Riverbed Certified Solutions Associate - Network Performance Management v8.0
Question 1
Protocols that are typically monitored in TCP/IP networks by visibility tools include (Select
3):
- A. SAN HBA Protocol
- B. TCP Protocols such as HTTP and HTTPS
- C. UDP Protocols such as SMTP and Video streaming
- D. IPv4 Protocols including TCP, UDP, and ICMP
- E. IPv4 Protocols such as x.25, TTY and TTL
Answer : B,C,D
Question 2
Which of the following are valid Dashboard Content Block Types? (Select 3)
- A. Service Health
- B. Watched Traffic
- C. WAN Utilization
- D. Service Map
- E. Security Threats
Answer : ABD
Question 3
Refer to the exhibit.
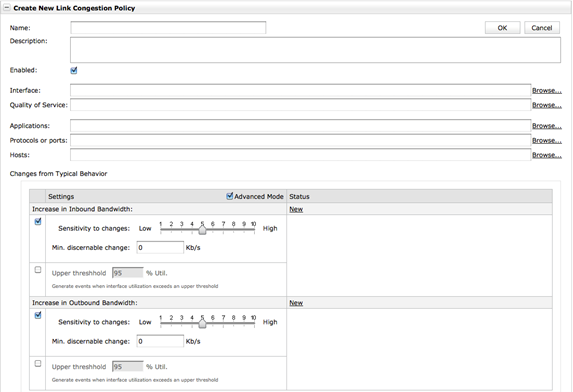
When creating a link congestion policy in Cascade Profiler, what are options that can be selected? (Select 4)
- A. Minimum discerning change
- B. Static upper threshold
- C. Multiple interfaces
- D. One interface
- E. Quality of service
Answer : A,B,D,E
Question 4
If you needed to replicate flow from a router and forward it in its native format to additional flow collectors, which Cascade device would you use?
- A. Sensor
- B. Express
- C. Shark
- D. Gateway
- E. Gateway-VE
Answer : D
Question 5
Which of the following statements are true about NetProfiler Security Profiles? (Choose three.)
- A. A security profile can be created for business hours or weekends or any other time periods you want to specify.
- B. Security Profiles utilize the SNORT Threat Signature Database.
- C. Security Profile data is aged out after one month.
- D. Security Profiles negate the need for IDS/IPS type systems.
- E. The appliance collects traffic data from the monitored network and aggregate it into security profiles.
- F. Recent statistics play a larger role in the profile than older statistics.
Answer : A,E,F
Question 6
The best definition of a Host Scan is:
- A. When one host on the network attaches to a network printer-scanner device and is able to exploit the printer-scanner to download all material scanned on the device.
- B. When one host on the network is infected with malware and the malware scans all of the files resident on the infected system looking for exploits.
- C. When several hosts on the network send a high volume of traffic to a single host to try to exhaust the resources of the host.
- D. When one host on the network send ping packets or other packet types to multiple other devices on the network to determine which hosts are available for further exploit.
Answer : D
Question 7
Which of the following remote user authentications and authorizations are supported by
NetProfiler? (Choose two.)
- A. Kerberos
- B. RADIUS
- C. Diameter
- D. TACACS+
- E. 802.1x
Answer : BD
Question 8
An interactive view within Cascade Pilot is:
- A. A downloadable customized view from the online Cascade community.
- B. Any view that is applied to live devices and dynamically updated.
- C. A view that can be created after drill-down from one view to another.
- D. Any view that was created by applying a traffic filter.
- E. All views within Cascade Pilot are considered interactive views.
Answer : C
Question 9
A list of live interfaces within the Cascade Pilot interface:
- A. Appear listed under the devices tab of the sources panel.
- B. Appear in the main workspace after selecting “choose an interface” from the main menu.
- C. Appear listed under the associated Cascade Shark capture job trace in the sources panel files tab.
- D. Must be selected from the “Capture. Interfaces” menu.
Answer : A
Question 10
How are ToolTips located in the Cascade Pilot user interface?
- A. Through the Reporting ribbon
- B. Through the search bar in the Views pane
- C. By hovering the cursor over the icon that precedes each View listed in the Views pane
- D. Through the Web Interface
Answer : C
Question 11
How can you gracefully reboot the AppResponse Appliance? (Choose two.)
- A. From Desktop Console
- B. Pressing the power button
- C. From Command-Line Interface
- D. From Webui
Answer : CD
Question 12
A logical Grouping of IP addresses in AppResponse is defined as:
- A. Business Groups
- B. Web Applications
- C. Defined Applications
- D. Server Applications
Answer : C
Question 13
What Operating System is required for installation of Cascade Pilot?
- A. Windows Server 2003 or Windows Server 2008
- B. Windows XP, Windows Vista, or Windows 7
- C. Cascade Pilot is not specific to an operating system since access is through any standard web browser.
- D. Any operating system supported by Wireshark
Answer : B
Question 14
Within Cascade Pilot, a sequence diagram is used to:
- A. Show timing and other information at the network or data link layer
- B. Show timing and other information at the application or transport layer
- C. Adjust the length of a trace clip created from a capture job trace
- D. Adjust the length of a trace clip created from a packet capture (pcap) file
- E. C and D
Answer : B
Question 15
What packet filter functions are used in Packet Analyzer?
- A. Shark Filter
- B. BPF (Berkeley Packet Filter)
- C. Wireshark Display Filter
- D. Time Interval
- E. All of the above
Answer : E