Designing for Cisco Internetwork Solutions v1.0
Question 1
You have a campus network that consists of only Cisco devices. You have been tasked to discover the device platforms, the IOS versions, and an IP address of each device to map the network. Which proprietary protocol will assist you with this task?
- A. SNMP
- B. TCP
- C. CDP
- D. ICMP
- E. LLDP C
Answer : Explanation
Explanation:
Question 2
Which three technologies are recommended to be used for WAN connectivity in today's Enterprise Edge designs? (Choose three.)
- A. DWDM
- B. Metro Ethernet
- C. Frame Relay
- D. MPLS VPN
- E. ISDN
- F. DSL
- G. Wireless ABD
Answer : Explanation
Explanation:
There is some discussion about whether ISDN not DWDM should be the answer but it does say TODAYS network
Question 3
WAN backup over the Internet is often used to provide primary connection redundancy. Which is the most important consideration when passing corporate traffic over the public Internet?
- A. security
- B. static versus dynamic routing
- C. bandwidth
- D. QoS
- E. latency A
Answer : Explanation
Explanation:
WAN Backup over the Internet -
Another alternative for WAN backup is to use the Internet as the connectivity transport between sites. However, keep in mind that this type of connection does not support bandwidth guarantees. The enterprise also needs to work closely with the ISP to set up the tunnels and advertise the company's networks internally so that remote offices have reachable IP destinations.
Security is of great importance when you rely on the Internet for network connectivity, so a secure tunnel using IPsec needs to be deployed to protect the data during transport.
Question 4
To provide Layer 2 connectivity between the primary and remote data centers, given that the two data centers are using Layer 3 routed DCIs, which NX-OS technology can be used to facilitate this requirement?
- A. VRF
- B. OTV
- C. MPLS
- D. SPT
- E. VPC B
Answer : Explanation
Explanation:
Question 5
Which WLC interface is dedicated for WLAN client data?
- A. virtual interface
- B. dynamic interface
- C. management interface
- D. AP manager interface
- E. service port interface B
Answer : Explanation
Explanation:
WLC Interface Types -
A WLC has five interface types:
â– Management interface (static, configured at setup, mandatory) is used for in-band management, connectivity to AAA, and Layer 2 discovery and association. â– Service-port interface (static, configured at setup, optional) is used for out-of-band management. It is an optional interface that is statically configured. â– AP manager interface (static, configured at setup, mandatory except for 5508 WLC) is used for Layer 3 discovery and association. It has the source IP address of the AP that is statically configured. â– Dynamic interface (dynamic) is analogous to VLANs and is designated for WLAN client data. â– Virtual interface (static, configured at setup, mandatory) is used for leaver 3 security authentication, DHCP relay support, and mobility management.
Question 6
According to Cisco, which four improvements are the main benefits of the PPDIOO lifecycle approach to network design? (Choose four.)
- A. faster ROI
- B. improved business agility
- C. increased network availability
- D. faster access to applications and services
- E. lower total cost of network ownership
- F. better implementation team engagement BCDE
Answer : Explanation
Explanation:
The PPDIOO life cycle provides four main benefits:
+ It improves business agility by establishing business requirements and technology strategies.
+ It increases network availability by producing a sound network design and validating the network operation.
+ It speeds access to applications and services by improving availability, reliability, security, scalability, and performance.
+ It lowers the total cost of ownership by validating technology requirements and planning for infrastructure changes and resource requirements.
(Reference: Cisco CCDA Official Exam Certification Guide, 3rd Edition) described in the link below. Link: http://www.ciscopress.com/articles/article.asp? p=1608131&seqNum=3
Question 7
DRAG DROP -
The first phase of PPDIOO entails identifying customer requirements. Drag the example on the left to the associated requirement on the right.
Select and Place:
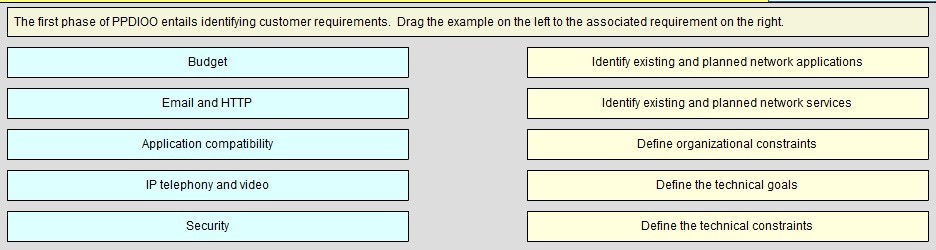
Answer : 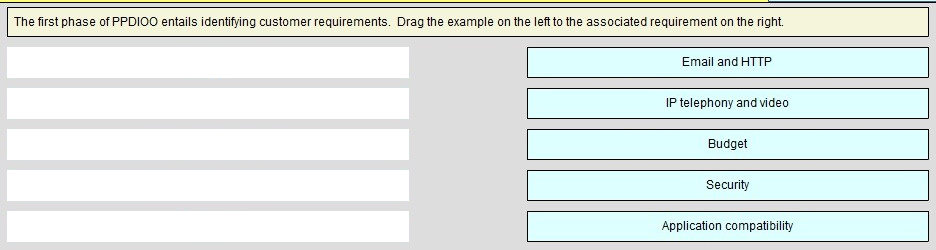
Question 8
During which phase of the PPDIOO model would you conduct interviews with supporting staff to develop and propose a viable solution?
- A. Prepare
- B. Plan
- C. Design
- D. Implement
- E. Operate
- F. Optimize A
Answer : Explanation
Explanation:
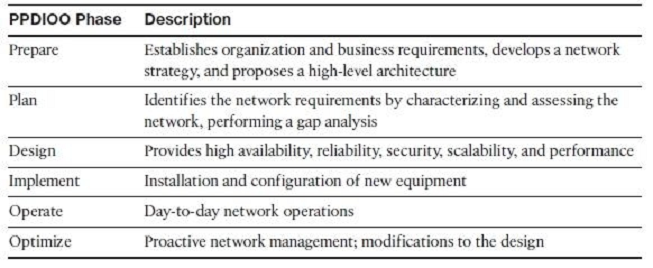
Prepare Phase -
The Prepare phase establishes organization and business requirements, develops a network strategy, and proposes a high-level conceptual architecture to support the strategy. Technologies that support the architecture are identified. This phase creates a business case to establish a financial justification for a network strategy.
Question 9
Which three are considered as technical constraints when identifying network requirements? (Choose three.)
- A. support for legacy applications
- B. bandwidth support for new applications
- C. limited budget allocation
- D. policy limitations
- E. limited support staff to complete assessment
- F. support for existing legacy equipment
- G. limited timeframe to implement ABF
Answer : Explanation
Explanation:
Network design might be constrained by parameters that limit the solution. Legacy applications might still exist that must be supported going forward, and these applications might require a legacy protocol that may limit a design. Technical constraints include the following:
-> Existing wiring does not support new technology.
-> Bandwidth might not support new applications.
-> The network must support exiting legacy equipment.
-> Legacy applications must be supported (application compatibility).
Question 10
DRAG DROP -
Drag the description or characteristic on the left to the appropriate technology or protocol on the right.
Select and Place:
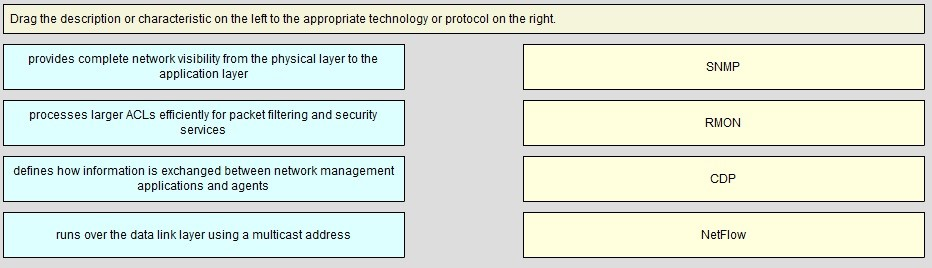
Answer : 
Question 11
DRAG DROP -
Click and drag the phases of the PPDIOO network lifecycle approach on the left to their order on the right.
Select and Place:
Answer : 
Question 12
Characterizing an existing network requires gathering as much information about the network as possible. Which of these choices describes the preferred order for the information-gathering process?
- A. site and network audits, traffic analysis, existing documentation and organizational input
- B. existing documentation and organizational input, site and network audits, traffic analysis
- C. traffic analysis, existing documentation and organizational input, site and network audits
- D. site and network audits, existing documentation and organizational input, traffic analysis B
Answer : Explanation
Explanation:
This section describes the steps necessary to characterize the existing network infrastructure and all sites. This process requires three steps:
Step 1. Gather existing documentation about the network, and query the organization to discover additional information. Organization input, a network audit, and traffic analysis provide the key information you need. (Note that existing documentation may be inaccurate.)
Step 2. Perform a network audit that adds detail to the description of the network. If possible, use traffic-analysis information to augment organizational input when you are describing the applications and protocols used in the network.
Step 3. Based on your network characterization, write a summary report that describes the health of the network. With this information, you can propose hardware and software upgrades to support the network requirements and the organizational requirements.
Question 13
Which three terms describe the primary functions of the distribution layer of the campus network design hierarchy? (Choose three.)
- A. provides end-user connectivity
- B. provides high speed transport
- C. provides QoS services
- D. enforces security policies
- E. provides WAN connections
- F. connects access devices to the core backbone CDF
Answer : Explanation
Explanation:
Link: http://www.cisco.com/en/US/docs/solutions/Enterprise/Campus/campover.html#wp708979
Question 14
Refer to the exhibit.
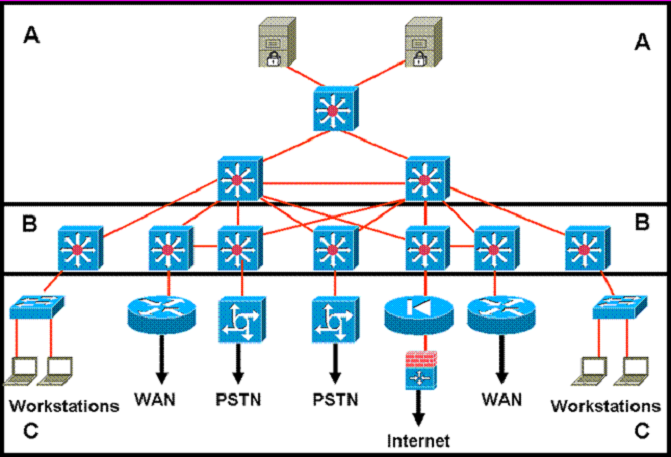
Which statement accurately represents the characteristics of the core layer in this design?
- A. QoS should only be performed only in the core.
- B. Load balancing should never be implemented or used.
- C. Access lists should be used in the core to perform packet manipulation.
- D. Partial mesh should be used as long as it is connected to each device by multiple paths.
- E. Policy-based traffic control should be implemented to enable prioritization and ensure the best performance for all time-critical applications. D
Answer : Explanation
Explanation:
Question 15
Which two of the following are benefits of using a modular approach to network design? (Choose two.)
- A. improves flexibility
- B. facilitates implementation
- C. lowers implementation costs
- D. improves customer participation in the design process AB
Answer : Explanation
Explanation: