Check Point Certified Security Expert - R80 v1.0
Question 1
What Factor preclude Secure XL Templating?
- A. Source Port Ranges/Encrypted Connections
- B. Simple Groups
- C. ClusterXL in load sharing Mode
- D. CoreXL
Answer : A
Explanation:
There are factors that can preclude templating if all other parameters are met for packet acceleration, such as:
ג€¢ Source port ranges
ג€¢ IPS features not supported in Acceleration
ג€¢ NATג€™d traffic, unless NAT templates are enabled
ג€¢ Encrypted connections
Question 2
In order to get info about assignment (FW, SND) of all CPUs in your SGW, what is the most accurate CLI command?
- A. fw ctl sdstat
- B. fw ctl affinity ג€"l ג€"a ג€"r ג€"v
- C. fw ctl multik stat
- D. cpinfo
Answer : B
Question 3
Check Pont Central Deployment Tool (CDT) communicates with the Security Gateway / Cluster Members over Check Point SIC _____________ .
- A. TCP Port 18190
- B. TCP Port 18209
- C. TCP Port 19009
- D. TCP Port 18191
Answer : D
Question 4
The CPD daemon is a Firewall Kernel Process that does NOT do which of the following?
- A. Secure Internal Communication (SIC)
- B. Restart Daemons if they fail
- C. Transfers messages between Firewall processes
- D. Pulls application monitoring status
Answer : D
Reference:
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk97638
Question 5
What is not a component of Check Point SandBlast?
- A. Threat Emulation
- B. Threat Simulator
- C. Threat Extraction
- D. Threat Cloud
Answer : B
Question 6
Full synchronization between cluster members is handled by Firewall Kernel. Which port is used for this?
- A. UDP port 265
- B. TCP port 265
- C. UDP port 256
- D. TCP port 256
Answer : D
Explanation:
Synchronization works in two modes:
Full Sync transfers all Security Gateway kernel table information from one cluster member to another. It is handled by the fwd daemon using an encrypted TCP connection on port 256.
Delta Sync transfers changes in the kernel tables between cluster members. Delta sync is handled by the Security Gateway kernel using UDP connections on port
8116.
Reference:
https://sc1.checkpoint.com/documents/R80.10/WebAdminGuides/EN/CP_R80.10_ClusterXL_AdminGuide/html_frameset.htm?topic=documents/
R80.10/WebAdminGuides/EN/CP_R80.10_ClusterXL_AdminGuide/7288
Question 7
Fill in the blank: The command ___________ provides the most complete restoration of a R80 configuration.
- A. upgrade_import
- B. cpconfig
- C. fwm dbimport -p <export file>
- D. cpinfo ג€"recover
Answer : A
Question 8
Check Point Management (cpm) is the main management process in that it provides the architecture for a consolidated management console. It empowers the migration from legacy Client-side logic to Server-side logic. The cpm process:
- A. Allow GUI Client and management server to communicate via TCP Port 19001
- B. Allow GUI Client and management server to communicate via TCP Port 18191
- C. Performs database tasks such as creating, deleting, and modifying objects and compiling policy.
- D. Performs database tasks such as creating, deleting, and modifying objects and compiling as well as policy code generation.
Answer : C
Question 9
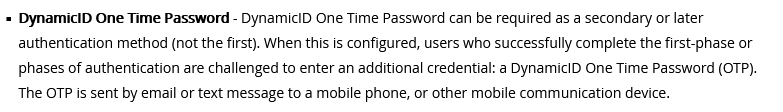
Which of the following type of authentication on Mobile Access can NOT be used as the first authentication method?
- A. Dynamic ID
- B. RADIUS
- C. Username and Password
- D. Certificate
Answer : A
Reference:
https://sc1.checkpoint.com/documents/R80.10/WebAdminGuides/EN/CP_R80.10_MobileAccess_AdminGuide/html_frameset.htm?topic=documents/
R80.10/WebAdminGuides/EN/CP_R80.10_MobileAccess_AdminGuide/41587
Question 10
Which of the SecureXL templates are enabled by default on Security Gateway?
- A. Accept
- B. Drop
- C. NAT
- D. None
Answer : D
Question 11
What happen when IPS profile is set in Detect Only Mode for troubleshooting?
- A. It will generate Geo-Protection traffic
- B. Automatically uploads debugging logs to Check Point Support Center
- C. It will not block malicious traffic
- D. Bypass licenses requirement for Geo-Protection control
Answer : C
Explanation:
It is recommended to enable Detect-Only for Troubleshooting on the profile during the initial installation of IPS. This option overrides any protections that are set to
Prevent so that they will not block any traffic.
During this time you can analyze the alerts that IPS generates to see how IPS will handle network traffic, while avoiding any impact on the flow of traffic.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_IPS_AdminGuide/12750.htm
Question 12
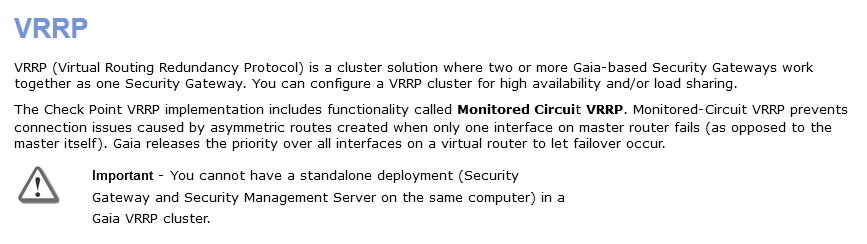
What is true about VRRP implementations?
- A. VRRP membership is enabled in cpconfig
- B. VRRP can be used together with ClusterXL, but with degraded performance
- C. You cannot have a standalone deployment
- D. You cannot have different VRIDs in the same physical network
Answer : C
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/87911.htm
Question 13
The Security Gateway is installed on GAIA R80. The default port for the Web User Interface is ______.
- A. TCP 18211
- B. TCP 257
- C. TCP 4433
- D. TCP 443
Answer : D
Question 14
Fill in the blank: The R80 feature ______ permits blocking specific IP addresses for a specified time period.
- A. Block Port Overflow
- B. Local Interface Spoofing
- C. Suspicious Activity Monitoring
- D. Adaptive Threat Prevention
Answer : C
Explanation:
Suspicious Activity Rules Solution
Suspicious Activity Rules is a utility integrated into SmartView Monitor that is used to modify access privileges upon detection of any suspicious network activity
(for example, several attempts to gain unauthorized access).
The detection of suspicious activity is based on the creation of Suspicious Activity rules. Suspicious Activity rules are Firewall rules that enable the system administrator to instantly block suspicious connections that are not restricted by the currently enforced security policy. These rules, once set (usually with an expiration date), can be applied immediately without the need to perform an Install Policy operation.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_SmartViewMonitor_AdminGuide/17670.htm
Question 15
What is the mechanism behind Threat Extraction?
- A. This a new mechanism which extracts malicious files from a document to use it as a counter-attack against its sender.
- B. This is a new mechanism which is able to collect malicious files out of any kind of file types to destroy it prior to sending it to the intended recipient.
- C. This is a new mechanism to identify the IP address of the sender of malicious codes and put it into the SAM database (Suspicious Activity Monitoring).
- D. Any active contents of a document, such as JavaScripts, macros and links will be removed from the document and forwarded to the intended recipient, which makes this solution very fast.
Answer : D