goes directly into a blocked state, what mechanism must be in use?
- A. root guard
- B. EtherChannel guard
- C. loop guard
- D. BPDU guard
Answer : A
Explanation:
The root guard feature protects the network against such issues.
The configuration of root guard is on a per-port basis. Root guard does not allow the port to become an STP root port, so the port is always STP-designated. If a better BPDU arrives on this port, root guard does not take the BPDU into account and elect a new STP root. Instead, root guard puts the port into the root- inconsistent STP state. You must enable root guard on all ports where the root bridge should not appear. In a way, you can configure a perimeter around the part of the network where the STP root is able to be located.
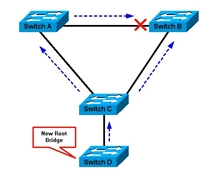
In the following figure, enable root guard on the Switch C port that connects to Switch D.
Switch C in figure below blocks the port that connects to Switch D, after the switch receives a superior BPDU. Root guard puts the port in the root-inconsistent
STP state. No traffic passes through the port in this state. After device D ceases to send superior BPDUs, the port is unblocked again. Via STP, the port goes from the listening state to the learning state, and eventually transitions to the forwarding state. Recovery is automatic; no human intervention is necessary.
This message appears after root guard blocks a port:
%SPANTREE-2-ROOTGUARDBLOCK: Port 1/1 tried to become non-designated in VLAN 77.
Moved to root-inconsistent state
Reference:
http://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10588-74.html
Question 13
Which statement about a PVLAN isolated port configured on a switch is true?
- A. The isolated port can communicate only with the promiscuous port.
- B. The isolated port can communicate with other isolated ports and the promiscuous port.
- C. The isolated port can communicate only with community ports.
- D. The isolated port can communicate only with other isolated ports.
Answer : A
A promiscuous port can communicate with all interfaces, including the isolated and community ports within a PVLAN.
Reference:
http://www.cisco.com/c/en/us/tech/lan-switching/private-vlans-pvlans-promiscuous-isolated-community/index.html
Question 14
If you change the native VLAN on the trunk port to an unused VLAN, what happens if an attacker attempts a double-tagging attack?
- A. The trunk port would go into an error-disabled state.
- B. A VLAN hopping attack would be successful.
- C. A VLAN hopping attack would be prevented.
- D. The attacked VLAN will be pruned.
Answer : C
Explanation:
The key feature of a double tagging attack is exploiting the native VLAN. Since VLAN 1 is the default VLAN for access ports and the default native VLAN on trunks, it"™s an easy target. The first countermeasure is to remove access ports from the default VLAN 1 since the attacker"™s port must match that of the switch"™s native VLAN.
Reference:
https://www.nlogic.co/understanding-vlan-hopping-attacks/
Question 15
What is a reason for an organization to deploy a personal firewall?
- A. To protect endpoints such as desktops from malicious activity.
- B. To protect one virtual network segment from another.
- C. To determine whether a host meets minimum security posture requirements.
- D. To create a separate, non-persistent virtual environment that can be destroyed after a session.
- E. To protect the network from DoS and syn-flood attacks.
Answer : A
Explanation:
The sole purpose of firewall is to protect endpoints (workstations, and other devices) from malicious activity and network connections with nefarious purposes.
Reference:
http://searchmidmarketsecurity.techtarget.com/definition/personal-firewall