CCNA Cyber Ops Implementing Cisco Cybersecurity Operations v1.0
Question 1
Which option can be addressed when using retrospective security techniques?
- A. if the affected host needs a software update
- B. how the malware entered our network
- C. why the malware is still in our network
- D. if the affected system needs replacement
Answer : B
Question 2
What is accomplished in the identification phase of incident handling?
- A. determining the responsible user
- B. identifying source and destination IP addresses
- C. defining the limits of your authority related to a security event
- D. determining that a security even has occurred
Answer : D
Explanation:
In the identification phase you need to work out whether you are dealing with an event or an incident. This is where understanding your environment is critical as it means looking for significant deviations from "normal" traffic baselines or other methods.
Question 3
Which network device creates and sends the initial packet of a session?
- A. source
- B. origination
- C. destination
- D. network
Answer : A
Question 4
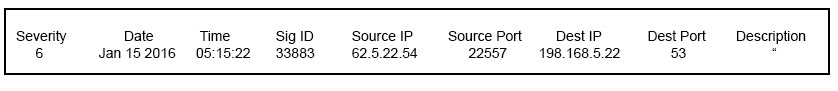
Refer to the exhibit. Which type of log is this an example of?
- A. syslog
- B. NetFlow log
- C. proxy log
- D. IDS log
Answer : A
Question 5
From a security perspective, why is it important to employ a clock synchronization protocol on a network?
- A. so that everyone knows the local time
- B. to ensure employees adhere to work schedule
- C. to construct an accurate timeline of events when responding to an incident
- D. to guarantee that updates are pushed out according to schedule
Answer : C
Question 6
Which CVSSv3 Attack Vector metric value requires the attacker to physically touch or manipulate the vulnerable component?
- A. local
- B. physical
- C. network
- D. adjacent
Answer : B
Reference:
https://www.first.org/cvss/specification-document
Question 7
DRAG DROP -
Drag and drop the elements of incident handling from the left into the correct order on the right.
Select and Place:
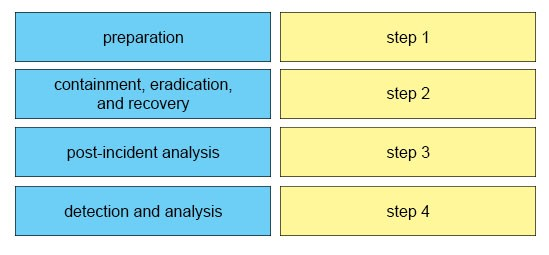
Answer : 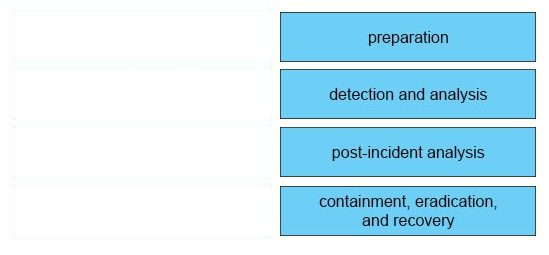
Reference:
https://countuponsecurity.com/2012/12/21/computer-security-incident-handling-6-steps/
Question 8
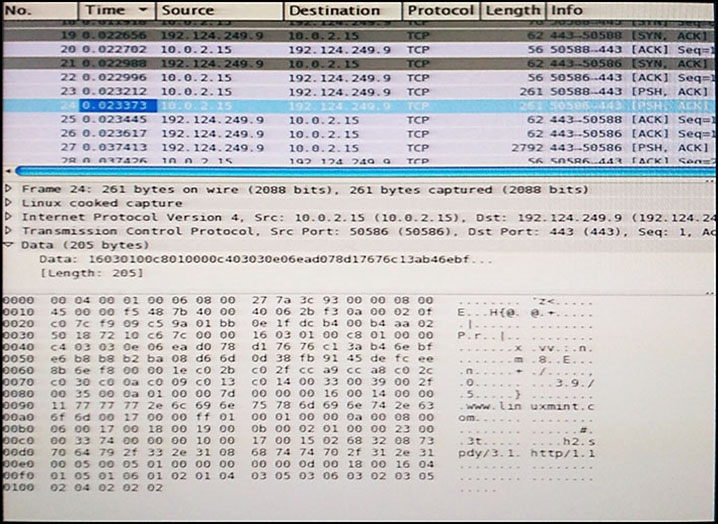
Refer to the exhibit. Which application protocol is in this PCAP file?
- A. TCP
- B. SSH
- C. HTTP
- D. SSL
Answer : D
Question 9
Which option creates a display filter on Wireshark on a host IP address or name?
- A. ip.address == <address> or ip.network == <network>
- B. [tcp|udp] ip.[src|dst] port <port>
- C. ip.addr == <addr> or ip.name == <name>
- D. ip.addr == <addr> or ip.host == <host>
Answer : D
Question 10
You see confidential data being exfiltrated to an IP address that is attributed to a known Advanced Persistent Threat group. Assume that this is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Diamond Model of Intrusion?
- A. reconnaissance
- B. weaponization
- C. delivery
- D. action on objectives
Answer : C
Question 11
Refer to the exhibit.
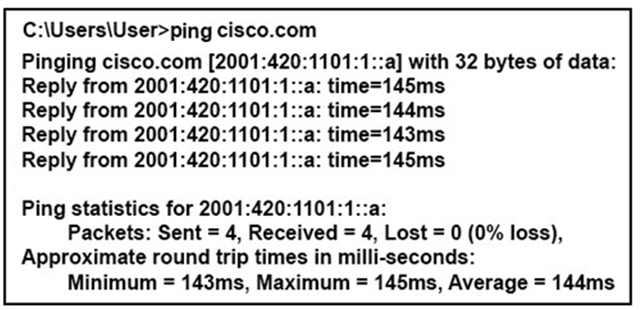
What can be determined from this ping result?
- A. The public IP address of cisco.com is 2001:420:1101:1::a.
- B. The Cisco.com website is down.
- C. The Cisco.com website is responding with an internal IP.
- D. The public IP address of cisco.com is an IPv4 address.
Answer : A
Question 12
DRAG DROP -
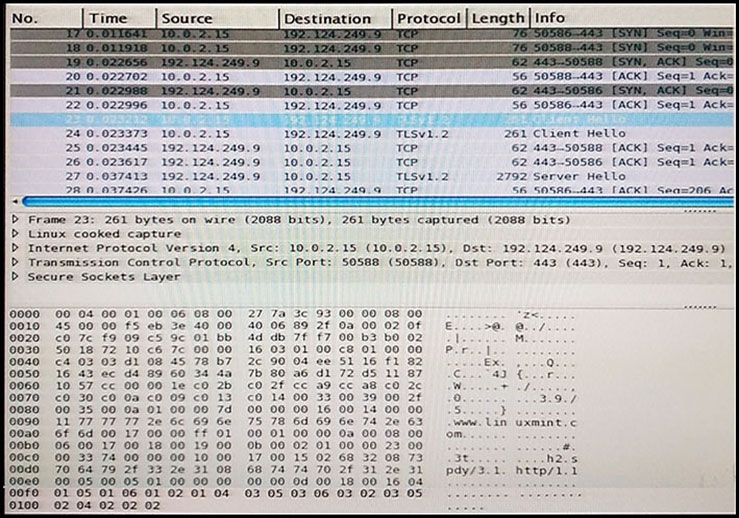
Refer to the exhibit. Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
Select and Place:
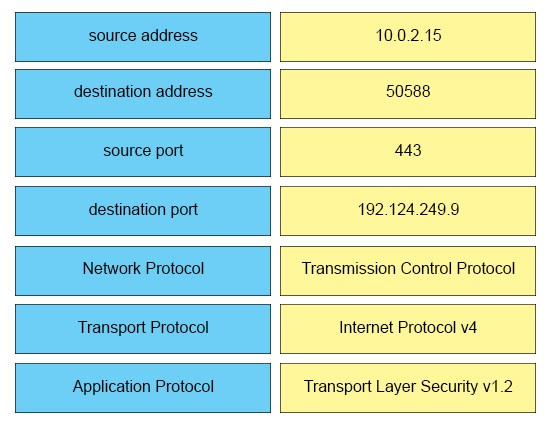
Answer : 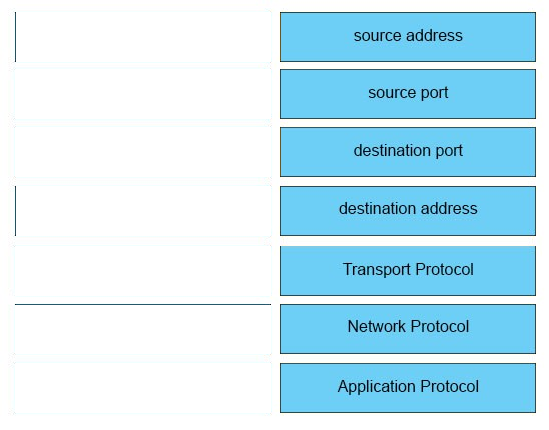
Question 13
Which option filters a LibPCAP capture that used a host as a gateway?
- A. [tcp|udp] [src|dst] port <port>
- B. [src|dst] net <net> [{mask <mask>}|{len <len>}]
- C. ether [src|dst] host <ehost>
- D. gateway host <host>
Answer : D
Reference:
https://www.wireshark.org/docs/wsug_html_chunked/ChCapCaptureFilterSection.html
Question 14
Which identifies both the source and destination location?
- A. IP address
- B. URL
- C. ports
- D. MAC address
Answer : A
Question 15
Which description of a retrospective malware detection is true?
- A. You use Wireshark to identify the malware source.
- B. You use historical information from one or more sources to identify the affected host or file.
- C. You use information from a network analyzer to identify the malware source.
- D. You use Wireshark to identify the affected host or file.
Answer : B