CCNA Cyber Ops Understanding Cisco Cybersecurity Fundamentals v1.0
Question 1
DRAG DROP -
Drag the data source on the left to the correct data type on the right.
Select and Place:
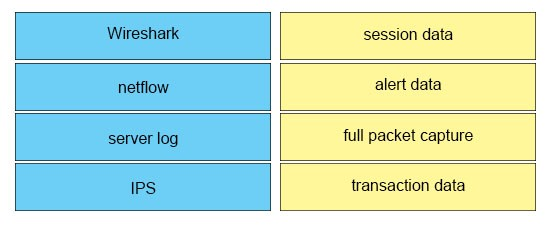
Answer : 
Question 2
Which protocol maps IP network addresses to MAC hardware addresses so that IP packets can be sent across networks?
- A. Internet Control Message Protocol
- B. Address Resolution Protocol
- C. Session Initiation Protocol
- D. Transmission Control Protocol/Internet Protocol
Answer : B
Question 3
Which option is an advantage to using network-based anti-virus versus host-based anti-virus?
- A. Network-based has the ability to protect unmanaged devices and unsupported operating systems.
- B. There are no advantages compared to host-based antivirus.
- C. Host-based antivirus does not have the ability to collect newly created signatures.
- D. Network-based can protect against infection from malicious files at rest.
Answer : A
Question 4
Which concern is important when monitoring NTP servers for abnormal levels of traffic?
- A. Being the cause of a distributed reflection denial of service attack.
- B. Users changing the time settings on their systems.
- C. A critical server may not have the correct time synchronized.
- D. Watching for rogue devices that have been added to the network.
Answer : A
Question 5
While viewing packet capture data, you notice that one IP is sending and receiving traffic for multiple devices by modifying the IP header. Which option is making this behavior possible?
- A. TOR
- B. NAT
- C. encapsulation
- D. tunneling
Answer : C
Question 6
Which hashing algorithm is the least secure?
- A. MD5
- B. RC4
- C. SHA-3
- D. SHA-2
Answer : A
Question 7
You must create a vulnerability management framework. Which main purpose of this framework is true?
- A. Conduct vulnerability scans on the network.
- B. Manage a list of reported vulnerabilities.
- C. Identify, remove, and mitigate system vulnerabilities.
- D. Detect and remove vulnerabilities in source code.
Answer : C
Question 8
Which definition of Windows Registry is true?
- A. set of pages that are currently resident in physical memory
- B. basic unit to which the operating system allocates processor time
- C. set of virtual memory addresses
- D. database that stores low-level settings for the operating system
Answer : D
Question 9
Which two features must a next generation firewall include? (Choose two.)
- A. data mining
- B. host-based antivirus
- C. application visibility and control
- D. Security Information and Event Management
- E. intrusion detection system
Answer : CE
Question 10
Which type of exploit normally requires the culprit to have prior access to the target system?
- A. local exploit
- B. denial of service
- C. system vulnerability
- D. remote exploit
Answer : A
Question 11
DRAG DROP -
Drag the technology on the left to the data type the technology provides on the right.
Select and Place:
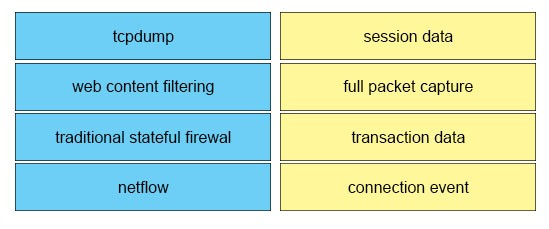
Answer : 
Question 12
Which two options are recognized forms of phishing? (Choose two.)
- A. spear
- B. whaling
- C. mailbomb
- D. hooking
- E. mailnet
Answer : AB
Question 13
According to RFC 1035, which transport protocol is recommended for use with DNS queries?
- A. Transmission Control Protocol
- B. Reliable Data Protocol
- C. Hypertext Transfer Protocol
- D. User Datagram Protocol
Answer : D
Question 14
Which statement about digitally signing a document is true?
- A. The document is hashed and then thedocument is encrypted with the private key.
- B. The document is hashed and then the hash is encrypted with the private key.
- C. The document is encrypted and then the document is hashed with the public key.
- D. The document is hashed and then the document isencrypted with the public key.
Answer : B
Question 15
Which term represents a weakness in a system that could lead to the system being compromised?
- A. vulnerability
- B. threat
- C. exploit
- D. risk
Answer : A