Check Point Certified Security Administrator v9.0
Question 1
Which of the following methods will provide the most complete backup of an R77 configuration?
- A. Policy Package Management
- B. Copying the directories $FWDIR\conf and $CPDIR\conf to another server
- C. Execute command upgrade_export
- D. Database Revision Control
Answer : C
Question 2
Where can an administrator specify the notification action to be taken by the firewall in the event that available disk space drops below 15%?
- A. SmartView Monitor > Gateway Status > Threshold Settings
- B. SmartView Tracker > Audit Tab > Gateway Counters
- C. SmartView Monitor > Gateway Status > System Information > Thresholds
- D. This can only be monitored by a user-defined script.
Answer : C
Question 3
Where can an administrator configure the notification action in the event of a policy install time change?
- A. SmartView Monitor > Gateways > Thresholds Settings
- B. SmartView Monitor > Gateway Status > System Information > Thresholds
- C. SmartDashboard > Policy Package Manager
- D. SmartDashboard > Security Gateway Object > Advanced Properties Tab
Answer : A
Question 4
You have created a Rule Base for firewall, websydney. Now you are going to create a new policy package with security and address translation rules for a second Gateway. What is
TRUE about the new packages NAT rules?
Exhibit:
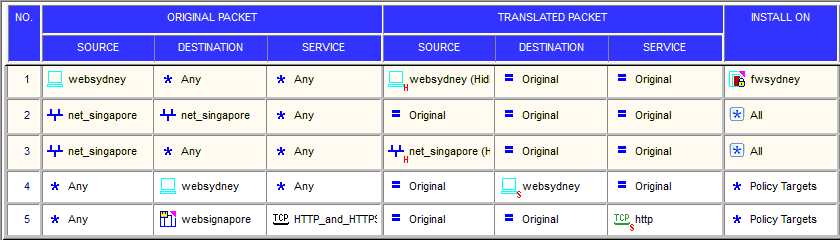
- A. Rules 1, 2, 3 will appear in the new package.
- B. Only rule 1 will appear in the new package.
- C. NAT rules will be empty in the new package.
- D. Rules 4 and 5 will appear in the new package.
Answer : A
Question 5
- A. On a GAiA Security Management Server, this can only be accomplished by configuring the command fw logswitch via the cron utility.
- B. Create a time object, and add 48 hours as the interval. Open the primary Security Management Server objects Logs and Masters window, enable Schedule log switch, and select the Time object.
- C. Create a time object, and add 48 hours as the interval. Open the Security Gateway object's Logs and Masters window, enable Schedule log switch, and select the Time object.
- D. Create a time object, and add 48 hours as the interval. Select that time objects Global Properties > Logs and Masters window, to schedule a logswitch.
Answer : B
Question 6
Which of these Security Policy changes optimize Security Gateway performance?
- A. Using groups within groups in the manual NAT Rule Base.
- B. Use Automatic NAT rules instead of Manual NAT rules whenever possible.
- C. Using domain objects in rules when possible.
- D. Putting the least-used rule at the top of the Rule Base.
Answer : B
Question 7
Which SmartView Tracker selection would most effectively show who installed a Security
Policy blocking all traffic from the corporate network?
- A. Management tab
- B. Custom filter
- C. Network and Endpoint tab
- D. Active tab
Answer : A
Question 8
Your main internal network 10.10.10.0/24 allows all traffic to the Internet using Hide NAT.
You also have a small network 10.10.20.0/24 behind the internal router. You want to configure the kernel to translate the source address only when network 10.10.20.0 tries to access the Internet for HTTP, SMTP, and FTP services. Which of the following configurations will allow this network to access the Internet?
- A. Configure three Manual Static NAT rules for network 10.10.20.0/24, one for each service.
- B. Configure Automatic Static NAT on network 10.10.20.0/24.
- C. Configure one Manual Hide NAT rule for HTTP, FTP, and SMTP services for network 10.10.20.0/24.
- D. Configure Automatic Hide NAT on network 10.10.20.0/24 and then edit the Service column in the NAT Rule Base on the automatic rule.
Answer : C
Question 9
When launching SmartDashboard, what information is required to log into R77?
- A. User Name, Management Server IP, certificate fingerprint file
- B. User Name, Password, Management Server IP
- C. Password, Management Server IP
- D. Password, Management Server IP, LDAP Server IP
Answer : B
Question 10
What is the default setting when you use NAT?
- A. Destination Translated on Server side
- B. Destination Translated on Client side
- C. Source Translated on both sides
- D. Source Translated on Client side
Answer : B
Question 11
After filtering a fw monitor trace by port and IP, a packet is displayed three times; in the i, I, and o inspection points, but not in the O inspection point. Which is the likely source of the issue?
- A. The packet has been sent out through a VPN tunnel unencrypted.
- B. An IPSO ACL has blocked the packet’s outbound passage.
- C. A SmartDefense module has blocked the packet.
- D. It is due to NAT.
Answer : D
Question 12
Which of the following R77 SmartView Tracker views will display a popup warning about performance implications on the Security Gateway?
- A. All Records Query
- B. Account Query
- C. Active Tab
- D. Audit Tab
Answer : C
Question 13
Many companies have defined more than one administrator. To increase security, only one administrator should be able to install a Rule Base on a specific Firewall. How do you configure this?
- A. Define a permission profile in SmartDashboard with read/write privileges, but restrict it to all other firewalls by placing them in the Policy Targets field. Then, an administrator with this permission profile cannot install a policy on any Firewall not listed here.
- B. Put the one administrator in an Administrator group and configure this group in the specific Firewall object in Advanced > Permission to Install.
- C. In the object General Properties representing the specific Firewall, go to the Software Blades product list and select Firewall. Right-click in the menu, select Administrator to Install to define only this administrator.
- D. Right-click on the object representing the specific administrator, and select that Firewall in Policy Targets.
Answer : B
Question 14
You are the Security Administrator for ABC-Corp. A Check Point Firewall is installed and in
- A. /etc/sysconfig/netconf.C
- B. /etc/conf/route.C
- C. /etc/sysconfig/network-scripts/ifcfg-ethx
- D. /etc/sysconfig/network
Answer : A
Question 15
Which of the following statements BEST describes Check Points Hide Network Address
Translation method?
- A. Translates many destination IP addresses into one destination IP address
- B. One-to-one NAT which implements PAT (Port Address Translation) for accomplishing both Source and Destination IP address translation
- C. Translates many source IP addresses into one source IP address
- D. Many-to-one NAT which implements PAT (Port Address Translation) for accomplishing both Source and Destination IP address translation
Answer : C