Riverbed Certified Solutions Professional - WAN Optimization v8.0
Question 1
You can monitor your Steelhead appliance disk performance using which reports? (Select
2)
- A. Data Store Cost
- B. Data Store Performance
- C. Disk Load
- D. SDR Hit
- E. Disk Pressure
- F. Disk Alarm
Answer : AC
Question 2
A Steelhead Mobile client can be configured to operate in visible or invisible mode (show client in system tray parameter).What part of the configuration is this setting included?
- A. Acceleration policy
- B. Authentication policy
- C. Endpoint policy
- D. Port labels
Answer : C
Question 3
Three Steelhead appliances SH1, SH2, and SH3 are deployed as shown in the exhibit.They are all using the default auto-discovery rule for optimization. However,
CLIENT99 experiences a failure when attempting to access either the HTTP or FTP service on SERVER88.CLIENT99 was able to access these services prior to the deployment of the three Steelhead appliances.
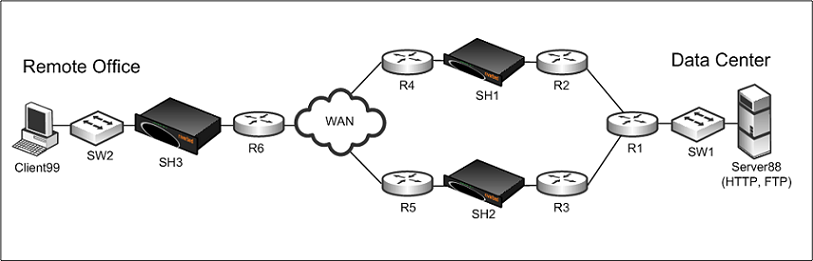
Which of the following choices would most likely correct the problem?
- A. Remove SH2.Use only SH1 and SH3.
- B. Remove SH1.Use only SH2 and SH3.
- C. Turn on Connection Forwarding between SH1 and SH2
- D. Turn on Connection Forwarding between SH1 and SH3
- E. Turn on Connection Forwarding between SH2 and SH3
Answer : C
Question 4
Refer to the exhibit.
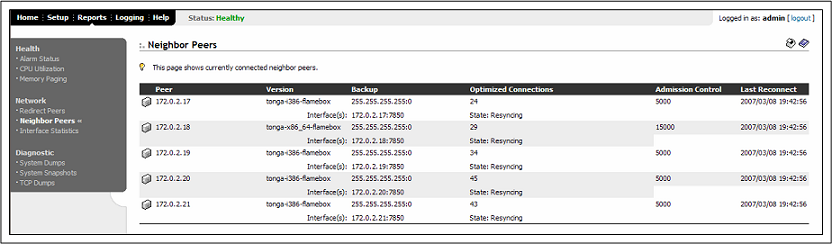
What does the term resyncing mean?
- A. All Interceptor appliances have been connected and the appliances are transferring connection information
- B. All Interceptor appliances and all Steelhead appliances have been connected and the appliances are transferring connection information
- C. The connection has been established and the Interceptor appliance is transferring its state information
- D. The connection has been established and the devices are transferring their state information
Answer : D
Question 5
When configuring SSL optimization for Steelhead Mobile clients, what step must be taken?
- A. Mutual exchange of public keys between the Steelhead Mobile Controller and the server-side Steelhead appliance
- B. Mutual exchange of private keys between the Steelhead Mobile Controller and the server-side Steelhead appliance
- C. Generate a self-signed certificate for the Steelhead Mobile Controller and import that on the client PCs
- D. Import the server's public and private keys to the Steelhead Mobile Controller
- E. Generate individual certificates for each PC and manually import the public key on the Steelhead Mobile Controller
Answer : A
Question 6
One of the Steelhead appliances in your Steelhead appliance cluster is running an older version of RiOS.You decide to schedule a change window to upgrade that Steelhead appliance's imageto the current release.What should you do to ensure that the Steelhead appliance optimization still occurs and the upgraded Steelhead appliance no longer accepts new connections?
- A. Enable the “no in-path accept new” CLI command
- B. Create an in-path rule on the Steelhead appliance to bypass the connections
- C. On the Interceptor appliance, click on “Pause” for that particular Steelhead appliance
- D. Schedule a job on the Steelhead appliance to remove itself from the cluster
- E. All of the above
Answer : C
Question 7
Which of the following are Steelhead Mobile Controller alarms? (Select 2)
- A. Memory paging
- B. Datastore errors
- C. Peer version mismatch
- D. SSL errors
- E. File system full
Answer : AE
Question 8
The Interceptor appliance will attempt to redirect a connection to a Steelhead appliance in the auto pool:
- A. When no user defined Load Balancing rules matches AND peer neighbors are defined
- B. When no user defined Load Balancing rules matches AND no peer neighbors are defined
- C. When no peer Interceptor appliances are defined
- D. When a user-defined Load Balancing rule matches AND a target Steelhead appliance is available
Answer : A
Question 9
The amount of memory required for Steelhead Mobile installation varies between 81 MB to
228 MB.What is the reasons for the variation?
- A. Number of TCP connections
- B. Types of application
- C. Datastore size
- D. Bandwidth
- E. All of the above
Answer : C
Question 10
What are the possible ways to downgrade a Virtual Steelhead appliance after it has been upgraded?
- A. Remove the upgrade license and restart the virtual Steelhead appliance
- B. Reinstall the original model license
- C. Reduce the amount of CPU and RAM allocated to the Virtual Steelhead appliance and it will automatically downgrade at the next startup
- D. It is not possible to downgrade after an upgrade
Answer : D
Question 11
What happens to traffic when a Steelhead appliance reports admission control?
- A. Traffic will be interrupted
- B. The Steelhead stops the interception of new connections for optimization for as long as it is in admission control
- C. This is just a report and the Steelhead will continue to optimize traffic
- D. The Steelhead will start optimizing faster any new connections
- E. The Steelhead will shut down in less than a minute
Answer : B
Question 12
Why should you use promiscuous mode on each in-path virtual NIC for Virtual Steelhead appliance? (Select 2)
- A. For LAN/WAN Virtual NICs to intercept traffic not destined for the virtual machine
- B. This configuration is mandatory for traffic optimization
- C. Promiscuous mode is not required
- D. Only verbose mode should be configured
- E. Only regular mode should be configured
Answer : AB
Question 13
When using SSL, what is the purpose of peer authentication?
- A. Register peers
- B. Confirm the identity of the peer
- C. Establish sessions
- D. Verify the user permissions
- E. Authenticate the client to the server
Answer : B
Question 14
If the VPN concentrator that a Steelhead Mobile client connects to is not in path with a
Steelhead appliance, what changes could be made to the Riverbed infrastructure to allow optimization from the Steelhead Mobile clients?
- A. Enable out-of-path support on server-side Steelhead
- B. Add a fixed-target rule in the Steelhead Mobile Acceleration policy
- C. Enable peering rule in Steelhead Mobile client
- D. B and C
- E. A and B
Answer : E
Question 15
Which of the following is Endpoint alarm?
- A. Locked secure vault
- B. Firewalled status
- C. Network interface error
- D. Temperature
- E. Memory paging
Answer : B